SELinux – Security Enhanced Linux
FREE Online Courses: Elevate Your Skills, Zero Cost Attached - Enroll Now!
In this article, you will learn what SELinux is, its features, and its uses. We will also be looking into the modes of Se Linux and how it works. In the end, we will take a brief look at some of the commands used with regard to SElinux.
What is SELinux?
Let’s get the obvious question out of the way. SELinux stands for Security-Enhanced Linux, like Linux was not secure enough already! Jokes aside, Se Linux is extremely useful to system administrators as it allows them to have more control over who can access the system and who cannot.
Security-Enhanced Linux or SELinux is a security architecture for Linux systems that allows administrators to define access controls over applications, processes, and files on a system.
It used security policies, which are a set of rules that tells SELinux what is accessible. SELinux is a set of kernel modifications and user-space tools that provide a mechanism for supporting access control security policies.
It provides various security policies like U.S Department of Defence style mandatory Access Control (MAC). SELinux was originally developed by the United States Security Agency (NSA) as a series of patches to the heart of Linux using Linux Security Modules (LSM)
Why SELinux?
We all know that Linux-based operating systems are the safest out there. Linux asks for authentication in the form of a password before running and executing every program or application. Then why do we need SELinux?
In Linux for every file and directory the user, user group, and other users have the permissions for reading (r), writing (w), and executing (x). Using the chmod command, the user can change these permissions and give himself all the permission, leaving the group and other users with no permission.
In such a case, the system administrator can use security policies to stop users from running scripts or files from their home directories. Hence with SELinux, you can specify access controls for users. This is just one such case where SELinux comes to help, there are various other cases where the administrator can use SELinux.
Features of SELinux
Here are some of the features that SELinux includes:
1. SE Linux provides a clean separation of policy from enforcement.
2. It has well-defined policy interfaces
3. Flexible policy
4. Provides support for policy changes
5. It controls the use of “capabilities”
6. It keeps individual labels and controls for kernel objects and services
7. Independence of certain security-label formats and contents
8. It controls open file descriptors, files, directories, and filesystems
9. It has a default-deny policy
10. It takes measures to protect system integrity and data confidentiality
11. Controls network interfaces, sockets, and messages
12. Independence of certain policies and policy languages
13. Control over process initialization and execution
14. Provides support for application querying the policy
15. Cached information on access decisions through the AVC
How does SELinux work?
SE Linux uses security policies, which are a set of rules that define what can and can not be accessed.
Whenever a process or application makes a request to access a file or any other object for that matter, SE Linux checks with an access vector cache (AVC).
If at all SE Linux cannot make decisions regarding checked permissions or access-based, it sends the request to the security server. The server checks for the security context of the file or app and then grants or denies permission accordingly. If a permission id is denied, the message of denial from AVC will be available in the “/var/log.messages” directory.
Sudo apt install policycoreutils
The initial work of SE Linux was directed toward normalizing an approach providing compulsory and voluntary access controls (MAC and DAC) within a UNIX-based computing interface that can be assigned to the National Security Agency’s (NSA) trusted UNIX working group.
Security-Enhanced Linux was designed to demonstrate the value of compulsory access controls to the Linux community. The NSA, who is the key developer of SE Linux. Released the very first version on the 22nd of December 2000. They released the source code under the GNU GPL license making it open source as anyone can access it and make changes for free.
The software was later merged into the mainline Linux kernel on the 8th of August 2003.
Users of SELinux
Roles and SE Linux need not be related to the actual system users and roles. For every user or process, SE Linux allocates a 3-string context. This string consists of a username, role, and domain.
This system of generating assigning a 3-string context is more flexible than required. Most of the real users share the same SE Linux username, and all the access control is managed through the domain.
Policies and security contexts of SELinux
We have seen that SE Linux has many policies and security contexts in the feature section. Let dive a little deeper to see what exactly the policies contain and what their uses are.
General policy rules include explicit permissions like which domain the user must possess to perform specific actions with the given target.
