What is SQL Injection (SQLi) | SQL Injection Example
FREE Online Courses: Click, Learn, Succeed, Start Now!
In this tutorial, we will learn about one of the major injection attack used by the hackers i.e. SQL Injection attack. This is one of the most popular web hacking injection protocol.
Here the hacker tries to execute malicious SQL statements on the database to access the hidden data which can corrupt and damage the database and the working of the whole system.
If the hacker succeeds in an injection attack, he gets access to the data which is normally not accessible to them. And they can delete or change it causing abnormal changes in the application.
Let us now dive deep into the concept of SQL injection and understand its causes and preventions.
What is an SQL Injection?
SQL Injection is also known as SQLi. SQLi is the web security vulnerability due to which the application is on the verge of losing private data.
When a hacker can run malicious SQL queries on the database the private data is exposed hence corrupting the application.
This can be done by interacting with the user input fields, using languages or particular special symbols, the most frequent being 1=1 and the ‘or’.
What happens if a SQL Injection is Successful?
When the hacker successfully breaks into the database by running the malicious SQL queries.
Hackers get access to the private database of the application and can corrupt the application which leads to failure of backend services as well.
Researchers have also seen that sometimes the hacker gets control of the backend system of the organization, even the backend stuff.
This leads to the compromise between the services being provided to the users and in some cases, the services remain down for a long period.
Some of the Major SQL Injections
When we talk about Injection attacks in the case of the web, SQL injection attacks top the list.
Some of the major SQL injection attacks are as follows:
1. SQL injection based on 1=1 which the system always evaluates to be True.
Here the hacker uses the fact that a or statement evaluates to true even if one condition evaluates to true. Hence the hacker uses a smart input like “1=1” which always evaluates to true.
