SSH Key in Linux
FREE Online Courses: Click for Success, Learn for Free - Start Now!
In this article, you will learn what an SSH key is, and what its uses are. You will also learn how to set up and configure the SSH key in Linux.
What is SSH key?
SSH stands for secure shell. An SSH key is a utility for creating new authentication key pairs for SSH. It is an encrypted protocol that communicates and administers with servers.
SSH keys offer an especially secure manner of logging into your server. The key pairs that SSH creates are for automating logins, single sign-on, and for authenticating hosts.
SSH public key is dependent on asymmetric cryptographic algorithms (like RSA algorithm) that generate a pair of separate keys. One of the 2 keys is a private key and the other key is a public key. You keep the private key secret and store it in the computer you use to connect. You can share the public key without compromising the private key.
SSH keys are an access credential that is used in the SSH protocol, and they are foundational to modern infrastructure service platforms like AWS, Microsoft Azure, google cloud, and many more.
SSH keys come in many sizes, but the most used and selected one is an RSA 2048-bit encryption. It is comparable to a 617 digit long password!
What is an RSA algorithm?
Before we see how SSH keys work, let us look at how the RSA algorithm work to provide a better understanding of cryptography and keys.
The RSA algorithm is called so after the names of its creator – Rivest, Shamir, and Adleman. The RSA system has 2 keys, unlike the Caesar cipher which has only 1. The 2 keys produced are the Public key and the Private key. The public key helps encrypt messages, whereas the private key helps in decrypting a message.
Before I explain the working of the RSA algorithm I would like to give a moment to a beautiful quote by William Stanley Jevons:
“Can the reader say what 2 numbers when multiplied together will produce the number 8,616,460,799? I think it is unlike;y that anyone but myself will ever know. ”
We know today that it is the product of 2 prime numbers 89,681 and 96,079. The reason why he made such a big claim is that it is difficult to find the factor of a very large number, and even harder when the numbers are prime! So that is why the key work on this principle. The RSA encryption relies on factors and large prime numbers.
Let us take an example.
If you ask the question, what is 31 * 37? It is an easy question for which the answer is 1147
But if you ask the question, what are the factors of 1147? This question is much harder to solve compared to the previous question. You will start dividing it by all the numbers until eventually, you find 1 factor.
Now let us see the steps involved in the RSA algorithm
1. Choose any two very large prime numbers, p, and q.
2. Let N = p * q
3. Find Euler’s phi functions p and g and multiply them,
T = φ(p) * φ(q)
4. Choose 2 numbers e and d such that (e * d) mod T = 1
5. The public key will be N and e
6. The private key will be N and d (keep as secret)
Let us create a simple key using above steps:
1. p = 2, q = 7 (chose small prime numbers for simplicity)
2. N = 2 * 7 = 14
3. T = φ (2) * φ(7) = 1 * 6 = 6
4. Choose (e * d) mod 6 = 1
We can divide this step into further steps,
Where 1 < e < φ(n) and φ(n) e are co prime
So we chose from 1 to 6 such that gcd (e, T) = 1
On working out we get e as 5
Now we can calculate d by :
d = e-1 mod T
⇒ ed = 1 mod T
⇒ ed mod T = 1
⇒ 5 * d mod 6 = 1
⇒ 5 * 11 mod 6 = 1
On working out we get d as 11
Therefore, e = 5 and d = 11
Step5. Public Key = (e, N) = (5, 14)
Step6. Private Key = (d, N) = (11, 14)
Now that we have a public key and private key let us encrypt the letter “B”. Instead of using ASCII values, let i\us keep it simple and use normal numbers: A is 1, B is 2, C is 3, D is 4, E is 5 and so on.