The Policy of SE Linux consists of a rule file, a mapping file, and an interface file. Thes 3 files must be put together with the SE Linux tools to produce a single policy file. The final compiled policy can be loaded into the kernel to make it active.
Command Line Utilities of SELinux
SELinux can clearly control which activities a system allows for each process, daemon, and user. Let us look at some of the command-line utilities included:
1. selinux-policy-upgrade
2. load-policy
3. semodule-package
4. checkmodule
5. selinux-config-enforcing
6. selinuxenabled
7. secon
8. check-selinux-installation
9. getsebool
10. checkmodule
Labeling and type enforcement in SELinux
Before proceeding any further, we must discuss 2 of the most important concepts in SE Linux, they are labeling and type enforcement.
Labeling: Security-Enhanced Linux works as a labeling system. This means that all of the ports, files, processes, and files in the system have an SE Linux label connected with them. Labels, as the name suggests is a way of grouping things together.
Type enforcement: the use of type enforcement in SE Linux is to enforce a policy that is defined in the system. It is a type of SE Linux policy that defines if a process running with a certain type can access a file labeled with a certain type.
Modes of SELinux
SELinux has 3 modes, actually speaking it is just 2 modes, however, we even count the disabled mode of SELinux.
1. Enforcing
The default state of SELinux is the enforcing mode. This mode enforces the SELinux security policy. Unless SELinux security policy rules permit users and programs, they are denied access.
2. Permissive
This mode of SELinux is a diagnostic state. In the permissive mode, the security policies are not enforced instead, SELinux sends denial messages to a log file. This mode allows you to see the denied parts if SELinux was running in the enforcing mode.
3. Disabled
Don’t even know why people account for this as a mode of SELinux, but as the name suggests, SELinux is not enabled and it does not enforce a security policy. Well, it doesn’t enforce, because there is no policy loaded in the kernel. It is disabled!
Installing SELinux
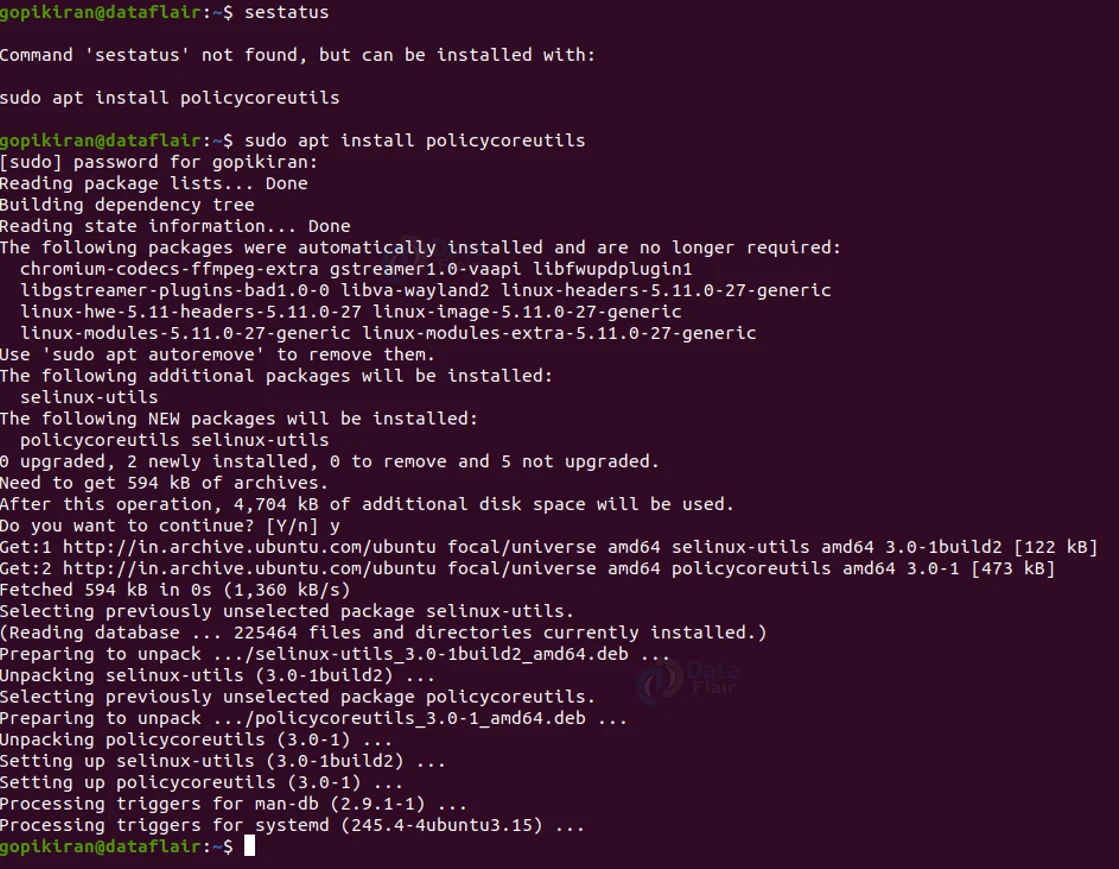
Now obviously if we want to use SELinux, we will first have to install it. SELinux does not come preinstalled in Linux distros. We can install SELinux by using the command below:
Sudo apt install policycoreutils
Once you do so, the system prompts you to enter your password. It also prompts you to press ‘y’ to confirm installation:
Checking the status of SELinux
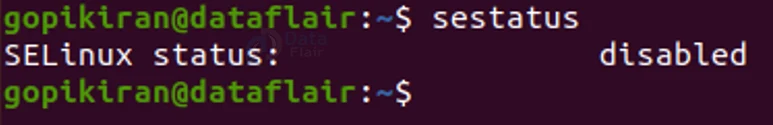
Now that you have installed it, let’s check the status of SELinux by typing the command “sestatus”
Since you have just installed SELinux, it will be disabled.
Enabling SELinux
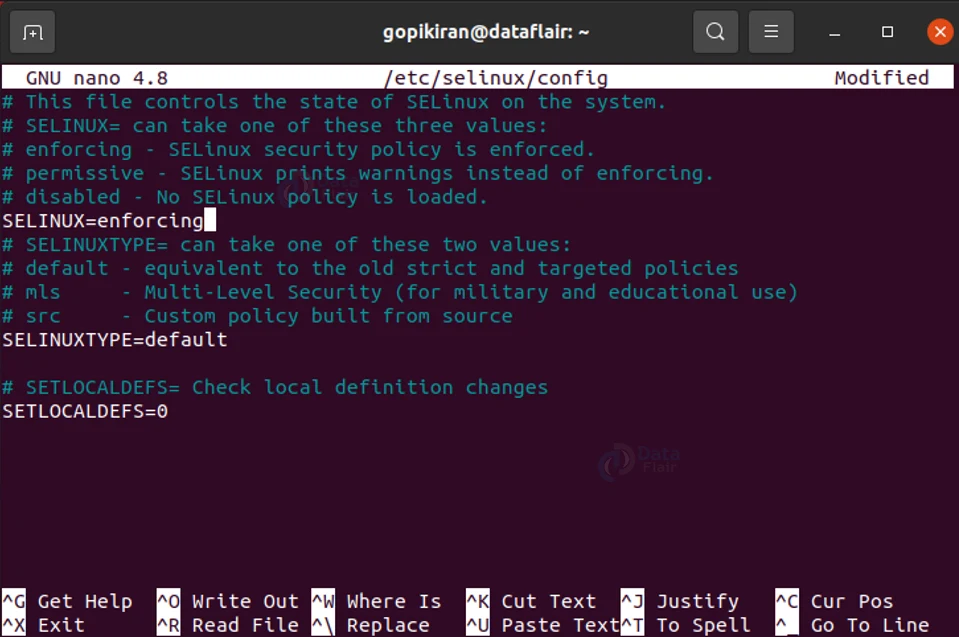
To enable SELinux, you first have to type in the command “sudo nano /etc/selinux/config” in the terminal as shown below.
