SSH Command in Linux
FREE Online Courses: Your Passport to Excellence - Start Now
In this article you will learn all there is to the SSH command and tool in Linux-based operating system. We will go straight from the fundamentals like what SSH is, terminology, uses of SSH, How SSH works, and the components of SSH to technical stuff like installing SSH, options used with SSH, generating keys with SSH and so many more. So buckle up and read till the end!
What is SSH in Linux?
SSH is the abbreviation for Secure Socket Shell or Secure Shell. SSH is a protocol used to connect to a remote server or system securely. It uses an SSH protocol (a secure protocol)as the data transfers between the client and the host takes place in an encrypted manner.
The prime role of the SSH command in Linux is to manage remote systems. Normally, this would be another Linux system, it could also be a router, firewall, or even a computer with a different operating system.
In simple terms, the ssh command lets you remotely log in to another system and gives you a terminal that allows you to fully access the remote system as if you were physically in front of the machine.
By definition, SSH is a cryptographic network protocol used for an encrypted connection between a client and a server. There are a number of SSH clients available for both commercial and free. SSH is so widely used, that apart from Linux, it is also available on macOS and windows.
What is the use of Linux SSH Command?
As I mentioned earlier, SSH is used to remotely log in to another system, and it lets you control the system as if you are physically present there. This feature is a god-sent boon for some people.
The reality of managing innumerable remote systems without ven getting up from your chair is nothing but a dream for Linux administrators, or even ordinary users having multiple systems in different locations.
SSH can also create port forwarding tunnels, successfully encrypting and securing connections made through any type of application or program on your Linux system.
SSH Terminologies
Before we head any further, let us familiarize ourselves with the terminology that is related to the world around SSH.
1. Service
Service refers to software that runs in the background so that it can be used by computers other than the one it is already installed on.
2. Host
Host refers to literally any computer. Computers are called hosts because technically a computer can host an application that is useful to some other computer.
3. Local
Local refers to the computer which you or some software is using.
4. Remote
Remote refers to a computer you are physically not in front of.
How does SSH work?
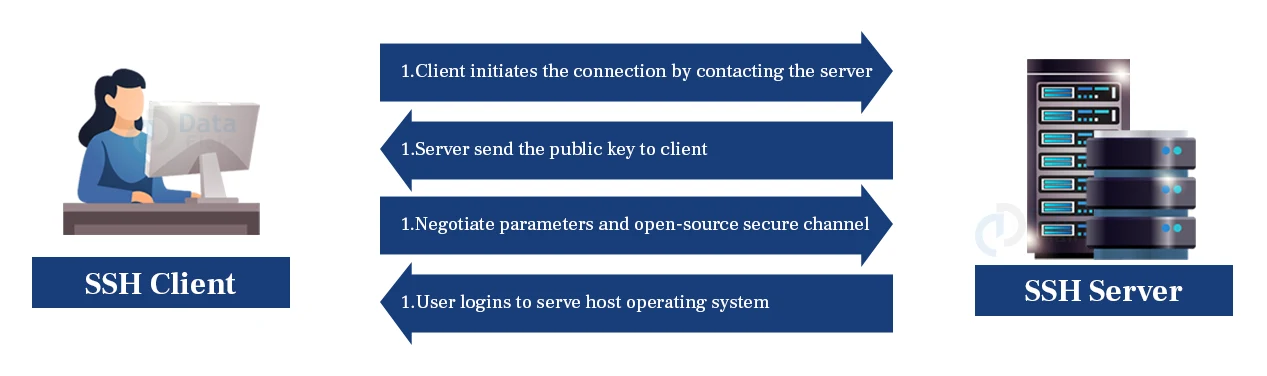
If we want to establish an SSH connection, we need two primary components, a client and a host. The host can be a domain name, IP address, server, and more. The client uses the specified host information to establish the connection. If at all the credential provided is verified, an encrypted connection is established.
The host contains an SSH process that is ready to make a request for the client connection through a TCP or IP port. Immediately when the client initiates a connection, the host responds with the necessary information.
Once the provided information is verified, SSH establishes a new connection for the available environment.
Linux SSH commands
Other than the SSH client command, there are other commands of SSH:
1. ssh-keygen
This command creates a key pair for public-key authentication.
2. ssh-copy-id
This command configures a public key as authorized on a server.
3. ssh-agent
This command creates an agent to hold a private key for a single sign-on.