For example:
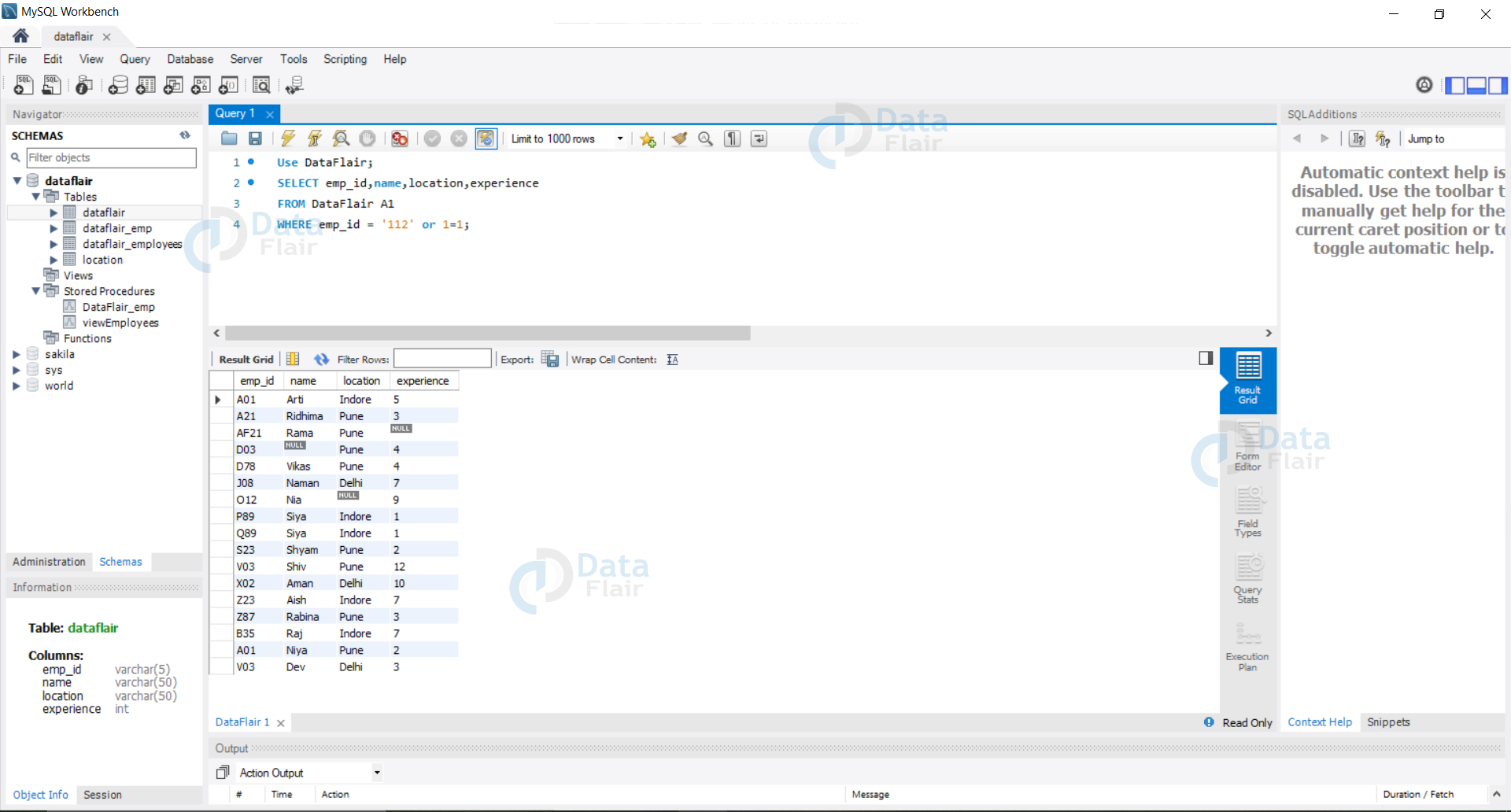
If we have an emp_id column and the hacker wishes to view the database he can use an input like “ emp_id = 112 or 1=1” this will evaluate to the SQL query as follows:
Query:
Use DataFlair; SELECT emp_id,name,location,experience FROM DataFlair A1 WHERE emp_id = '112' or 1=1;
Output:
2. SQL injection based on “=” which the system evaluates to be True always.
In this case, the hacker will manifest the fact that the expression on each side of =, if evaluate to true will return all the results stored in the database.
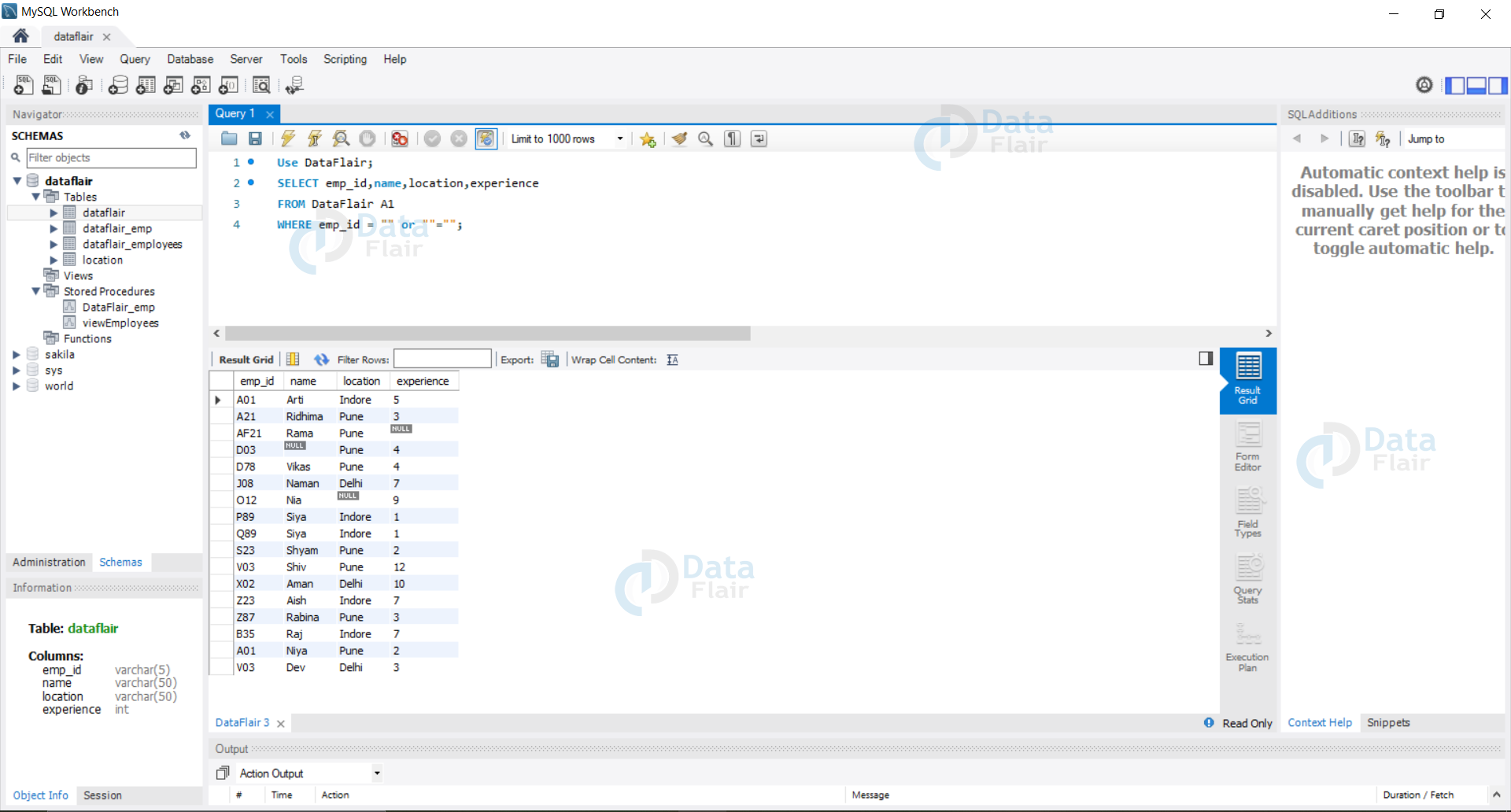
For example, if we have an emp_id field and the hacker inputs- “” or “”=”” this expression evaluates to true and thus returns the whole database data to the hacker.
If we put emp_id = “” or “”=””, then the SQL query which automatically executes at the backend is as follows:
Query:
Use DataFlair; SELECT emp_id,name,location,experience FROM DataFlair A1 WHERE emp_id = "" or ""="";
Output:
3. SQL injection based on batched SQL statements.
