SSH vs Telnet – Difference Between SSH and Telnet
FREE Online Courses: Your Passport to Excellence - Start Now
In this article, we will compare 2 of the best network protocols – SSH and Telnet. Both of them are very similar when it comes to the facility they provide. But why was SSH even created when Telnet already existed? Is Telnet better than SSH, or is it the other way around? What is the difference between the two?
Well, in this article, we will be answering precisely these. By the end of the article, we will finish comparing SSH and telnets along with their disadvantages and advantages and try to find a winner between the two network protocols.
Before we compare SSH and Telnet, let us start from the basics by discussing what they are.
What is SSH?
SSH is the abbreviation for Secure Socket Shell or Secure Shell. SSH is a protocol to connect to a remote server or system securely. It uses an SSH (a secure protocol)as the data transfers between the client and the host in an encrypted manner.
The prime role of the SSH command in Linux is to manage remote systems. Although usually, this would be another Linux system, it could also be a router, firewall, or even a computer with a different operating system.
In simple terms, the ssh command lets you remotely log in to another system and gives you a terminal that allows you to fully access the remote system as if you were physically in front of the machine.
By definition, SSH is a cryptographic network protocol used for an encrypted connection between a client and a server. There are many SSH clients available for both commercial and free. SSH is so widely used that it is also available on macOS and windows.
What is Telnet?
Telnet is the abbreviation for TErminal NEtwork. Telnet, just like SSH, is also a network protocol that can virtually access a computer and provide two-way communication between 2 machines. In addition, this protocol enables one computer to connect to the local computer.
Telnet follows TCP (Transmission Control Protocol) networking protocol to create remote sessions. ISO gives the TCP protocol for terminal service. Through Telnet, users can log on as regular users with the privileges granted to the specific applications and data on that computer.
Upon successful connection between the local and remote computer, the local computer will display whatever is being performed on the remote computer. The Local computer uses a telnet client program, and the remote computer uses a telnet server program.
The telnet network protocol is mainly used by program developers and those who need to use specific applications or data on a remote machine. Users can also use this Telnet to ping a port to find if it is open.
Terminology
Before we head any further, let us familiarise ourselves with the terminology related to the world around network protocols.
1. Service
Service refers to software running in the background to be used by computers other than the one it is already installed on.
2. Host
Host refers to literally any computer. Computers are called hosts because, technically, a computer can host an application useful to another computer.
3. Local
Local refers to the computer which you or some software are using.
4. Remote
Remote refers to a computer you are physically not in front of.
How does SSH work?
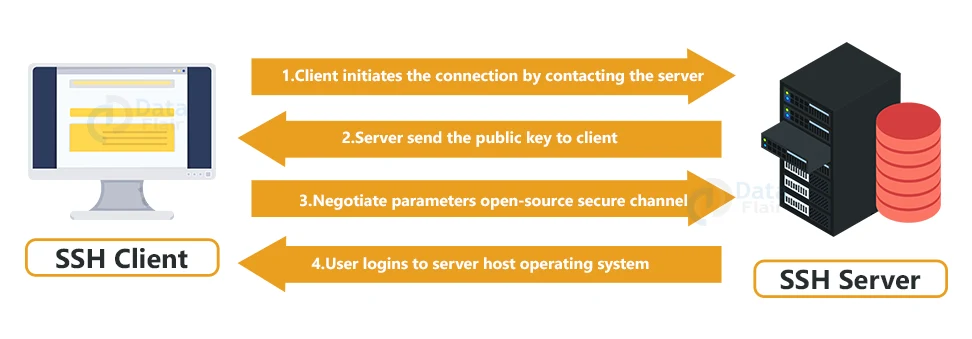
If we want to establish an SSH connection, we need two primary components, a client and a host. The host can be a domain name, IP address, server, and more. The client uses the specified host information to establish the connection. If all the credential provided is verified, an encrypted connection is established.
The host contains an SSH process ready to request the client connection through a TCP or IP port. Immediately when the client initiates a connection, the host responds with the necessary information.
Once the provided information is verified, SSH establishes a new connection for the available environment. Here is a diagram to get a gist of how SSH works:
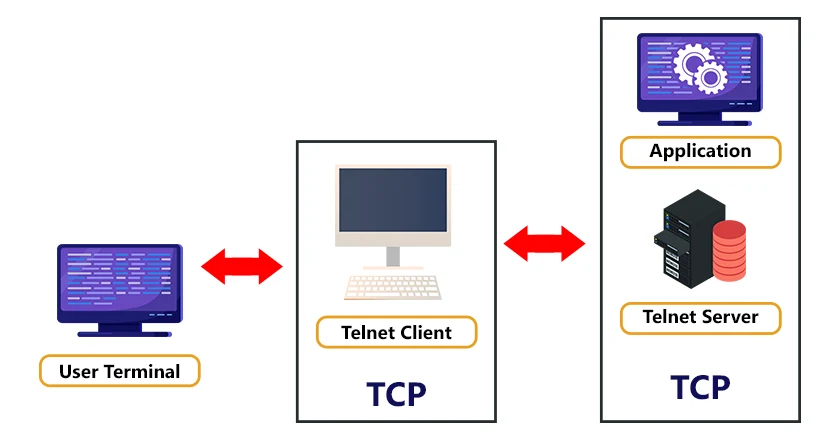
How does Telnet work?
