Master SAP HANA Authorization without Breaking a Sweat!
FREE Online Courses: Click for Success, Learn for Free - Start Now!
Another important concept in SAP HANA security is Authorization. In this tutorial, we will be covering all the aspects of SAP HANA authorization and privileges to understand how security works in SAP HANA.
So, let’s start!
What is SAP HANA Authorization?
SAP HANA authorization is the process of granting access privileges to users using the SAP HANA database. In authorization, a set of privileges are assigned to a user i.e. the user can only perform those operations in SAP HANA or on SAP HANA database that the privileges allow them to.
In this way, users get a decided set of actions that they are allowed to perform while working on SAP HANA and utilizing SAP HANA database from client tools via JDBC/ODBC or HTTP connections.
Whenever the user requests access to the SAP HANA system, the authentication process verifies his identity. Once access into the HANA system is granted, the user starts interacting with the HANA system and database.
To let the user do what he wishes to do, HANA system conducts an authorization check to confirm that the user is having all the required privileges to perform that task.
Once all the required privileges are found under that user, the system check stops and grants permission to the user to perform the task and work on HANA system.
So, every user must have some basic as well advanced (depending on their purpose and requirement) privileges granted to them in order to work on HANA.
| Privilege Type | Applicable to | Target user |
System Privilege | System, Database | Administrators, Developers |
Object Privilege | Database objects (Tables, procedures, schemas, views, etc.) | End users, Technical users |
| Analytic Privilege | Analytic view | End users |
| Package Privilege | Packages present in the classic repository of SAP HANA Database | Application and content developers of SAP HANA classic repository |
Types of Privileges in SAP HANA
In SAP HANA, user privileges divide into several categories and are granted to the users either directly or indirectly (as roles). A role in SAP HANA is a collection of different privileges created to be granted to users.
So, individual privileges can be granted to users directly from the user profile and grouped privileges are granted to a user indirectly i.e. in the form of roles. The ideal way of authorizing users is through roles rather than privileges.
Before we learn more about roles and how to grant roles to users in SAP HANA, let us first learn about the 5 major types of privileges given to users.
1. System Privileges
The system privileges are used to authorize general system activities and administrative tasks for the HANA system.
The user can be authorized with system specific tasks such as creating/deleting schemas, managing user and role (creating/modifying user and roles), monitoring and tracing HANA database, performing data backups, license management, version management, audit management, importing/ exporting content, maintaining delivery units, etc.
In addition to this, basic repository operations are authorized and can be granted as system privileges. System privileges are applied or granted only to the native users of a particular tenant database.
Listed below are all the system privileges supported in SAP HANA:
CREATE SCHEMA | CREDENTIAL ADMIN |
| CREATE STRUCTURED PRIVILEGE | DATA ADMIN |
OPTIMIZER ADMIN | DATABASE ADMIN |
RESOURCE ADMIN | EXPORT |
| ROLE ADMIN | EXTENDED STORAGE ADMIN |
SAVEPOINT ADMIN | IMPORT |
| SCENARIO ADMIN | SSL ADMIN |
SESSION ADMIN | STRUCTUREDPRIVILEGE ADMIN |
INFILE ADMIN | TENANT ADMIN |
| LICENSE ADMIN | TABLE ADMIN |
LOG ADMIN | TRACE ADMIN |
ADAPTER ADMIN | TRUST ADMIN |
| AGENT ADMIN | USER ADMIN |
AUDIT ADMIN | BACKUP ADMIN |
| AUDIT OPERATOR | VERSION ADMIN |
| CATALOG READ | WORKLOAD ADMIN |
CERTIFICATE ADMIN | WORKLOAD ANALYZE ADMIN |
| CREATE R SCRIPT | WORKLOAD CAPTURE ADMIN |
| CREATE REMOTE SOURCE | WORKLOAD REPLAY ADMIN |
2. Object Privileges
Object privileges are assigned to users so that they can view as well as modify database objects. They are also known as SQL privileges as they are a collection of DDL and DML privileges to be applied on database objects.
Authorization can either be provided directly to the database objects such as tables, views, etc. or to the schema containing the objects. Thus, the object privileges are for catalog objects like tables, views, etc. and for non-catalog objects like development objects.
Object privileges used in different scenarios are as follows:
- Object privileges used as source privileges to authorize the access of remote data sources connected to SAP HANA through SAP HANA smart data access.
