Transport Layer Protocols
FREE Online Courses: Dive into Knowledge for Free. Learn More!
The transport layer is the fourth layer from the top in the OSI Model. Its primary function is to provide communication services directly to application processes running on separate hosts.
The transport layer facilitates logical communication between application processes that execute on separate hosts. Although the application processes on separate hosts are not physically connected, the application processes transmit messages to each other through the logical connection provided by the transport layer.
Transport layer protocols are used in end computers but not in network routers.
A computer network offers several protocols to network applications. TCP and UDP, for example, are two transport layer protocols that each provide a unique set of services to the network layer.
All transport layer protocols support multiplexing and demultiplexing. Other services include dependable data transfer, bandwidth assurances, and latency guarantees.
Each application at the application layer has the capability of sending a message through TCP or UDP. These two protocols are used by the application to communicate. In the internet layer, both TCP and UDP will communicate with the internet protocol. The apps have access to the transport layer and may read and write to it. As a result, we might argue that communication is a two-way street.
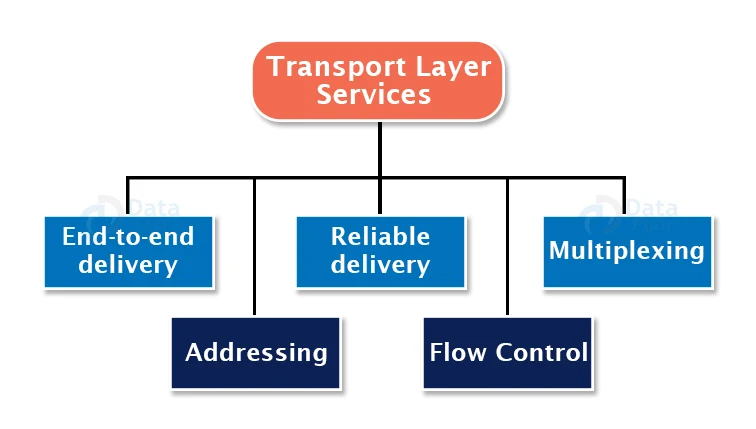
Services provided by the Transport Layer:
1. End-to-end delivery:
The complete message is sent to the destination by the transport layer. As a result, it secures the complete transport of a message from source to destination.
2. Addressing:
The transport layer interacts with the session layer’s functions, according to the tiered model. Many protocols integrate session, presentation, and application layer protocols into a single application layer. Delivery to the session layer in these situations entails delivery to the application layer. Data created by one programme on one system must be sent to the appropriate application on another machine. The transport layer provides addressing in this scenario.
The user address (as a station or a port) is provided by the transport layer. The port variable represents a specific Transport Service access point user of a certain station (TSAP). Each station has a single mode of transportation.
The transport layer protocols must be aware of which upper-layer protocols are in use.
3. Reliable delivery:
By retransmitting missing and broken packets, the transport layer provides reliability services.
There are 4 dimensions to reliable delivery:
a. Error Control:
Error Control is the basic function of dependability. In truth, no transmission will be completely error-free. As a result, transport layer protocols are built to ensure error-free transmission.
The error handling technique is likewise provided by the data connection layer, although it only assures node-to-node error-free transmission. However, node-to-node dependability does not guarantee end-to-end dependability.
The data connection layer inspects each network for errors. If an issue is introduced into one of the routers, the data link layer will not detect it. It only detects faults that have occurred between the start and finish of the connection.
As a result, the transport layer checks for defects from end to end to guarantee that the packet arrives successfully.
b. Sequence Control:
The second part of reliability is sequence control, which is done at the transport layer.
On the transmitting end, the transport layer is responsible for guaranteeing that packets received from the upper levels may be utilised by the lower layers. It guarantees that the various portions of a transmission may be accurately reassembled on the receiving end.
c. Loss Control:
A third facet of reliability is loss control. The transport layer guarantees that all fragments of a transmission, not just portions of them, arrive at their destination. A transport layer assigns sequence numbers to all transmission pieces on the transmitting end. These sequence numbers help the transport layer of the receiver to identify the missing segment.
d. Duplication Control:
The fourth component of reliability is duplication control. The transport layer ensures that no duplicate data is delivered to the destination. Sequence numbers are used to detect missing packets, as well as to identify and delete duplicate segments by the receiver.
