Power BI Security – What is Dynamic Row-Level Security
FREE Online Courses: Elevate Your Skills, Zero Cost Attached - Enroll Now!
1. Objective
In our previous session, we talked about Power BI Slicer. Here, in this Power BI Security tutorial, we will learn about the introduction of security first then we will move towards aspects of Power BI Security. Moreover, we will discuss row-level security in Power BI.
So, let’s start Power BI Security Tutorial.
2. What is Security in Power BI?
Security is an important aspect of any reporting system. It is critical that users only see data that they are authorized to see. To implement Power BI security, you set up roles and use DAX to enforce data access rules. For example, you can create a role for USA Sales and authorize them to see sales for stores in the United States.
Do you know What are Power BI Admin Roles (Power BI Administration)
3. Power BI Security
One of Power BI’s most useful options is that the easy sharing the reports and dashboards you produce. Understanding the most effective thanks to do this may be a lot of difficult – particularly if you merely need to supply access to a particular user cluster. Otherwise, you solely need to share some of the report information.
For example, a report creator might want to share a report containing sensitive monetary information with the finance team and government leadership solely. Associate 60 minutes specialist may need to share associate 60 minutes report that features elaborated pay info with the 60 minutes team solely. In these cases, access to reports and dashboards ought to solely be created accessible to specific teams or people. On the opposite hand, a report that shows company sales information may be of nice use to sales managers and individual salespeople.
However, maybe {the information|the info|the information} ought to be secured to indicate solely the sales data for the regions or accounts that pertain to the individual viewing the report. Finally, it’d be helpful to share analysis with partners or suppliers that aren’t a part of the organization. Every one of those cases needs a distinct approach to confirm the correct access is being provided to customers of the facility metal artifacts.
Before we glance at the various choices accessible to deal with these situations, it’s vital to know the ideas of access, sharing, and security, as they’re usually confused. This is often graspable, as these ideas are usually employed in conjunction with the event and preparation of Power metal solutions. A few languages in use within the product (row-level Power BI security, for example) will contribute to misunderstandings.
As we have a tendency to dive more, we are going to cowl a way to give access to Power metal artifacts to specific folks in your organization. The way to limit views of knowledge among reports and dashboards to such as users. The implementation would force the employment of some safety features. However, the whole Power BI security model for Power metal is out of scope. For a lot of info on however Microsoft secures Power metal instances, see this documentation.
One easy thanks to rely on access to Power metal dashboards associated reports is to match it to take a flight on a plane. To urge to a destination, an individual can get to have a price tag for that flight. The price tag (along with identification resembling a driver’s license or passport) has the mandatory info for the individual to undergo numerous checkpoints to urge on the flight, and can even have info concerning what kinds of services the rider has access to once on board the flight.
Read about Power Bi and Excel Integration – With Existing Dashboard
This is like the method for a user accessing associate organization’s Power metal service via authentication of username and parole. Once a licensed user has provided the mandatory account info and parole. They’re going to be logged on to the facility metal service that hosts the workspaces, apps, dashboards, and reports for that organization.
Just because an Individual has more established aerodrome security doesn’t mean they need the flexibility to urge on any flight within the airport. The airline price tag is for a particular flight! equally. A company will use permissions to confirm that users United Nations agency have applicable permission to the organization’s Power metal service solely have access to the dashboards and reports that are relevant to their role.
This is often access control… if the user doesn’t have the correct permissions. They can’t access (or even see within the list of accessible reports/dashboards) the content. Power metal report and dashboard authors will outline that structure user teams ought to have content access. Whether or not to grant permissions for report creation collaboration, or entirely for report consumption.
4. FirstClassBuisnessClass.jpg
Now that the individual has boarded the plane they need a price tag for, another side of ticketing comes into play. Looking at the price tag, they may be sitting in first-class, business category, or economy. Thus whereas the individual on the superior price tag might need access to a broader menu of meals, and conveniences. The economy individual may solely have access to a set of these services. Thus, whereas all travellers are on a similar flight, their experiences can be quite totally different. This is often like the employment of role-based security in Power metal dashboards (Power BI Security)and reports.
If role-based Power BI security is employing, a report or dashboard creator will make sure that whereas a bunch of customers of a report or dashboard is all interacting with a similar object. Members of various roles can solely see the information that’s relevant or allowable for members of that role. Managers can appoint to a job that enables them to look at all of the information within the dataset. Whereas individual salespeople may solely have access to their region or customers.