4. ssh-add
This command is a tool to add a key to the agent.
5. scp
This command is a file transfer client with an RCP-like command interface.
6. sftp
This command is a file transfer client with an FTP-like command interface.
7. sshd
This command is the open SSH server.
Syntax of the SSH command
The syntax of the ssh command is:
ssh <user name> @host <IP address / Domain name>
The command consists of the keyword ‘ssh’ and the components username and host. Let us look into the components of the SSH command.
1. Ssh command
The keyword ‘ssh’ instructs the system to create a secure and encrypted connection with the host system.
2. User name
The username is the name of the Linux user. This is the user who is being accessed by the host machine.
3. Host
The hast is the machine that is being accessed by the user. The host can be a computer pr a router. The host can be specified by a domain name or IP address.
Techniques of SSH protocol
The SSh protocol is one of the most secure when compared to other protocols like telnet. Let us look at the 3 encryption techniques used by SSH
1. Symmetrical encryption
This technique of encryption generates a simple key for both encrypting and decrypting. This single key is distributed among the hosts and clients and creates a secure connection.
One of the most commonly known symmetrical encryption is the caesar cipher. Symmetrical encryption is not much preferred as it is extremely vulnerable to brute-forcing.
2. Hashing
Hashing is an encryption technique that is used to ensure whether the received data is coming from a legit sender or not. This technique uses a hash function that generates a hash code from the data received.
Hashing also comes with its own disadvantages, it is not possible to regenerate the data from the hash value. The data is authenticated is only if the hash value at both the sender and receivers side is matched.
3. Asymmetric encryption
This technique is the most used and the most secure. It works on the principle of factoring in really large numbers. Asymmetric encryption generated 2 keys called the private and public keys. The private key is used to encrypt messages, while the public key decrypts messages only encrypted using the respective private key.
The private key is kept with the client machine while the public key is distributed to other machines. It must be noted that the private key must be always kept a secret, else it will compromise the entire secure connection.
Installing Open SSH client in Ubuntu
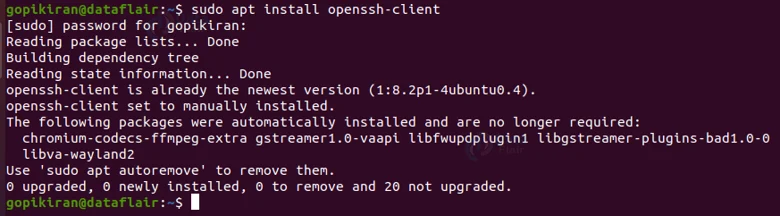
SSH does not come pre-installed on most of the Linux distributions, don’t worry, because you can download it on all of the Linux distros as ssh supports all of them. To install SSH in ubuntu, use the following command:
sudo apt install openssh-client
If at all you want to install SSH in fedora based Linux distros like CentOS, use the command
sudo dnf install openssh-clients
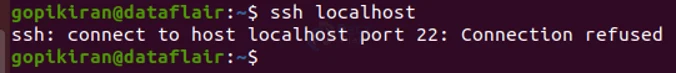
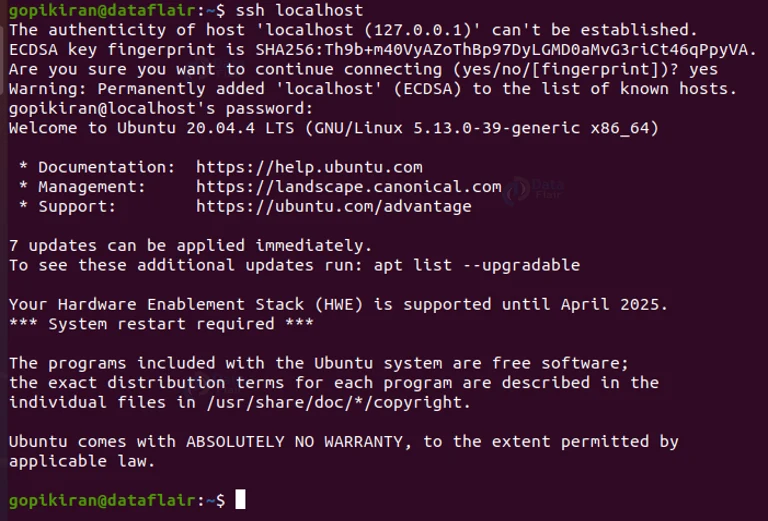
We are not done with the installation part yet. To check the installation status of the server, type the command shown below in the terminal
ssh localhost
If your system does not have the serval tool kit, the command will print the message that the connection has been refused.