4. Flow Control:
The use of flow control prevents the transmitter from overloading the recipient. If the receiver becomes overwhelmed with data, it discards the packets and requests that they be retransmitted. This increases network congestion and, as a result, reduces system performance.
Flow control is handled by the transport layer. It employs the sliding window protocol, which increases the efficiency of data transmission while also controlling the flow of data so that the receiver is not overburdened. The sliding window protocol is byte oriented as opposed to frame orientated.
5. Multiplexing:
There are two types of multiplexing:
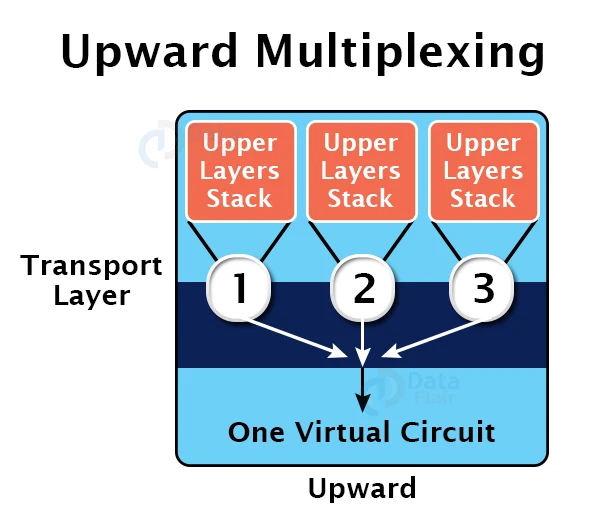
a. Upward Multiplexing:
Multiple transport layer connections using the same network connection is referred to as upward multiplexing. The transport layer delivers numerous transmissions intended for the same destination along the same channel to save costs; this is accomplished by upward multiplexing.
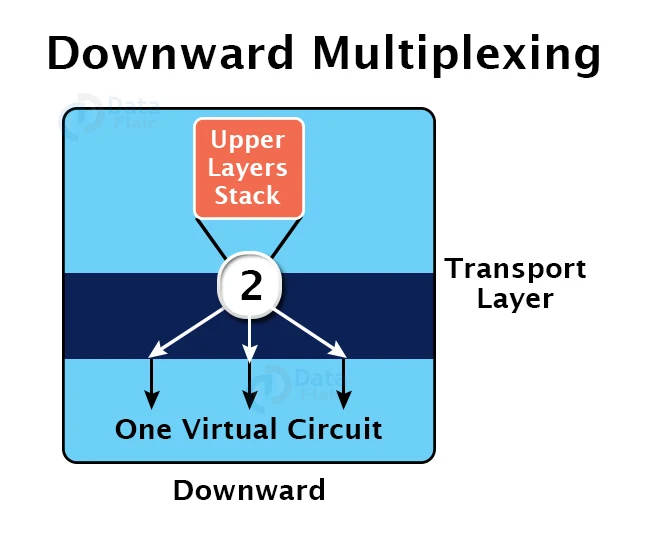
b. Downward Multiplexing:
Downward multiplexing refers to the usage of several network connections using a single transport layer link. It allows the transport layer to divide a connection across numerous pathways in order to increase throughput. When networks have a limited or sluggish capacity, this sort of multiplexing is utilized.
Transport Layer Protocols:
TCP and UDP are the protocols that represent the transport layer.
In the network layer, the IP protocol transports a datagram from a source host to a destination host.
The operating system now supports multiuser and multiprocessing settings, and an executing program is referred to as a process. When a host sends a message to another host, it indicates that the source process is transmitting a process to the destination process. Some connections to particular ports known as protocol ports are defined by transport layer protocols.
An IP protocol is a host-to-host protocol that can deliver a packet from a source host to a destination host, whereas transport layer protocols are port-to-port protocols that work on top of IP protocols to deliver packets from the originating port to IP services and from IP services to the destination port.
Each port is identified by a 16-bit positive integer address.
User Datagram Protocol (UDP):
UDP is short for User Datagram Protocol. It is a basic protocol that allows for nonsequential transmission. It is a protocol that does not require a connection to be made before functioning. This protocol is used when speed and size are more critical than dependability and security.
