Salesforce Data Security Model | Salesforce Security
FREE Online Courses: Elevate Skills, Zero Cost. Enroll Now!
1. Objective
Today, in this Salesforce tutorial, we are going to discuss Salesforce Data Security. Moreover, we will see the exact meaning of Data Security in Salesforce. Also, we will discuss the Salesforce Data Security Model and their different layers of Security in Salesforce.
So, let’s start Salesforce Data Security.
2. What is Salesforce Data Security?
Now, in order of providing a security model that satisfies all, different real-world business issues, Salesforce provides a comprehensive and versatile data security model to secure information at totally different levels. Salesforce additionally provides sharing tools to open up and allow secure access to data supported business needs. In this post, we are going to learn how Salesforce Security features work together by taking a real-world scenario. This whole content act as a primer on the Salesforce Data Security Model.
Have a look at Salesforce Schema Builder
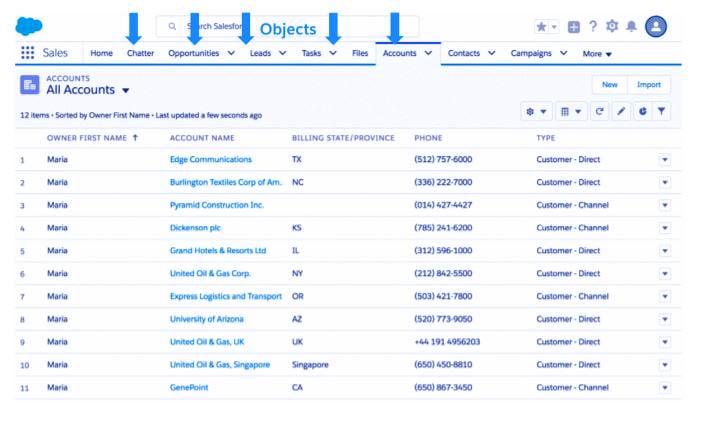
In Salesforce, data is stored in 3 key constructions: objects, fields, and records. Objects are similar to tables in databases. Fields are similar to columns of the table. Records are similar to rows of data within the table. Salesforce seeks the support of object-level, field-level, and record-level security to make the secure access to the object, field, and individual records.
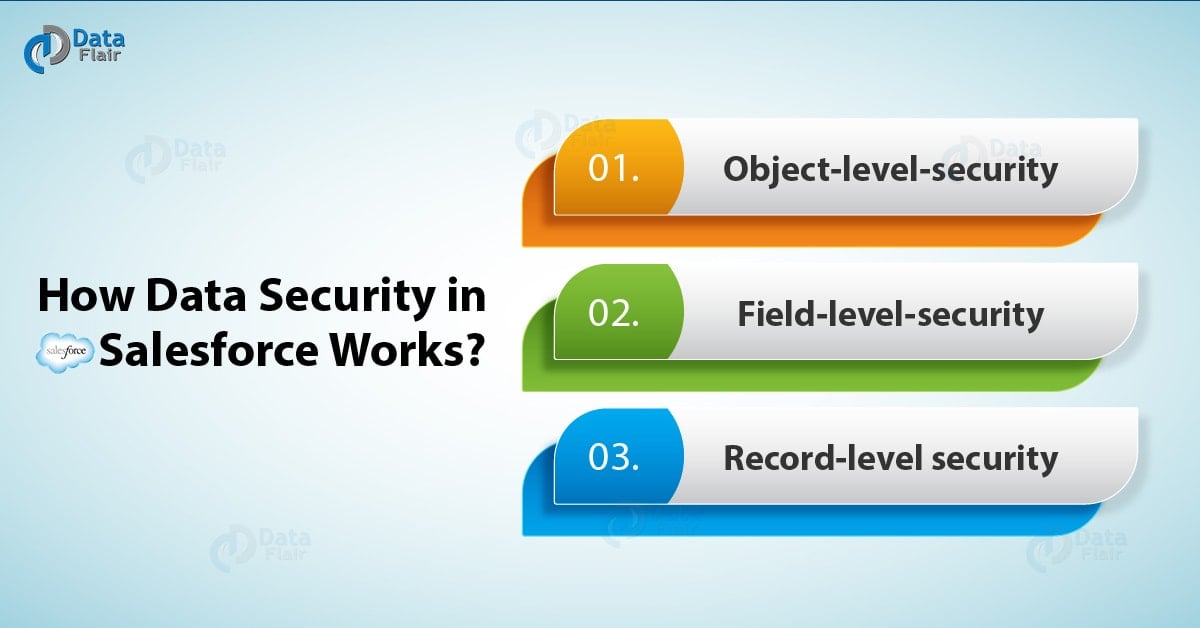
3. How Data Security in Salesforce Works?
Working up of the Salesforce Data security is divided into layers in order to understand this let us assume a scenario.