In the above output screen, My system does not have the server tool kit, which means only one thing, to install it.
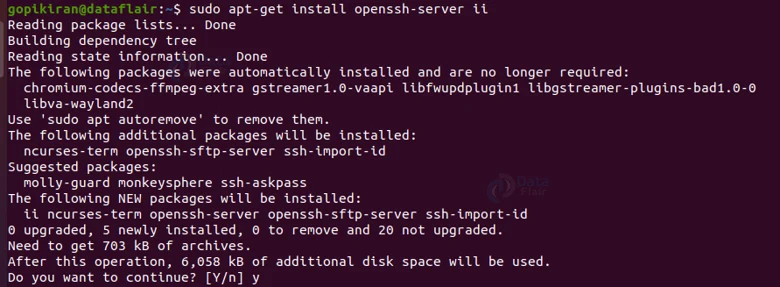
To install the server SSH, type the command shown below in the terminal:
sudo apt-get install openssh-server ii
On executing the command, the system will prompt you to press “y” to confirm the installation of additional packets.
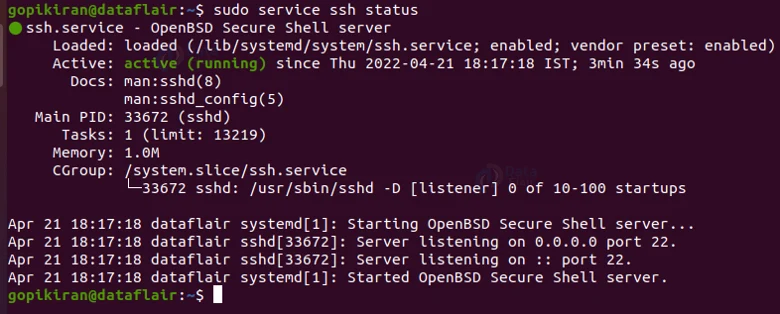
To verify if the installation had been a success or not, type the command
sudo service ssh status
Executing the above command will display the status of the installation.
If you want another method to really crosscheck if the installation has been successful, you can retype the command “ssh localhost”.
This time the output screen will be different (showing confirmation of installation) as we have successfully downloaded the server-side tool kit as well as the host side.
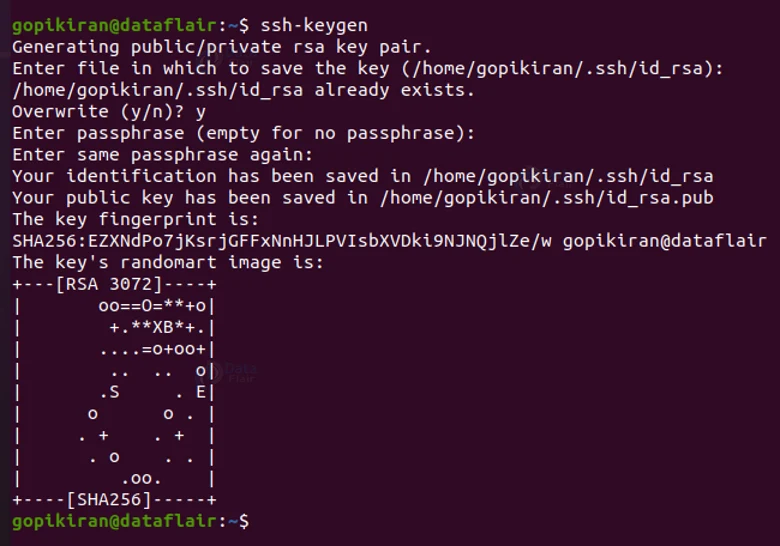
Setting up SSH keys
Now that you have successfully installed open SSH, you need a specific key for an encrypted connection. To generate keys, you can type the command “ssh-keygen”.
Options used with the SSH command
We can use many options along with the SSH command to specify the different specifications of the SSH output. Let us look at some of the most used options along with the SSH command.
1. -c
This option specifies the query class for non-IN data.
2. -C
This option compares SOA records on authoritative nameservers.
3. -d
This option is exactly the same as the option “v” it provides verbose.