- Object privileges used to authorize run time database objects.
- Object privileges used to authorize activated repository objects such as calculation views.
- Object privileges used to authorize schema containing an activated repository object.
Given below is the list of object privileges supported by SAP HANA:
- ALL PRIVILEGES
- ALTER
- CREATE ANY
- CREATE VIRTUAL FUNCTION
- CREATE VIRTUAL FUNCTION PACKAGE
- CREATE VIRTUAL TABLE
- CREATE TEMPORARY TABLE
- DEBUG
- DELETE
- DROP
- EXECUTE
- INDEX
- INSERT
- REFERENCES
- SELECT
- SELECT METADATA
- SELECT CDS METADATA
- TRIGGER
- UPDATE
Thus, the object privileges allow a user to perform certain actions like create, insert, drop, delete, select, update, etc on the database objects, data tables, views or schemas. The object privileges granted to users under a particular database are applied to the schemas and objects of only that database.
And, the users who are the owner of the object and owner of the schema, have permission to access an object or schema.
Object Privilege type | Command types | Applies to |
ALL PRIVILEGES | DDL, DML | Tables, Views |
ALTER | DDL | Schemas, Tables, Views, Functions/procedures |
CREATE ANY | DDL | Schemas |
CREATE VIRTUAL FUNCTION | DDL | Remote sources |
CREATE VIRTUAL FUNCTION PACKAGE | DDL | Schemas |
CREATE VIRTUAL TABLE | DDL | Remote sources |
CREATE TEMPORARY TABLE | DDL | Schemas |
DEBUG | DML | Schemas, Calculation views, functions/procedures |
DELETE | DML | Schemas, Tables, Views, Functions/Procedures |
| DROP | DDL | Schemas, Tables, Views, Sequences, Functions/procedure, Remote sources |
| EXECUTE | DML | Schemas, Functions/procedure. |
| INDEX | DDL | Schemas, Tables |
| INSERT | DML | Schemas, Tables, Views |
| REFERENCES | DDL | Schemas, Tables |
| SELECT | DML | Schemas, Tables, Views, Sequences |
| TRIGGER | DDL | Schemas, Tables |
| UPDATE | DML | Schemas, Tables, Views |
3. Analytic Privileges
The analytic privileges are used to grant read-only access to users for information models such as analytic view, attribute view, and calculation view. The analytic privileges authorize information models or views and provide row and column level to the data contained in them.
A user’s analytic privileges are evaluated during query processing and they are given access to view information models accordingly. Analytic privileges restrict the user from seeing only a selected part of the entire information model. There are two types of analytic privileges; XML-based analytic privileges and SQL-based analytic privileges.
4. Package Privileges
The package privileges are used to grant users the permission to access individual packages from SAP HANA Repository. In other words, package privileges allow access to design-time versions of different data models like analytic views, attribute views, and calculation views.
While assigning the privileges to a repository package, you can assign the same package privilege to sub packages as well and decide if the privileges can be passed to other users.
Users require package privileges to be given to them in order to access and modify objects in a particular package in the repository. The package privileges are applied only on the packages available in that database. Some commonly used package privileges on native repository packages are:
- REPO.READ grants read access to the selected packages and design-time objects.
- REPO.EDIT_NATIVE_OBJECTS grants modification privileges to objects (native objects) in a package in the current HANA system.
- REPO.ACTIVATE_NATIVE_OBJECTS grants the privilege to activate or reactivate design-time objects.
- REPO.MAINTAIN_NATIVE_PACKAGES grants the privilege to update or delete a native package and create sub-packages from the main package in the native HANA database system.
- REPO_PACKAGE_ROOT grants the privilege to access and modify all the packages in the repository. This enables the user to access the root package.
5. Application Privileges
Users and clients are given application privileges to access SAP HANA XS applications (created on SAP HANA XS classic applications). The application privileges are either applied directly to users or indirectly via roles.
Also, application privileges granted through roles can be assigned to single users or group of users at a time.
Developers who assign application privileges can decide the extent of access provided to a user i.e. to grant read-only access to general users and administrative and advanced operations access to database administrators.
To grant an application privilege, use the procedure GRANT_APPLICATION_PRIVILEDGE, and to revoke it use the procedure, REVOKE_APPLICATION_PRIVILEGE from the _SYS_REPO schema.