The Encryption value is given by: plain text ^ e (mod N), in our case:
C (cipher text) = 25(mod 14) = 32 mod 14 = 4
Therefore B is encrypted to D
Let us also see how to decrypt the message:
Decrypted value = cipher text ^ d (mod N), in our case:
Private key = (11, 14)
Secret message = “D”
P (plain text) = 411(mod 14) = 4,194,304 mod 14 = 2 (approx)
Therefore “D” is decrypted to “B”
So that is how we encrypt and decrypt messages using the private key and public key in the RSA algorithm.
Similarly, SSH keys always come in pairs. Every RSA key pair consists of a private key and a public key. Who possesses the keys determines the type of SSH key pairs.
If both the private key and public key remain with the user, the set of keys is user keys. If both the keys are on a remote system, this keyset is the host keys
How do user keys work?
The user key is one of the most commonly used keysets. The private key is stored in the system, being used to access the remote system. It is used to decrypt information that is exchanged in the SSH protocol.
To sum up, the RSA algorithm is an algorithm that is based on the difficulty of factoring really large prime numbers. All SSH clients support this algorithm.
How do SSH keys work?
The SSH server can authenticate clients using a variety of different methods. The most simple of them all is password authentication which is not very secure. Even though passwords are sent to the server in a secure manner, passwords are not generally complex or long enough to be resistant to repeated attacks. With the current technology, brute-forcing a password-protected account is very much possible.
This is where keys come to the rescue. SSH key pairs, as you saw are 2 cryptographically secure keys that can authenticate a client to an SSH server. Each key pair consists of a private key and a public key.
What is the private key meant for?
The private key is kept by the clients. It must be kept absolutely secret because any compromise of the private key will allow the attacker to log into servers that are configured with the associated public key without further authentication. This is why the private key must always be encrypted on a disk with a passphrase.
What is the public key meant for?
The public key, on the other hand, can be shared freely. This is so because the public key can encrypt messages that only the private key can decrypt. The public key is uploaded to a remote server that you want to be able to log in with SSH. It is added to a special file within the user account you will be logging into: “~/.ssh/authorized_keys”
How to configure SSH Key-based authentication?
Step 1: Generate SSH keys
The first step to configuring SSH key authentication is to generate an SSH key pair on your local computer.
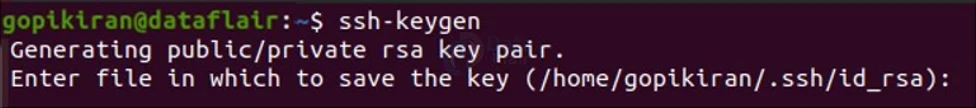
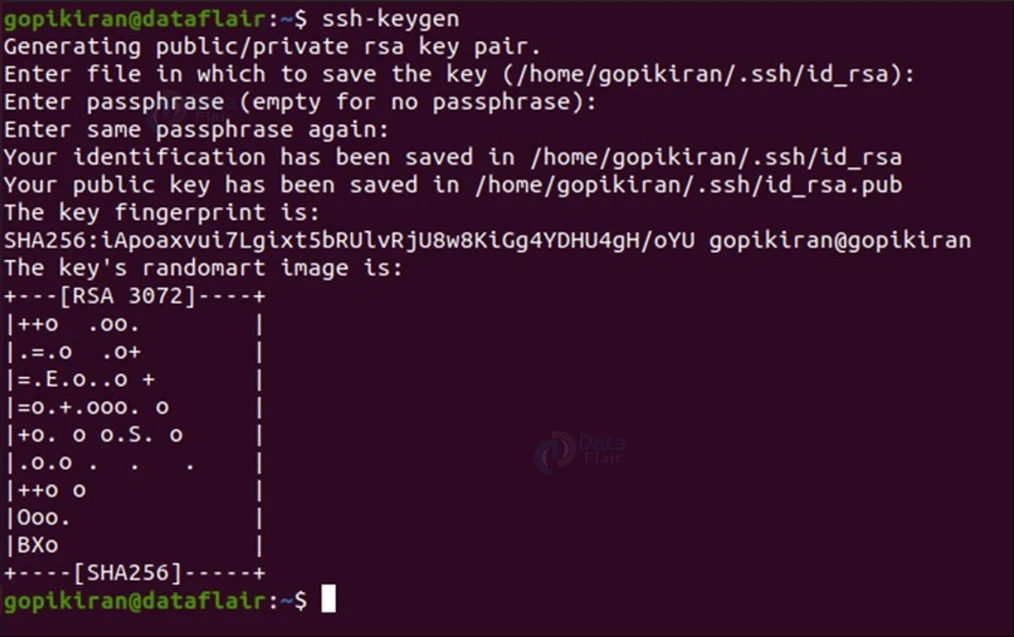
To do this, we use the special utility called ssh-keygen. By default, this will create a 3072 bit RSA key pair:
It will prompt you to select a location for the keys to be generated. By default, the system will store the keys in the ~/.ssh directory. “Id_rsa” is sn
the name of the private key, and “id_rsa.pub” is the name of the public key
Stick to the default location as your SSH client will automatically find your SSH keys while authenticating.