4. -i
This option is used for IP6.INT reverse lookups.
5. -I
This option lists all hosts in a domain using AXFR.
6. -m
This option sets the memory debugging flag.
7. -N
This option changes the number of dots allowed before root lookup is done.
8. -r
This option disables recursive processing.
9. -R
This option specifies the number of retries for UDP packets.
10. -s
This option provides a SERVFAIL response
11. -t
This option specifies the query type.
12. -T
This option enables the TCP/IP model.
13. -v
This option provides verbose for a better understanding of the output
14. -V
This option prints information about the version of SSH you are using.
15. -w
This option specifies the wait forever for a reply.
16. -W
This option specifies how long to wait for a reply.
17. -4
This option is used to query only IPv4 transport
18. -6
This option is used to query only IPv6 transport
19. -1
This option forces ssh to use protocol SSH-1 only.
20. -2
This option forces ssh to use protocol SSH-2 only.
21. -A
This option enables authentication agent connection forwarding.
22. -a
This option disables authentication agent connection forwarding.
23. -f
This option requests ssh to go to the background just before executing the command
24. -g
This option allows remote hosts to connect to local forwarded ports.
25. -n
This option prevents reading from stdin.
26. -p <port number>
This option specifies the Port to connect to on the remote host.
27. -q
This option suppresses all errors and warnings
28. -X
This option Enables X11 forwarding or GUI Forwarding.
29. -c <cipher spec>
This option Selects the cipher specification for encrypting the session.
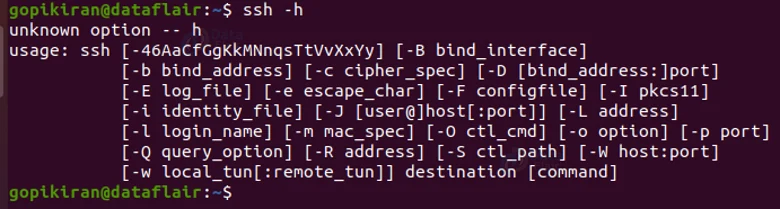
30. -h
This option displays the help screen, which contains the usage of SSH.
How to connect through SSH?
Now that you have installed SSH, we can now establish a connection with the machines. We have already installed both the server and clients, now all there is left to do is establish a connection between the 2.
To establish a secure connection, open the terminal and type the command:
ssh <your username> @ <IP address of the host>
If the machine verifies the IP address of the host you wanted to connect, type the command shown below:
ssh <IP address of the host>
On executing the command, the system will prompt you to enter your password, type it and press enter.
Please note that, if you are establishing a connection for the first time, the system will ask you to continue or not, press “y” and enter. The command will add connect you to a remote server by adding an ECDSA (Elliptical curve Digital Signature Algorithm) key.
Specifying a different user name
We can also use a different username at the remote machine by entering the following command:
ssh [email protected]
The above command can also be written by removing the “@” symbol and using the option “-l” as shown: ssh -l alternative-username sample.ssh.com
Executing command on the server remotely
You can also make use of SSH to execute commands on the server from your remote system without logging in to a shell prompt. To do this, use the following syntax:
ssh <hostname> <command>
For example, if you want to list the contents of the “/temp/doc” directory of the server from your system, use the command shown below:
ssh <hostname> ls /temp/doc
After successful execution of the command, the contents of the remote directory will be displayed to your local shell prompt.
Configuration file of the SSH client
The ssh command reads its configuration file which is present in the path ~/ .ssh/config. We all know by now that all of the configuration files in Linux are stored on the /etc directory, and so is the configuration file of SSH, it is present in the path /etc/ssh/ssh_config.
Port forwarding
The options we have discussed above can be used to set up port forwarding. Before start, let us familiarize ourselves with the terms “local forwarding” and “Remote forwarding”.
Local forwarding means that a local port at the client computer is tunneled to an IP address and port from the server computer. Remote forwarding means that a remote port at the server computer is forwarded to a given IP address and port from the client computer.
Summary
As you have seen, SSH is a really helpful tool that helps in establishing a secure connection between a client and a host. We have seen what SSH is, how SSH works, the main purpose of why SSH is used, other commands which are closely related to SSH, and 3 techniques of encryption.
We have also seen how to install SSH, the syntax along with the various options used with the command, and how to connect using SSH.
Did you know we work 24x7 to provide you best tutorials
Please encourage us - write a review on Google