You must read about Salesforce Services
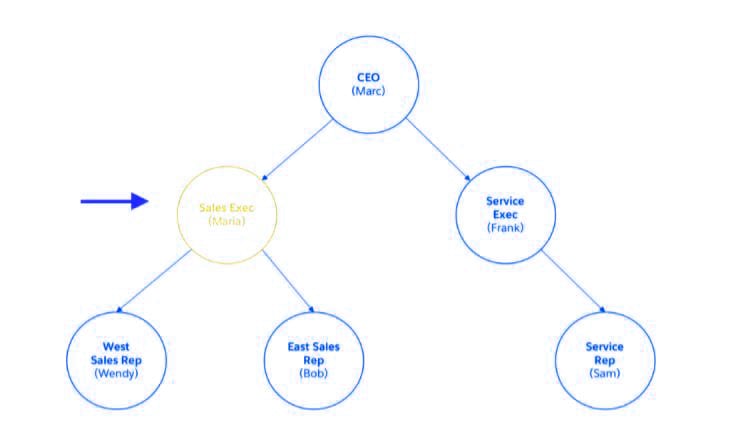
Maria is a working woman. She is an experienced leader who has joined the ABC organization recently. She also has a background in marketing and she reports directly to the CEO of the company.
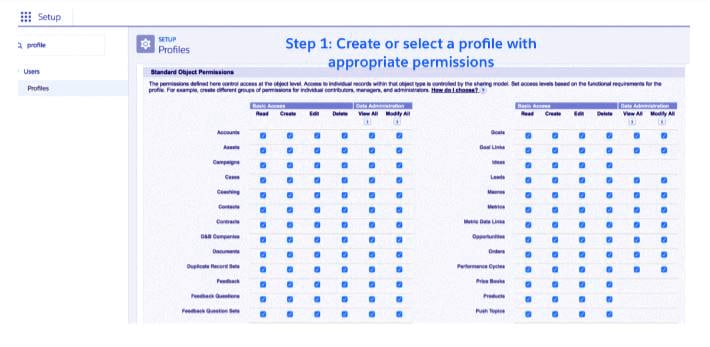
a. Object-level-security
In Salesforce, profiles control access to object-level and field-level security among alternative things like apps, tabs, and so on.
Have a look at Salesforce Environment
Since Maria is a new worker, the associate admin needs to add Maria to the acceptable profile that has access to sales apps and related objects to start giving her access to Salesforce data.
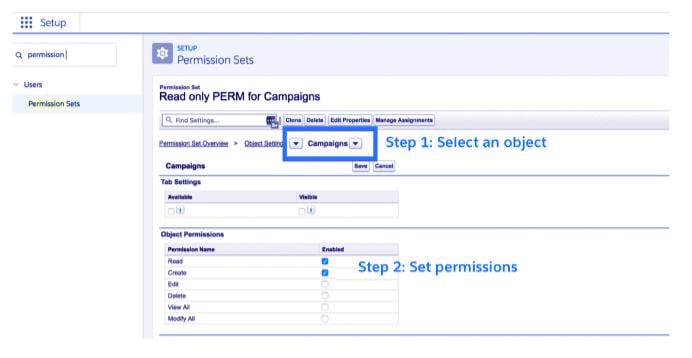
Permission sets in Salesforce Object-Level Security
Since Maria features a marketing background, let’s say she needs to access the Campaigns object to assist with marketing. However, since she is already an important constituent of the sales profile, if an admin adds CRUD (Create, Read, Update, and Delete) to Campaigns, then everyone within the profile is able to access Campaigns. The admin wants to grant permission to access Campaigns just to Maria. this is where permission sets come in. Permission sets are used to provide further (usually special) permissions to users who are already in a profile. In our case, an admin needs to produce a permission set that provides access to the Campaigns object and assign that permission set to Maria.
