IoT Security – Major Problems Faced by IoT System
FREE Online Courses: Dive into Knowledge for Free. Learn More!
In our last IoT Tutorial, we studied Contiki Operating System. Today, we will discuss IoT Security and some major problems we faced on IoT system. These Internet of Things security helps to face the problems, at the time of working on IoT.
So, let’s start IoT Security.
IoT Security
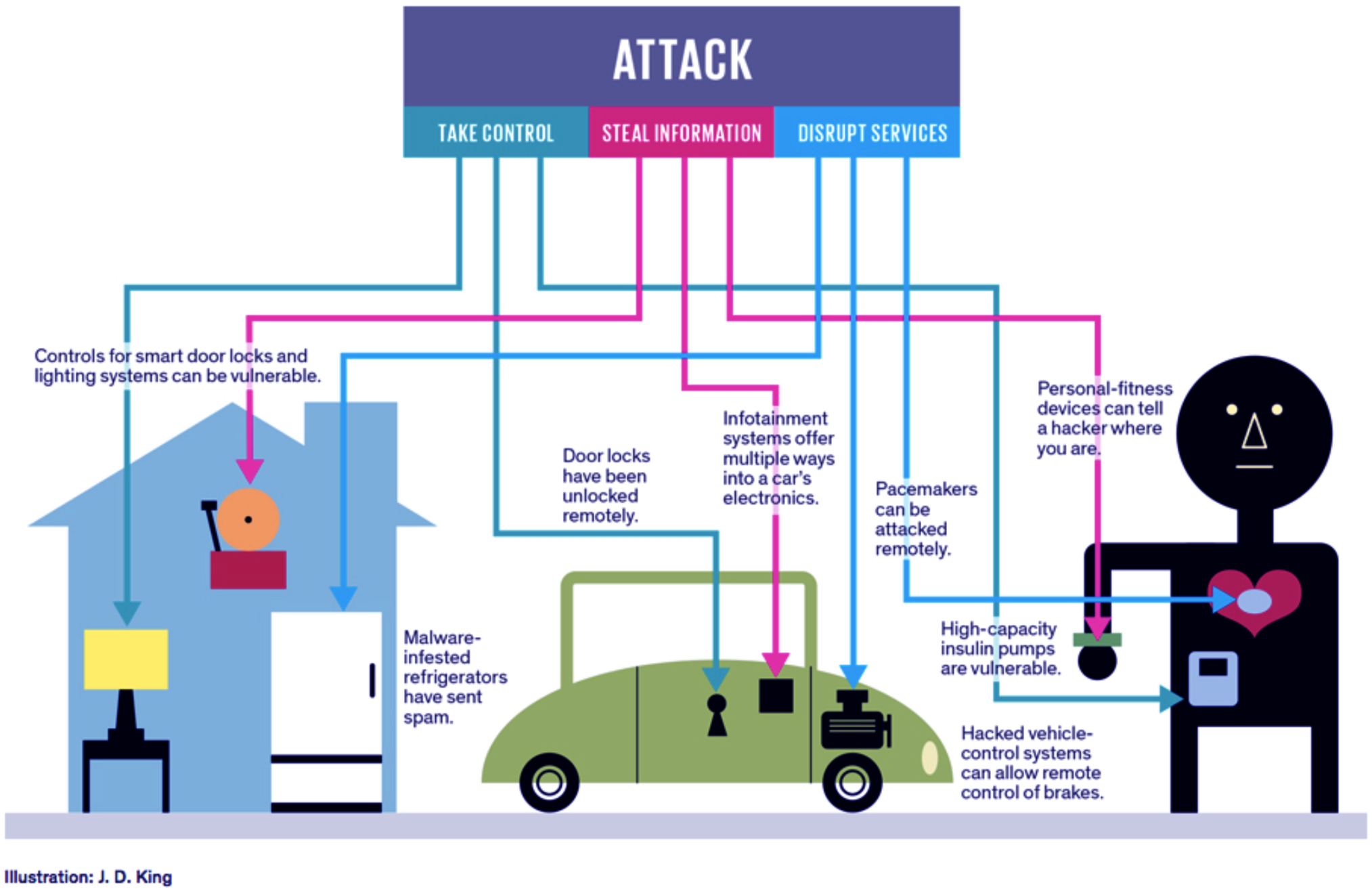
Every linked tool creates opportunities for attackers. Such vulnerabilities are extensive, even for a single small tool. The dangers posed consist of facts transfer, the device gets entry to, malfunctioning devices, and usually on/usually-related devices.
The primary demanding situations in-security continue to be the safety barriers related to producing low-cost gadgets, and the growing range of gadgets which creates greater possibilities for assaults.
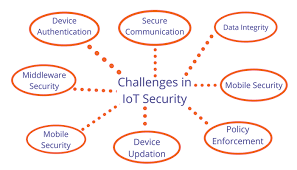
3. Problems Faced by IoT Systems
These are some problem which can be solved by IoT Security. Let’s discuss them one by one:
a. Unpredictable Conduct
The sheer quantity of deployed gadgets and their lengthy listing of enabling technology method their behavior within the discipline can be unpredictable. A selected machine may be properly designed and inside administrative manipulation, but there are not any ensures about how it will interact with others.
b. Tool Similarity
IoT devices are fairly uniform. They make use of the same connection technology and components. If one system or tool suffers from vulnerability, many more have the equal difficulty.
c. Deployment Difficulty
One of the primary dreams of IoT stays to be in the vicinity of superior analytics and networks where they previously couldn’t be. Therefore creates the trouble of securing the devices bodily in odd or difficulty accessed places.
d. Long Tool Lifestyles and Expired Guide
One of the benefits of IoT gadgets is longevity, however, that lengthy existence additionally means they’ll outlive their tool support. Examine this to traditional structures which normally have guide and upgrades long after many have stopped using them.
Orphaned devices lack the same safety hardening of different systems because of the evolution of era through the years.
e. No Improve Aid
Many IoT devices, like many cell and small gadgets, aren’t designed to permit improvements or any modifications. Others provide inconvenient enhancements, which many proprietors ignore, or fail to see.
f. Poor or No Transparency
Many IoT gadgets fail to offer transparency in regards to their functionality. Customers can not study or access their approaches and are left to count on how devices behave.
They have no manage over undesirable capabilities or records series; furthermore, whilst a manufacturer updates the device, it could carry greater undesirable capabilities.
g. No Indicators
Every other purpose of IoT stays to offer its splendid capability without being glaring. This introduces the trouble of user awareness. Users do no longer display the devices or recognize whilst something is going wrong. Protection breaches can persist over long intervals without detection.
So, this was all about IoT security. Hope you like our explanation.
Conclusion
Hence, today we learned how IoT systems deal with security challenges. We covered the different issues that arise while dealing with IoT security systems. Furthermore, if you have any query regarding the Internet of Things security, feel free to ask in the comment box.
You give me 15 seconds I promise you best tutorials
Please share your happy experience on Google