The process for making role-based security is managed by making roles among Power metal desktop. A job uses information among the model to outline access. To Illustrate, to limit sales information to solely sales representatives in a specific region. The space owner would produce a job for every region. Then use a DAX expression to limit the members of that role to the information filtered by that expression.
Do you know How to Add Power BI Filter in Report & Types of Filters
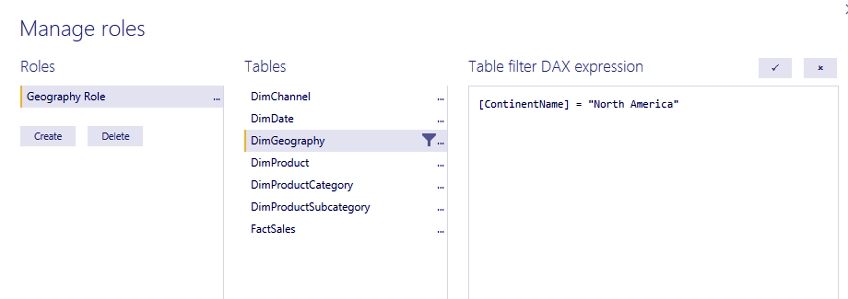
As an associate example, the image below shows making a job that filters the information by North America:
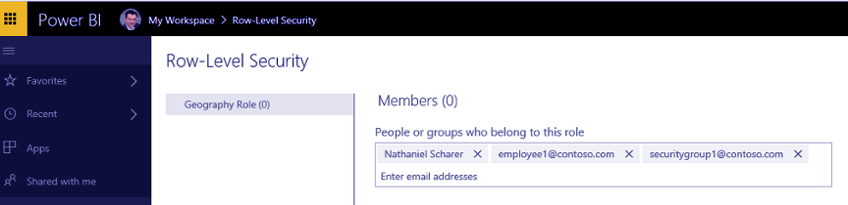
Once the dataset print to the facility metal service. The owner assigns users to the role or roles that were created, as shown below:
While this methodology will cut back the number of reports and dashboards that require to create for a company. It will need careful management to each produces the mandatory roles within the report, and to feature the users and/or teams to the role within the service. Employing a SQL Server Analysis Services Tabular model to standardize the datasets behind your reports. A dashboard is a method to attenuate the work of making and maintaining multiple security roles. It’s as simple as building and sanctionative roles and role filters with the SSAS tabular information supply to use across multiple Power metal reports and dashboards.
Lastly, you’ll use dynamic Power BI security to limit information access. By sanctionative row-level security in Power metal reports, supported a user’s log-in credentials. You set the parameters of what information they see. Continued with our travelling analogy, the employment of dynamic Power BI row-level security is analogous to the data provided to the flight attendants concerning things like special meals. Travellers can be on a similar flight and within the same category and row of seats. However, one may receive a vegetarian meal and therefore the different a gluten-free meal, supported by the data they provided to the airline.
Let’s explore How to Create Power BI Donut Chart
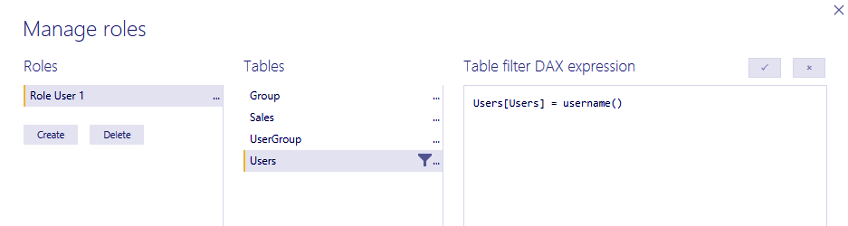
Dynamic row-level security in Power BI accomplishes in Power metal by victimization user tables within the model. Therefore the USERNAME() or USERPRINCIPALNAME() functions within the DAX expression once making security roles. The facility metal service passes the credentials of the user logged into the service. Viewing the report or dashboard to the operation and uses that price to filter the information, as shown below:
Creating the proper level of access and security for your Power metal reports, dashboards, and datasets may difficult. However, it doesn’t need to be! If you have got a matter or need to grasp a lot of concern. However, BlueGranite will facilitate your organization with Power BI security.
So, this was all about Power BI Security. Hope you like our explanation.
5. Conclusion
Hence, in this tutorial, we learned about the Power BI Security aspects. In addition, we discussed an example of Power BI security and Row Level Power BI Security. Still, if have a doubt feel free to ask.
Related Topic- Power BI Query
For reference
Did you know we work 24x7 to provide you best tutorials
Please encourage us - write a review on Google