Upon typing the command “sudo nano /etc/selinux/config”, the terminal will open up the configuration files of SELinux in the nano text editor. Here you must change the text ‘disabled’ to either ‘enforcing’ or ‘permissive’.
Once you make the changes in the text editor, you have to press “ctrl” + “x” to exit from the configuration files opened in the nano text editor. Then press “y” and “enter” to confirm your changes. You must then reboot your computer to see the changes, you can directly restart your PC by typing the command “sudo reboot”.
After rebooting, you can check if your changes have worked by using the “sestatus” command.
Changing nodes of SELinux:
After enabling SELinux, you can switch between the modes enforcing and permissive.
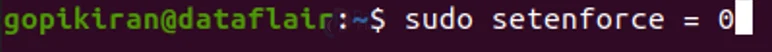
To Switch from enforcing mode to permissive mode, you can type the command:
sudo setenforce = 0
This command will turn off enforcing mode, thereby turning on permissive mode.
To Switch from permissive mode to enforcing mode, you can type the command:
sudo setenforce = 1
This command will turn on enforcing mode, thereby turning off permissive mode.
Viewing policy modules
As mentioned earlier, SELinux has many policies that are extremely helpful to the system administrator. To view the policy modules that are currently running in your operating system, you can type the command:
sudo semodule -l
Benefits of SELinux
There are many advantages of using SELinux, let us look into a few.
1. SELinux Labels all the files and processes. The policy rules in SELinux define how processes interact with files and also other processes. It allows access if and only if there exists an SELinux policy module that specifically allows it.
2. SELinux can also be used to enforce data integrity and confidentiality. It also protects processes from untrusted inputs
3. SElinx policy modules are administratively defined and carried out system-wide
4. SELinux provides fine-grain access control. SELinux’s access decisions are based on all the available information like SELinux user, role, type, security level, and a lot more.
Configuring SELinux
You can configure Security-Enhanced Linux to protect your system in a number of ways. The most common methods to configure are multi-level security (MLS) or targeted policy.
The targeted policy is the default option. It covers a wide range of tasks, services, and processes
Multi-level security or MLS on the other hand can be very complicated. It is typically only used by government organizations.
You can check what configuration your system is supposed to be running by looking at the “/etc/sysconfig/selinux” file.
DAC and MAC
Just to take things a notch deeper, let us understand what Discretionary access control (DAC) and mandatory access control (MAC) are.
Discretionary access control (DAC)
In DAC files and processes have owners. You can either have users, groups or other global users own a particular file. Moreover, users have the right to change the permissions of the file using the chmod command.
The root user has complete access and control with the DAC system because If you have root access, you can access the files of any other user in your system, or do whatever you want on the system.
Mandatory access control (MAC)
SELinux is an example of the MAC system. In MAC systems there is an administratively set policy around access. Even though the DAC system settings are changed on your home directory, the SELinux policy will prevent another process or user from accessing the directory.
The policies let you cover a large number of processes. You can also make changes with SELinux to limit the access between directories, files, users, and more.
Handling errors in SELinux
To gain complete knowledge of SELinux, it is only fair to learn how to deal with the errors in it. Let us look at 4 of the most common problems:
1. Wrong labels
If the labels in your system are incorrect, you can use the tools to fix them.
2. Fixing a policy
You may need to inform SE Linux regarding the changes you have made or adjust to a specific policy.
3. Bug in a policy
This could just be a bug that exists in the policy that needs to be addressed
4. Hacking of your system
Even though SELinux can safeguard your systems in many scenarios, there is still a possibility for your system to be compromised. If you suspect that your system has been broken into, take action immediately.
Summary
SELinux can also set various other custom modules if needed. For example, if the default action of a policy module is to deny and an SELinux rule does not exist to allow, like a process for opening a file, the access is denied. However, this process is very complex, as it involves coding up your own custom policy module and also installing various other tools and utilities.
Your opinion matters
Please write your valuable feedback about DataFlair on Google