What are Database Roles?
A “Role” in SAP HANA is a collection of different privileges granted as a single unit to a database user or another role in runtime. The standard mechanism of granting privileges in SAP HANA is through Roles.
By using roles instead of granting individual privileges to users, complex authorization concepts can be passed on to users and implemented in HANA system working.
A role essentially contains such collection of privileges using which the database users can perform certain tasks like creating models and reports, reading reports using client tools such as Microsoft Excel, maintaining and operating databases and users, etc.
It is just like using steering, clutch, accelerator, gear stick, breaks together to be able to drive a car.
Role Structure
A role typically comprises of different kinds of privileges such as system privileges, object privileges, analytic privileges, package privileges, and application privileges.
The structure of a role is created when discrete privileges are selected and put together as a role. The role will allow users to perform all the tasks that the privileges within a role grant them.
Authorization in SAP HANA Database Repository
Application developers who develop SAP HANA-based applications use design-time objects stored in HANA’s built-in repository.
The repository contains objects like views, procedures, roles, tables, CDS entities, web content, etc. These objects can be stored, versioned and delivered to the customer from the repository.
The apps are developed using SAP HANA Extended Services (SAP HANA XS) classic model. The repository objects that the developers use are needed to be secured by authorization.
The authorization privileges are granted by the technical user _SYS_REPO via stored procedures. _SYS_REPO owns all the objects stored in the repository and so it grants privileges to other users.
Then, the users can access objects from the repository and use them for application development.
Cross-Database Authorization
In SAP HANA, there is a cross-database access system where users from one tenant database can access data residing in the other. Users from local databases make read-only queries (cross-database SELECT queries) to remote databases.
Users access data or objects such as tables and views from the remote database for cross-database reporting applications. A user from the local database is associated with a user from the remote database.
It is a “remote identity”. Remote identity is essential for a user to be authorized to access data from a remote database.
Cross-database authorization is generally needed for tenant databases. The tenant databases are isolated database systems having their own set of database users and database catalog.
Users from one tenant database might run a query where it references data objects from another (remote) tenant database within a system. Here comes the need to authorize or secure this data transaction between the two databases.
Remote Identities
Here are some important points about remote identities for cross-database authorization:
- Only one user can be a remote identity to a specific user in another database.
- You can use the ALTER USER statement to assign a remote identity to a user.
- The relationship or association between users of two tenant databases is always unidirectional.
Understanding Cross-Database Authorization
To understand this cross-database authorization better, let us suppose that there are two tenant database DFDB1 and DFDB2. USER1 is the user of DFDB1 system and USER2 is the user of DFDB2.
USER2 runs a query which needs to access data table (SCH1.TABLE1) from DFDB1 (remote database).
The SELECT query statement for this will be:
SELECT* FROM DFDB1.SCH1.TABLE1.
Either the administrator of DFDB1 will create a user in DFDB1 which will have a remote identity in DFDB2.
CREATE USER USER1 WITH REMOTE IDENTITY USER2 AT DATABASE DFDB2
Or, the DFDB1 administrator will grant the access privileges required by USER2 to USER1. The USER1 will be authorized to access or read the table SCH1.TABLE1.
GRANT SELECT ON SCH1.TABLE1 TO USER1 [WITH GRANT OPTION]
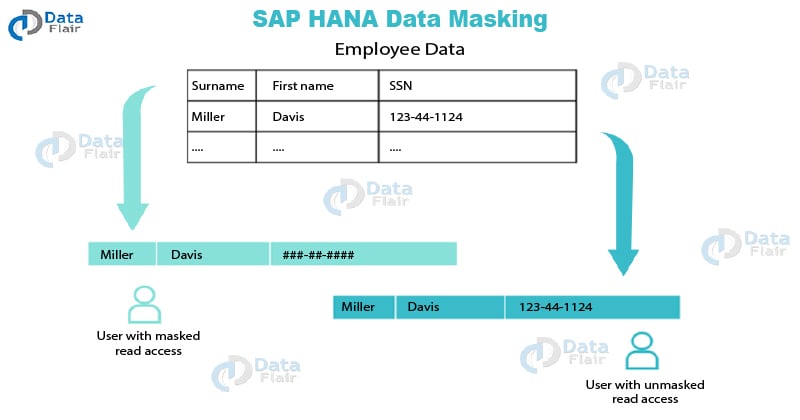
What is Data Masking?
