Linux chroot Command
We offer you a brighter future with FREE online courses - Start Now!!
In this article, you will learn what chroot is, why and when you should use it. In the end, you will also be learning how to create your own chroot environment, where you can perform some chroot commands.
What is chroot?
Chroot is an operation that changes the apparent root directory for the current running process. In simple words, chroot does one thing — It runs a command with a different root directory. Only some root users and processes are allowed to use the chroot command.
Chroot does not make any modifications to your disk, nonetheless, it can make it appear that way from the POV of the processes running under it.
This command runs in such a modified environment that cannot access files outside the root directory.
The process of chrooting accomplishes the same thing as changing the mount namespace for a process, apart from doing so at a higher level than the namespace modification.
The command which is being run in chroot has no idea that anything outside of the jail exists. It does not have any links to it, and as far as its aware, it is running on the root system anyway. Since there is absolutely nothing above the ‘root’, the command can’t access anything else.
Why use chroot?
The number one thing chroot is used for is to lock away system daemons so that any security vulnerabilities in them don’t affect the rest of the system.
The chroot environment works very similarly to a virtual machine. In fact, chroot is even lighter than a virtual machine because the system doesn’t need a hypervisor to be installed or configured. And the fact that a chroot environment does not have a kernel installed and shares your current existing kernel makes it even better.
Since chroot environments are lightweight, quick to deploy, and creating and firing up can be automated, they prove to be extremely helpful in many fields which we will discuss later.
Chroot is also useful as a budget container. It creates a subset of your operating system and runs apps in an isolated environment.
What is a chroot jail?
As we discussed, chroot is a process/command that is run in such a modified environment that it cannot access files outside the root directory. This modified environment is what we call “jailed directory” or “chroot jail”. It is same as a chroot environment.
Uses of chroot
There are many uses of chroot, The chroot environment or “jail” can be useful for:
1. Setting up a test environment.
2. Recovering your system
3. Recover your password, as you can reset your password.
4. Reinstalling the bootloader such as Grub or Lilo
5. Giving privilege separation for the unprivileged process
6. Running old programs or ABI in-compatibility programs without crashing applications or systems.
Apart from these, chroot proves to be useful in many fields like:
Software development and product verification
We all know that developers write software and the product verification team verifies it. Sometimes the product verification team finds issues that can’t be replicated on the developers’ computers. This happens because the developer has all sorts of tools and libraries installed, which the average user, does not.
Chroot comes in handy in such situations, as it allows the developer to have a plain and simple environment on their computer, in which they can test the software they develop before giving it to the product verification team.
Reducing development risks
Since the developer can create a bare minimum, environment to test his work, he can also create a dedicated development environment so that nothing that happens in the environment he created messes up his actual computer.
Running deprecated software
Sometimes it requires someone to have an old version of something running, and if the old system has requirements that wouled clash or be incompatible with your current version of the operating system, you can always create a jail environment such that it meets the requirements of the old software you have to run,
Options used with chroot
Before we look at how to create a chroot environment, let us take a look at the options used with chroot
1. –userspec = <user>.<group>
This option describes the user and group which is to be used. You can either specify the name or numeric ID of the user or group
2. –group = <group list>
This option describes the supplementary groups as g1, g2, g3, ……, gn.