UDP is an end-to-end transport level protocol that adds transport-level addresses, checksum error control, and length information to higher layer data.
A user datagram is a packet generated by the UDP protocol.
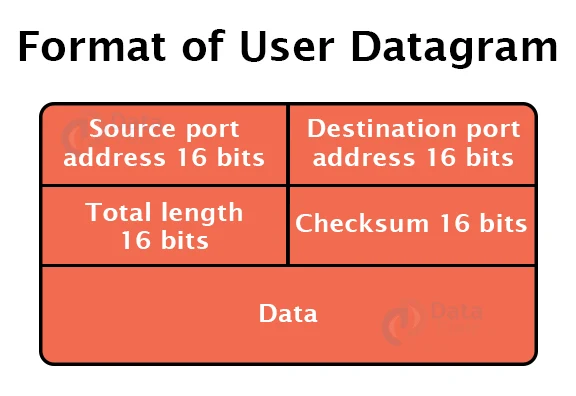
Format of User Datagram:
a. Source port address:
It specifies the address of the application process that sent the message. The source port address is 16 bits long.
b. Destination port address:
It specifies the application process address that will receive the message. A 16-bit address is used for the destination port address.
c. Total Length:
It specifies the user datagram’s entire length in bytes. It is a field of 16 bits.
Checksum:
The checksum is a field that is 16 bits in length, and is used to detect errors.
Disadvantages of UDP:
1. UDP offers the fundamental functions required for the end-to-end delivery of communication.
2. When reporting an error, it does not describe the damaged packet and does not give any sequencing or reordering operations.
3. UDP can detect an error, but it can not indicate which packet was lost since it lacks an ID or sequencing number for a specific data segment.
Transmission Control Protocol (TCP):
TCP is an abbreviation for Transmission Control Protocol. It offers apps with full transport layer services.
It is a connection-oriented protocol, which implies that it establishes a link between both ends of the communication. TCP creates a virtual circuit between sender and recipient for the length of transmission to establish the connection.
Features of TCP:
1. Stream data transfer:
The TCP protocol sends data in the form of a continuous stream of bytes. TCP groups bytes into TCP segments, which are subsequently given to the IP layer for transmission to the destination. TCP segments the data and forwards it to the IP.
2. Reliability:
TCP allocates a sequence number to each byte sent and waits for a valid acknowledgement from the receiving TCP. If no ACK is received within a timeout interval, the data is resent to the destination.
The sequence number is used by the receiving TCP to reassemble the segments if they come out of order or to delete duplicate segments.
3. Flow Control:
TCP sends an acknowledgment back to the sender stating the number of bytes it may accept without exceeding its internal buffer when it receives. The amount of bytes delivered in ACK is the largest sequence number that it may receive without issue. This process is also known as the window mechanism.
4. Multiplexing:
Multiplexing is the technique of taking data from several programmes and passing it to various apps on various machines. The data is forwarded to the appropriate application at the receiving end. This is referred to as demultiplexing. TCP uses logical channels known as ports to send the message to the relevant application.
5. Logical Connections:
A logical connection is a mix of sockets, sequence numbers, and window widths. The pair of sockets used by transmitting and receiving processes uniquely identifies each connection.
6. Full Duplex:
TCP offers Full Duplex service, which means that data may travel in both ways at the same time. To provide Full Duplex service, each TCP should have transmitting and receiving buffers to allow segments to travel in both ways. TCP is a protocol that manages connections. Assume that process A wishes to communicate and receive data from process B.
The following stages take place:
a. Make a connection between two TCPs.
b. Data is sent and received in both directions.
c. The connection is closed.