As we say above, Telnet is a client-server protocol that can open a command line on a remote computer (mostly a server). Therefore, the telnet network protocol requires a server application on the remote system you want to manage, and the client application needs to be installed on the local machine.
Telnet works with what is called a virtual terminal connection emulator. Telnet uses Transmission Control Protocol (TCP) and port 23 to connect with a remote system. However, FTP may also be used along with Telnet for users working to send data files.
Commands are sent from the local computer to the remote computer using the Network Virtual Terminal (NVT) format that is received and interpreted by the server and sent to the appropriate application. Here is a diagram to get a gist of how Telnet works:
Few important SSH command
Some important SSH commands include:
1. ls- This command shows the contents of a directory (list the files).
2. cd– This command helps you to change the directory.
3. mkdir– This command helps create a new directory (folder).
4. touch– This command allows you to remove a file.
Few important Telnet command
Some important SSH commands include:
1. Close – This command helps close an existing Telnet connection.
2. Quit – This command is used to exit from Telnet.
3. Timing Mark – This command defines the timing marks.
4. Terminal Type/Speed – This command sets the terminal type and speed.
Advantages of SSH
A few benefits of SSH include the following:
- SSH is available free for non-commercial use.
- It may offer multiple services using the same connection.
- SSH provides privacy of your data through strong encryption.
- SSH authenticates the proof of identity of senders and receivers.
- It allows you to back, forward, or encrypt other TCP-based sessions.
Advantages of Telnet
A few benefits of Telnet include the following:
- Telnet can be used to send and receive information.
- Telnet supports user authentication.
- It enables the collaboration of multiple users.
- You can use it to send and receive information.
- Telnet’s remote login saves your research hours.
Disadvantages of SSH
A few drawbacks of SSH are as follows:
- SSH does not allow you to run GUI tools.
- SSH cannot protect users from attacks made through other protocols.
- This protocol does not protect Trojan horses or viruses.
- SSH cannot fix all TCP’s problems since TCP runs below SSH.
- The SSH protocol is not entirely secure.
Disadvantages of Telnet
A few drawbacks of Telnet are as follows:
- Port numbers can be exploited.
- Dynamic port is not supported.
- Telenet displays only text and numbers, no graphics and colours.
- Telnet does not encrypt any data sent over the connection.
SSH vs Telnet
Now that we have laid down the fundamentals, let us get back to the main motto of this article – SSH vs Telnet. So let us compare them in different aspects:
Security
Telnet does not use any security measures like SSH does when sending data. This makes the data highly vulnerable. This is why using Telnet on private, trusted networks is recommended.
On the other hand, SSH is all about security – so secure that it is written in its name. In addition, SSH uses Key pair authentication, where public and private keys are generated. This makes it extremely difficult to decrypt and read the exchanged data.
Authentication
Telnet does not use any authentication protocols or mechanisms when establishing a connection between 2 systems.
On the other hand, SSH uses key pair authentication, where the Private key remains with the client, and the public key is sent to the server. The two systems can establish a secure connection if and only if both the keys match – by comparing the private key to the public key.
Data Formats
Telnet uses Network Virtual Terminal (NVT) format and transfers the data as plain text.
SSH uses an encrypted format and a secure connection to transfer the data between the two systems.
To sum up, here is a table differentiation between the two network protocols:
| TELNET | SSH |
| Telnet uses port 23, which was designed specifically for LAN. | By default, SSH runs on port 22. You can later change it if you wish. |
| No privileges are provided for the user’s authentication. | Key pair authentication is provided for the user’s authentication. |
| Best suited for Private networks. | Best situated for public networks. |
| Telnet transfers the data in plain text. | SSH encrypts the data shared between the 2 systems. |
| Requires low bandwidth usage. | Requires high bandwidth usage. |
| Vulnerable to security attacks. | Protects data from security attacks. |
| Used in Linux and Windows. | Used in most Operating systems. |
| Data sent using telnet cannot be easily interpreted by hackers. | Passwords and Usernames can be prone to malicious attacks. |
We can see that there is no winner; both are similar yet very different. Each network protocol has its own pros and cons. However, we can still discuss under what scenarios we can use each network protocol to make the best out of them.
When do you use SSH?
Since SSH is way more secure than Telnet and offers more functionality than Telnet (secure file transfer and port forwarding), you can use SSH whenever you want to connect to a remote system over the Internet.
When do you use Telnet?
The only drawback of Telnet is that it is not as secure as SSH. Nonetheless, it is a star performer in private connections – in private connections, Telnet can perform even better than SSH. Therefore, it is recommended to use Telnet in the following Scenarios:
1. In trusted networks like LANs that are not connected to the Internet.
2. When devices don’t support SSH protocol.
Summary
The only drawback of Telnet is its security. Otherwise, both SSH and Telnet are of equal calibre. In this article, you have learned various topics on SSH and Telnet, like what they are, how they work, a few essential commands, and advantages and disadvantages. We have also compared both SSH and Telnet under various aspects and figured out the best scenarios to use each.
Did we exceed your expectations?
If Yes, share your valuable feedback on Google