Data masking is an advanced level of data security. It is applied as an additional layer of security on top of authorization processes. In data masking, highly confidential or important data is masked hiding the original data.
Whenever a non-authorized or unprivileged user will see masked data columns, it cannot see the actual data values. Instead, the user will see masked values.
Data masking provides a strong as well as an easy way to secure important data, as it only hides the column values that you don’t want unprivileged users to see and shows other unmasked columns as it is. To understand this better, refer to the image given below.
As shown in the image, an unprivileged user will see ## in place of the actual Social Security Number (SSN) of the employees. Only the user with UNMASKED object privilege for a view can see the original SSN of the employee.
You can apply data masking on columns in views. The column masks hide or disguise all the values present in that column within a view.
LDAP Group Authorization
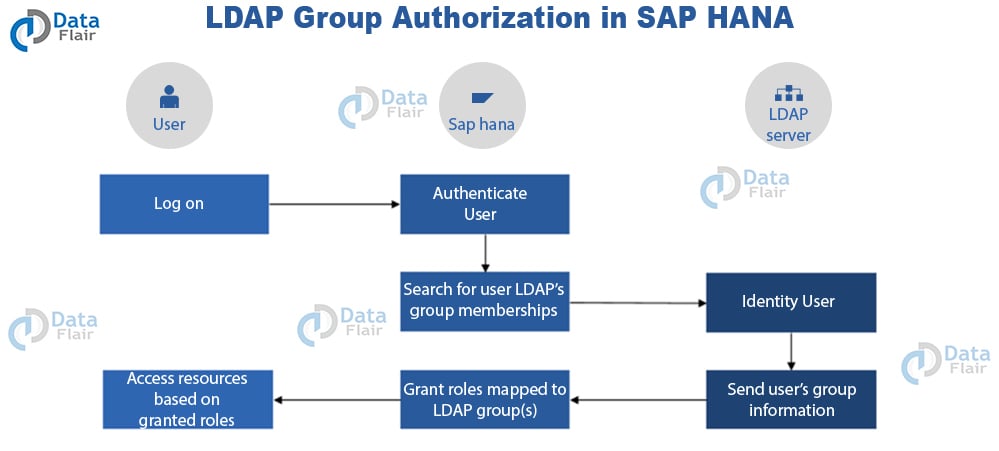
LDAP stands for Lightweight Directory Access Protocol. One uses LDAP as an application protocol to access directory services for SAP HANA. There are LDAP-complaint directory servers using which you can utilize the LDAP group memberships to authorize an SAP HANA user.
Users using directory services via LDAP divides into different groups based on their purpose or role in SAP HANA. By mapping LDAP groups to SAP HANA roles, one can practice LDAP group authorization.
In LDAP group authorization, whenever a user (registered in SAP HANA user directory) logs into SAP HANA, it gets authenticate via the system. After authentication is successful, the system searches for the user’s LDAP group membership.
Once they identify the user as an LDAP group member by the LDAP Server, the group information of the user is sent to SAP HANA. Based on the user information and as per the role mapping to LDAP groups, the system grants roles to the user.
Based on the roles granted, the users get to access the resources from SAP HANA. Thus, this authorizes a user via LDAP grouping to access selected resources or objects from SAP HANA system.
Follow the steps to implement LDAP Group Authorization:
- Firstly, map the LDAP groups to SAP HANA roles.
- Configure the connection with LDAP provider in SAP HANA.
- Lastly, configure SAP HANA users for LDAP Group Authorization
Shared Business Authorizations
The SAP provides a special authorization method for ABAP-based SAP applications like S/4 HANA. It uses Authorization Objects for ABAP apps in SAP NetWeaver Application Server. One can reuse these ABAP authorization objects to give read-only access to SAP HANA users.
The authorization objects grant access privilege to SAP HANA users. Users can access data from ABAP systems. Thus, one can use this method of authorization when they want to replicate the data from an ABAP system into SAP HANA system.
Summary
This was all you need to know about authorization to be able to perform a certain operation on the SAP HANA system. We hope you liked the explanation. If you have any suggestions or queries, leave your comments in the comment section below.
Your opinion matters
Please write your valuable feedback about DataFlair on Google