Do you know how to export data in Salesforce
Notes regarding Salesforce Data Security Permission sets:
- With permission sets, you’ll be able to add and remove permissions to a small set of users at any time.
- You can add multiple permission sets to a given user.
- Use permission sets only when a set of users would like further permissions.
- If tons of individuals in a profile need that permission, then create a custom profile and add permission directly to that profile.
b. Field-level-security
Even if Maria has the freedom to access all the things, it’s not sufficient for her, she still wants access to individual fields of every object. In Salesforce, profiles also control field-level access. An admin will provide scan and write permissions for individual fields. an admin can also set a field to hidden, fully hiding the field to that user.
c. Record-level security
With simply object-level access and field-level access, Maria can solely access records she owns (that is, records created by her). However, if you look at the organization structure, she reports to marc (CEO) and has 2 sales reps (Wendy and Bob) reporting to her.
i. Record-level-security: Organization-wide sharing defaults
In Salesforce, records have a field known as “OwnerId” that points to a true user. owners of records are typically people who created the record and have full CRUD access to it. Salesforce provides alternative ways in which to automatically assign ownership to users and to transfer ownership from one user to a different user.
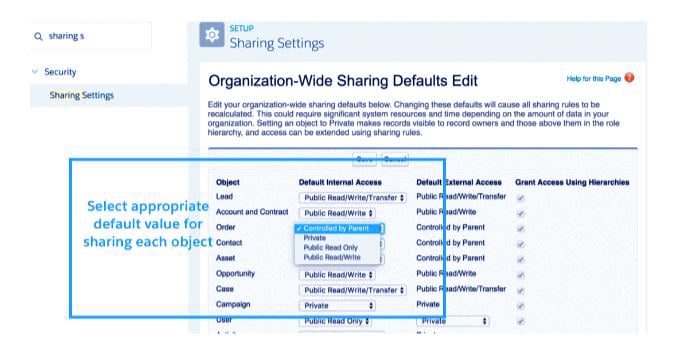
Organization-wide defaults (OWD) control the all the behavior of how each and every record of a given object (for example, Accounts) is going to be accessed by users who don’t own the record.
You must read about Salesforce Architecture
For example:
If OWD for Accounts is private, it suggests that Maria will only see records she is an owner of.
If OWD for Accounts is Read/Write, it means anyone can scan and update (but not delete) the record.
ii. Record-level-security: Role hierarchies
Virtually all companies have an organization structure wherever teams of people report back to their managers and their managers in turn report to their managers, forming a tree-like org chart. So as to simplify sharing, Salesforce provides a straightforward way to share records with managers. To use this sharing rule, an admin should first add the user to a role and grant access.
Let’s revise Salesforce Role Hierarchies
In our case, the admin needs to add Maria to the appropriate role among Maria’s user record.
iii. Record-level-security: Sharing rules
Hierarchy-based sharing solely works for sharing upward and in a vertical direction. What if we want to share laterally? for example, what if we want to share records that Maria owns with her peers within the service govt teams? This is often wherever sharing rules come in. Sharing rules provide a very convenient way to share records laterally and in an ad-hoc fashion via public groups.
iv. Record-level-security: Manual sharing (Classic only)
Record-level-security provides a mechanism to share individual records with others. This whole permission is only granted through the button of Sharing on the record details page, and lets end-users share the individual record with others.
v. Record-level-security: Apex managed sharing
There are occasions when you can’t share records via UI or settings, but you wish to write Apex code to do. For example: If Maria just wants that the record to be shared with a single individual (not roles, roles, and subordinates, public groups), then she has to raise the admins to form an Apex managed sharing rule.
Let’s revise the Salesforce Static Resource
So, this was all in Salesforce Data Security. Hope you like our explanation.
4. Conclusion
In this Salesforce tutorial, we learned what is Salesforce Data security. How Salesforce Data Security works and what are the various levels of security in Salesforce it provides. Also, we discussed the Salesforce Data Security Model. Furthermore, if you have any query, feel free to ask in the comment tab.
See also –
Salesforce Import Data
For reference
Did you like our efforts? If Yes, please give DataFlair 5 Stars on Google