On pressing enter, it will prompt you to enter a passphrase twice (once to enter and 2nd to confirm). If at all you don’t want to set a passphrase, you can press enter and bypass this prompt.
Now have a public and private key that you use to authenticate. The next step is to place your public key on your server so that you can use SSH key authentication to log in.
Step 2: Copying the SSH public key to your server
The easiest method to copy your public key to an existing server is to use the command: “ssh-copy-id”
For this command to work, you must currently have password-based SSH access to your server. You can copy toys Public key to your server using the syntax:
ssh-copy-id username@remote user
When you are doing this for the first time, that is connecting to a new host, you will get a message saying, that it cannot establish the authenticity of the host. Ignore this and press ‘y’ for connecting. The system will ask for the remote user’s password.
If the connection was a success, it will prompt you to try logging into the remote user machine and check if only the public key has been added.
Step 3: Authenticate to your server
If you have successfully completed the procedure above, you can now log into the remote host without their password. To do so type in the command using the following syntax:
ssh username@remotehost
Again, if it is your first time, you will get a message saying that it cannot establish the authenticity of the host. Ignore it and pre ‘y’ to connect.
If at all you bypassed entering the passphrase in step – 1, you will be logged in immediately. If at all you supplied a passphrase for the private key, you must enter it to log into the remote user. And if the connection was successful, a new shell session will be created with the account on the remote system
Step 4: Disabling password authentication on your server
If you were able to log into the remote user, it means that you have successfully configured your SSH keys. Yet, your password-based authentication mechanism is still active, which makes your system vulnerable to brute force attacks.
To turn off the password authentication, log into your remote server with SSH keys and open the SSH daemon’s configuration file. (if you are not root, give sudo privileges.):
Sudo nano /etc/ssh/sshd_config
Inside the file, search for the directive called “PasswordAuthentication”. This directive is already commented out in the file, uncomment it by removing the ‘#’ in front of it and set the value to ‘no’. Doing so will disable your ability to log in through SSH using passwords.
The final step is to save and close the file, to do this you can simply restart your computer.
And voila! You now have SSH key-based authentication configured and running on your server, allowing you to sign in without providing an account password.
How to protect your SSH keys?
Now that you have created your SSH keys, you must also protect them. As told earlier, the private key is extremely important and must remain a secret always, else anyone can hack into your server. Here are some ways to ensure that you protect your SSH keys.
1. Never share your private key with anybody
2. Restrict privileges of the account
3. Use a very strong passphrase
4. Never store your private key on insecure storage.
Summary
As you have seen SSH is a very powerful encrypted protocol to communicate and administer with servers with the help of SSH keys (public and private keys). You have learned the use of SSH and how it works. You have gotten a good idea of what the RSA algorithm is and how to generate the keys. Last but not least, you have also seen how to set up and configure your own SSH key-based authentication.
Your 15 seconds will encourage us to work even harder
Please share your happy experience on Google