3.– skip-chdir
This option does not change the working directory to “/”
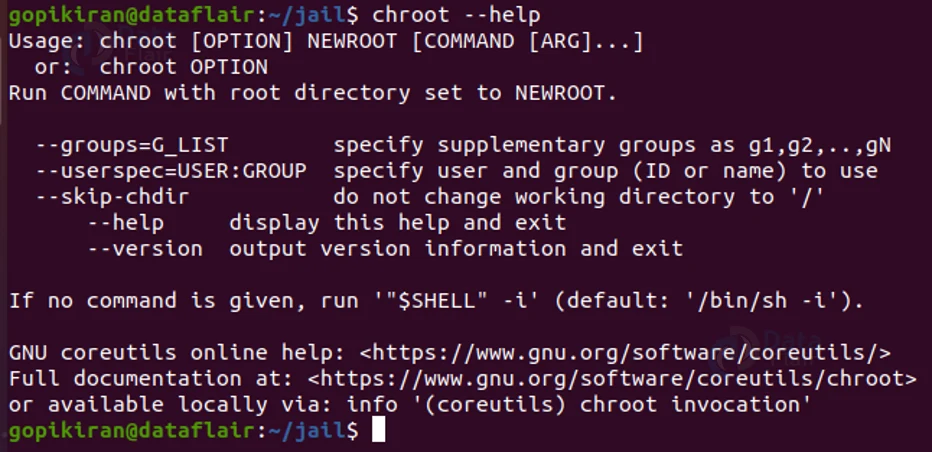
4. –help
This option shows the help message of chroot as below:
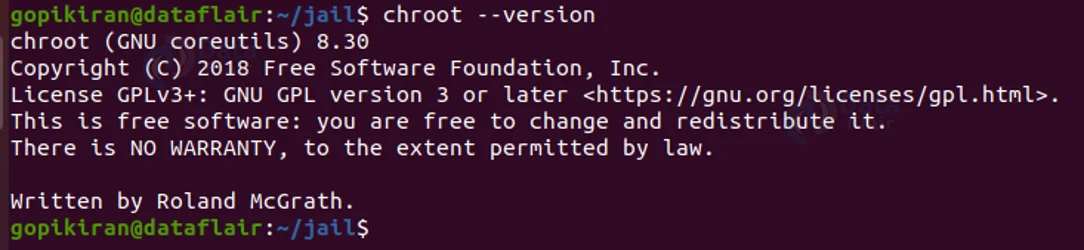
4. –version
This option gives information about the version of chroot you are using.
How to create a chroot environment?
Now that you have learned the uses of a chroot environment, let us create one. Before you begin creating a chroot environment, make sure your root directory is “/”
Step – 1
To create a mini jail, create a jail directory inside the home directory, this will later be our new root directory
Step – 2
We need to give our new root directories some feature like a bash shell, to do so first let us create the files so that we can later copy them.
Step – 3
Let us go into the jail directory to perform some actions.
Step – 4
Now that we are in the jail directory which has subdirectories, let us copy the “/bin/bash” and “/bin/ls” into “$HOME/jail/bin”
Step – 5
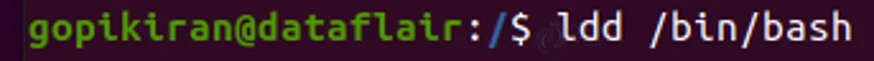
Now that you have copied the files, use the ldd command to print the shared libraries to “/bin/bash”
Step – 6
After copying the bash files, it is now time to copy the libraries to “$HOME/jail/lib64/” using the cp command
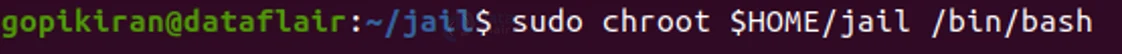
Step – 7
After successfully copying the files you can finally chroot into your mini jail.
And voila, you have your chroot environment setup!
Can a process escape the jail?
Well, not easily. Unless the process is running as root, it cannot escape the jail. Chroot does not block access to low-level system resources because it would require root access. Therefore only a privileged process could easily escape the jail.
Nonetheless, chroot is not a bulletproof security tool, as it is not fully containerized. It should not be thought of as a firewall that will save your system from attackers.
Finding out if the service is in the chrooted jail or not
Since we have discussed whether a process can escape the jail or not, it is only fair if we also know how to find out if a service is in the jail environment created.
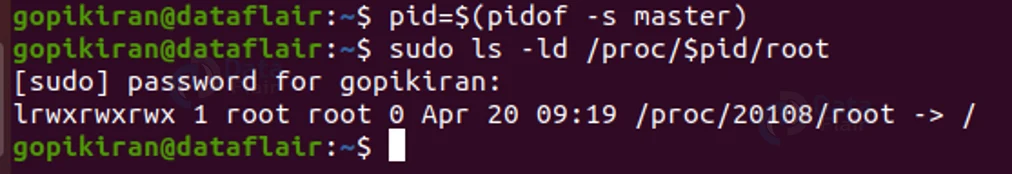
Well, to find out if the service is in the jail environment you created or not, you can use the following 2 commands:
pid=$(pidof -s master) Ls -ld /proc/$pid/root
In the output, the PID 20108 is pointing out to ‘/’, and we all know that ‘/’ means root. Therefore. The root directory for the application is not chrooted.
Summary
Thus you have learned what chroot is, what are its uses, and the options used with chroot. You have also seen the uses of a chroot environment and even created your own.
Your 15 seconds will encourage us to work even harder
Please share your happy experience on Google