If the hacker passes some SQL statement in the input field it is treated as a valid SQL statement and is executed on our database.
For example:
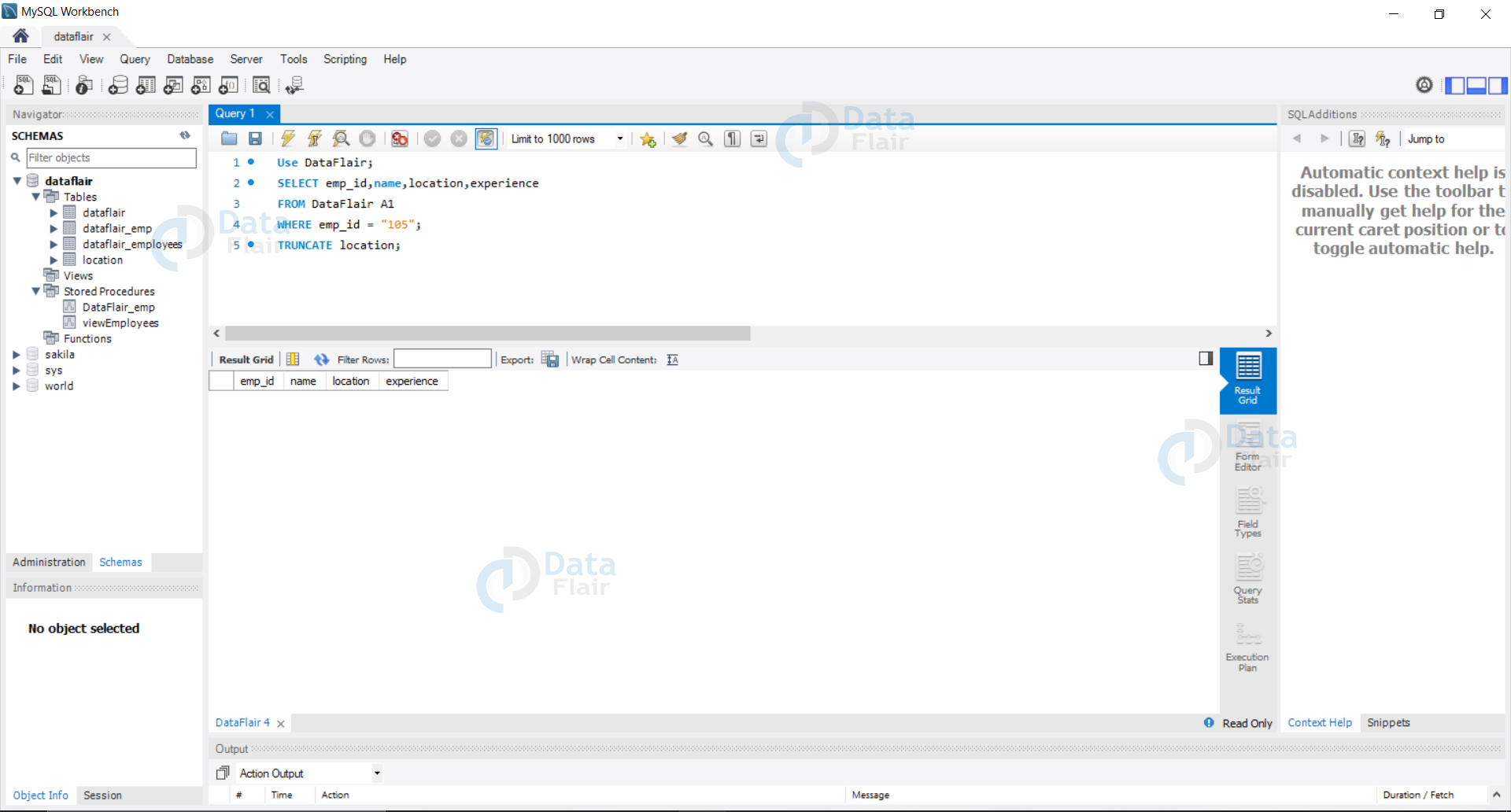
If the hacker inputs the following in the emp_id user field: “118”; TRUNCATE location
In this case, we will lose all the data stored in the location table of our database. The resulting query would be as follows:
Query:
Use DataFlair; SELECT emp_id,name,location,experience FROM DataFlair A1 WHERE emp_id = "105"; TRUNCATE location;
Output:
4. SQL injection to access the hidden data.
Here the hacker accesses the hidden data by using malicious entries into the user input fields.
For Example:
If the hacker inputs some data which is always true into the user field whole application data is exposed.
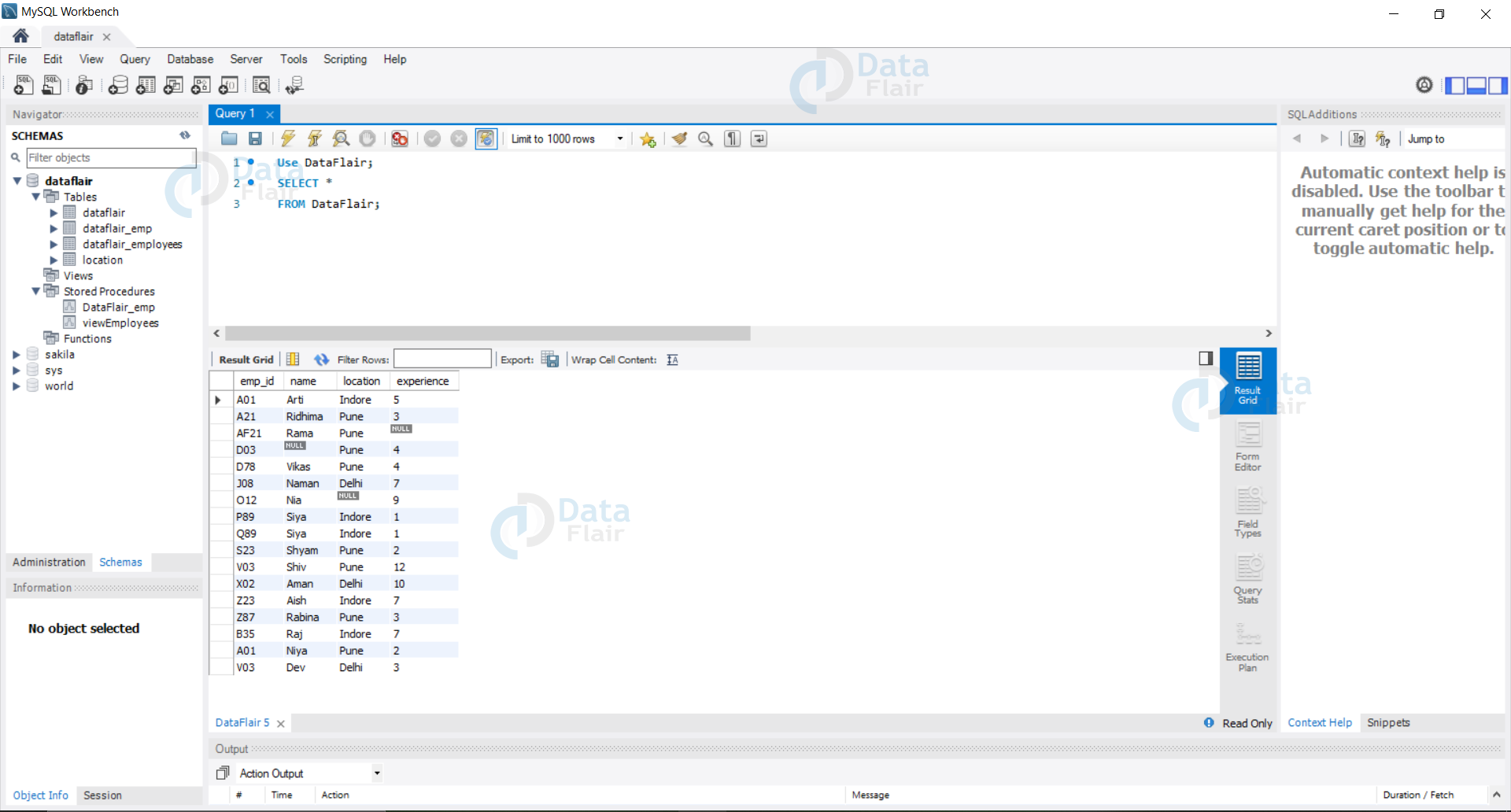
If the user inputs something like ‘*’, in the input field whole data is exposed as the query translates to the following:
Query:
Use DataFlair; SELECT * FROM DataFlair;
Output:
5. SQL injection to alter the application logic.
In this case, the hacker changes the hidden logic or gets access to the backend of the application hence corrupting the application. We can understand this by the following example:
If the hacker inputs a random input in the emp_id input field and a truncate statement then we can lose all the data stored. Hence the logic at the backend would fail.
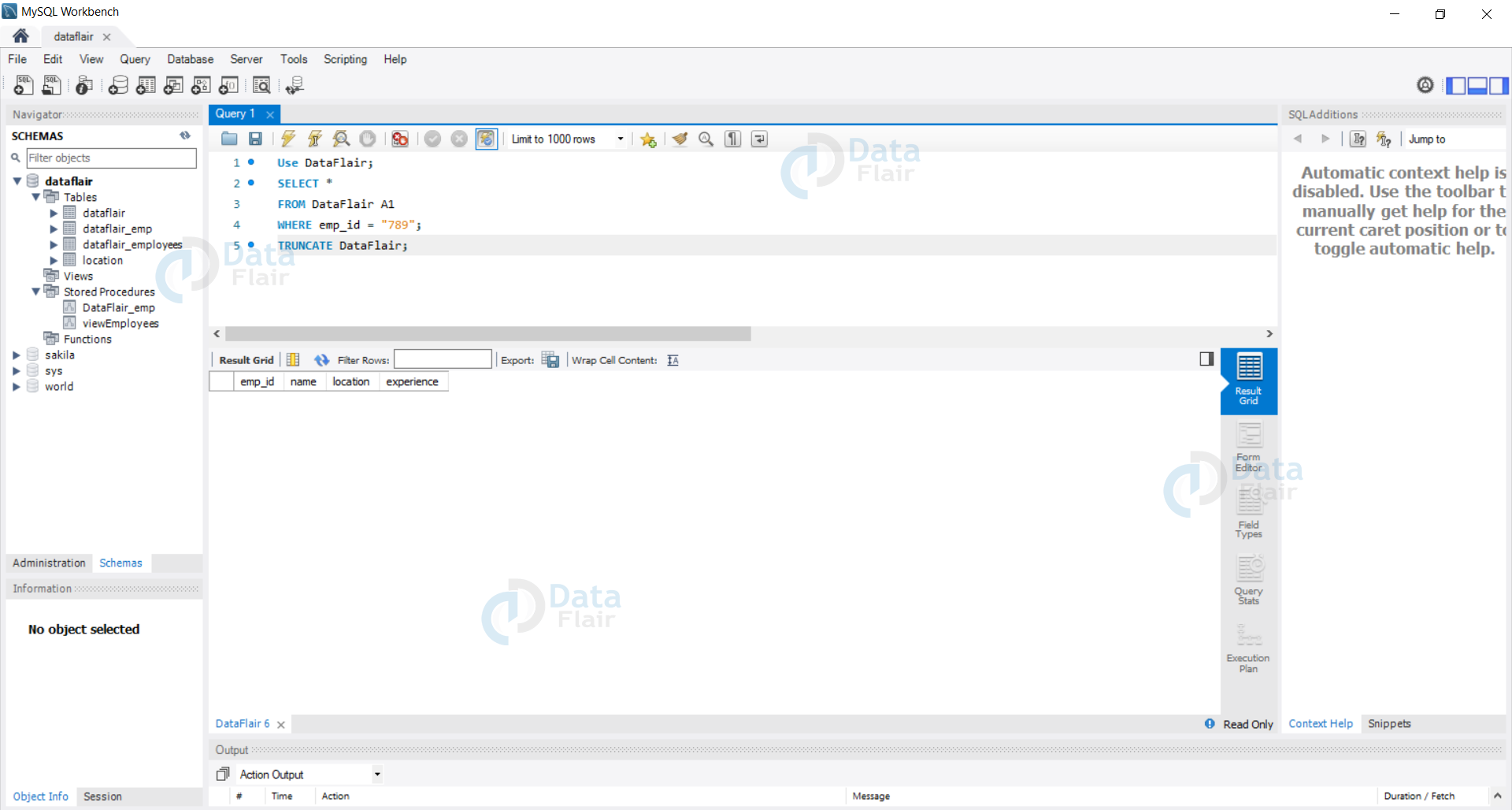
Emp_id = ‘789’ ; TRUNCATE DataFlair
This would translate to the following SQL query-
Query:
Use DataFlair; SELECT * FROM DataFlair A1 WHERE emp_id = "789"; TRUNCATE DataFlair;
Output:
How to Prevent SQL Injections?
Some of the general methods which one can follow to avoid SQL Injection attacks are as follows:
1. The organisation should make aware all the web developers and the backend developers about tips and tricks to avoid SQL injections.
Regular training can help avoid these attacks to a large extent.
2. All the user inputs should be treated as untrusted and should be checked before we run the query on our database.
3. Filter the user input based on the white lists as the hacker always develops the tool to get past the blacklist almost always.
4. The organisations and the hosting units should make sure that the website runs on the latest technologies and uses the latest security certificates to avoid injection attacks.
5. Always implement the tried and tested mechanisms to prevent an attack on the system instead of deploying the system you built from scratch.
6. Last but not least always ensure that the systems are regularly on the monitor for suspicious activity or events.
Summary
In this tutorial, we have seen what is an SQL injection and how it is done. We have then seen the problems one can face due to a successful injection attack.
When the hacker performs an SQLi attack it can lead to the exposure of an internal database which could corrupt the whole application and can even result in breaking the backend logic.
Then we also understood all the tips and tricks by which we can avoid SQLi attacks.
Thus we can say that organizations and individuals should take care while hosting on the web to avoid any possible SQLi attacks which can be done by following required security protocols.
We work very hard to provide you quality material
Could you take 15 seconds and share your happy experience on Google