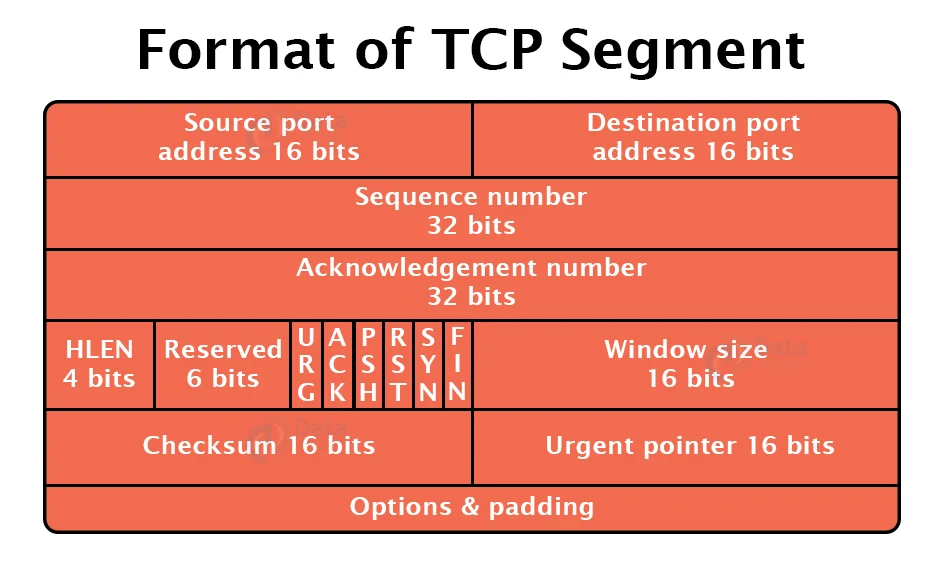
Format of TCP Segment:
a. Source Port Address:
It is used to provide the location of an application software on a source machine. It is a field of 16 bits.
b. Destination Port Address:
It specifies the location of an application software on a destination machine. It is a field of 16 bits.
c. Sequence Number:
A data stream is split into two or more TCP segments. The 32-bit sequence number field reflects the data’s location in the original data stream.
d. Acknowledgement Number:
A 32-field acknowledgement number indicates that data from other communicating devices has been acknowledged. If the ACK field is set to 1, it indicates the sequence number that the recipient expects to receive.
e. Header Length (HLEN):
It determines the TCP header size in 32-bit words. The header must be no less than 5 words long and no more than 15 words long. As a result, the maximum size of the TCP header is 60 bytes, while the minimum size is 20 bytes.
f. Reserved:
It is a six-bit field that will be used in the future.
g. Control Bits:
Each bit in a control field operates separately and independently of the others. A control bit specifies the usage of a segment or acts as a check for the correctness of other fields.
h. Window Size:
The window is a 16-bit parameter that determines the window’s size.
i. Checksum:
The checksum is used to detect errors. It is a 16-bit field.
j. Urgent Pointer:
If the URG flag is set to 1, this 16-bit field indicates that it is the final urgent data byte and is offset from the sequence number.
k. Options and Padding:
It specifies the optional fields that provide the recipient with more information.
Types of Flags in the control bit field:
a. URG:
The URG field indicates that the information in a segment is critical.
b. ACK:
When the ACK field is set, the acknowledgment number is validated.
c. PSH:
The PSH field informs the sender that higher throughput is required, hence data must be pushed with higher throughput if feasible.
d. RST:
When there is a misunderstanding in the sequence numbers, the reset bit is utilized to reset the TCP connection.
e. SYN:
The SYN field synchronises the sequence numbers in three sorts of segments: connection request, connection confirmation (with the ACK bit set), and confirmation acknowledgment.
f. FIN:
The FIN field is used to notify the receiving TCP module that the sender has completed data transmission. It is used in three different sorts of connection termination segments: termination request, termination confirmation, and acceptance of termination confirmation.
Comparison of TCP and UDP:
Parameter | TCP | UDP |
| Definition | Before transferring data, TCP creates a virtual circuit. | UDP sends data immediately to the destination computer without checking to see if the recipient is ready to receive. |
| Connection Type | It is a protocol that is connection-oriented. | It is a protocol that does not require a connection. |
| Speed | Slow | Fast |
| Reliability | Reliable Protocol | Unreliable Protocol |
| Header Size | 20 bytes | 8 bytes |
| Acknowledgement | It waits for data acknowledgement and has the capability of resending lost packets. | It does not accept acknowledgements, nor does it retransmit damaged frames. |
Summary:
In this article, we looked at the Transport Layer and the services provided by it in detail. We also looked at the 2 main protocols involved in the functioning of the Transport Layer, which is TCP and UDP. We covered the formats of the User Datagram and the TCP Segment, along with explanations of the various fields in them. Then we concluded with a direct comparison of TCP with UDP.
Did you like this article? If Yes, please give DataFlair 5 Stars on Google