E-Commerce Security Threats and Their Solutions
FREE Online Courses: Dive into Knowledge for Free. Learn More!
E-commerce has become one of the largest industries in the world to function. The evolution of technology and the internet led to the opening of infinite ways to engage with consumers worldwide. But the larger the business, the greater the risk. And this is the case for e-commerce as well.
As a brand or an organization, it is your responsibility to protect all the consumers and yourselves from threats. This is why security concerns over the internet and privacy have gone up in the last few years. Information about the brand and the consumer is out there, making them vulnerable to security issues.
Why is E-commerce Security Important?
Protecting the industry has become the need of the hour as the third party gets the confidential information using unfair means with bad intentions. 15.5% of the total retails sales have come from e-commerce in 2020 and this will only grow with time. There are multiple ways by which this can happen. And many times they are purposeful or just accidental.
But the intention is what matters here as many stakeholders are at risk. 5-% of the small companies think that e-commerce security is rising at its peak with technology developments. With this being said, 60% of the business may not be able to overcome these cyber attacks.
Two major reasons why companies fail in securing their business is ignorance and price manipulation. Inaccurate management at the companies often lead to sacrifice of confidential information. This may be due to lack of budget or ignorance of the employees, but the consequence is always security failure.
Secondly, manipulation of price at the payment gateway has also become quite common. The intruders are mostly targeting this level to steal money. But this is just the tip of the iceberg, there are many specific issues we must be aware of. Let us take a look at different types of threats and the possible solutions to overcome them.
Electronic Payments Threat
The idea of everything taking place online is now applicable for the finance and banking sector as well. The system of online wallets and e-transactions have become very common as a mode of payment. But handling money on a network is also dangerous as hackers may break into the firewall. There are many other risks like –
1. Fraud
The users have pins or passwords to facilitate an online transaction. But payment authorization based on just passwords and security questions does not guarantee the identity of a person. This may lead to a fraud case if someone else gets ahold of our passwords. This way the third person can steal money easily.
2. Tax Evasion
The invoice is provided by the companies as paper records to verify tax collection. But in an online scenario, things become blurry and the Internal Revenue Service faces the challenge. It becomes hard for them to process tax collection and verify if the organization is being ethical or not.
3. Payment Conflicts
These transactions take place between automated electronic systems and the users. Because it’s a machine at the end of the day, errors while handling payments are possible. These glitches and anomalies lead to conflicts of payment and users end up losing their money.
4. E-cash
The paperless cash system is by using online wallets like PayPal, GooglePay, Paytm, etc. Because all the financial information is in that application, a single security breach can lead to the disclosure of private information and monetary loss.
It has four components – issuers, customers, merchants, and regulators. The issuers are the financial institutions, customers are the ones using this money, merchants are the ones earning it and regulators are for monitoring its movement. Some of the threats that e-commerce website face while using e-cash are –
a. Direct Access Attacks
The hackers get direct access to the device and install programs in it without permission. These softwares have worms that automatically save information from the device without getting caught. It can lead to server paralysis and eventually make it offline.
It can also slow down the speed and make consumers go back with a negative experience. To solve this issue in particular, always use a web application firewall, go blacking or change server IP in the worst case scenario. You can read about more solutions in detail below.
b. Backdoors Attacks
The hackers use this attack to enter the user’s system by escaping normal authentication using unethical means. As the name suggests, it functions in the background making it difficult for the users to detect and remove it.
c. Denial of service attacks and Distributed Denial Service Attacks
The hacker breaks into the system and takes away all the accessibility from the user. They block the users from all the functions and resources and disrupt the system temporarily. This is mainly done by using an internet network and the hackers may ask for ransom/favors to activate the device again. In case of DDoS, the hackers will use your computer to sabotage the security of another computer.
d. Eavesdropping
This is a comparatively new way by which hackers listen to our personal conversations over the internet. It doesn’t lead to disruption in the system functioning but gives them access to private communication which they might leverage upon later. The users in this case are not aware of their conversation being tracked. Wifi eavesdropping is also a part of this type.
Personal Information Threats
1. Scraping
This is mostly done by competitive brands to get their hands on sensitive data and valuable internal metrics. The companies are very confidential about such information but hackers/bots can break into the system to get access.
2. Spam
This is usually by sending out attractive baits to get personal information. The spammers can also use blog pages and contact forms to get companies to click on malicious links. This allows them to harm the website’s speed, security, and consumers as well.
3. SQL Injection
It is a technique in which hackers use query submission forms to gain database access. They corrupt all the information using viruses and make it infectious. They may copy the data for personal benefit and delete it from the main system permanently.
4. Bots
These are software that has web crawlers to decide website rankings of existing pages on the internet. The hackers can use these crawlers to track competitor’s policies and strategy leading to unfair market practices. This may be used against the company or in favor of the competitor.
5. Brute Force Attacks
The hackers use this method to draw patterns and guesses to crack user/company passwords. They will do so by using algorithms and multiple combinations until they get the correct password to get in.
6. Trojan horses
This is a malware that users download thinking of it as legitimate software. But it can collect the user pattern, financial information, personal details, and more without the owner’s permission. The commercial website becomes prone to sensitive data leaks and system infections.
7. Cross-Site Scripting (XSS)
This technique uses the planting of malicious JavaScript snippets that track consumer behavior and patterns on websites. This is by accessing customers’ cookies and computers. Content Security Policy is one way to assure customers about their privacy and safety.
8. Man in the middle
Similar to eavesdropping, the hackers use open networks or weaker networks to listen in on conversations between a store consultant and a customer. They can manipulate the message or the response and use the information for personal gain.
9. Hacktivism
Hacking activism is a type of hacking that targets social media more than the websites. It is usually to bring out social issues by breaking into a company’s social media accounts. It can also include spamming websites with email addresses to bring the server down.
Credit/Debit Card Threats
ATM
The fraudsters are very active at these machines to steal card details. Some of the common ways are –
a. Skimming
A device is attached to the card reader at the ATM which skims data as soon as the card enters the machine. AS the user swipes the card, the information from the magnetic strip is copied on the skimming device. The scammers by this method get access to all financial details about the person.
b. Unwanted Presence
This is a physical way of getting financial information which is quite common. The rule at the ATM celery says one person at a time but many people tend to lurk and overlook the card details with negative intention.
c. POS Theft
The salesperson at the store may have an ulterior motive and use the financial information of customers for personal benefits. It is commonly done at merchant stores at the time of POS transactions. This may be done at the billing counter when the person copies the information on the card using unfair means.
d. Online Transaction
Like we read above, online transactions are very risky as hackers can break at any time. They can steal passwords, card details. Personal information, identity, and much more by unethical means. The ways to do them are already mentioned above.
e. Vishing/Phishing
The scammers use SMS and calls to set baits for the users to make them reveal personal information. They may act as a financial institution or some other credible entity to get your card details for unfair practices.
E-commerce Security Solutions
1. Secured Payment Gateway
Using only secured payment getaway is the smartest instruction to follow during online transactions. These gateways have better security and nondisclosure policies to protect all the consumers.
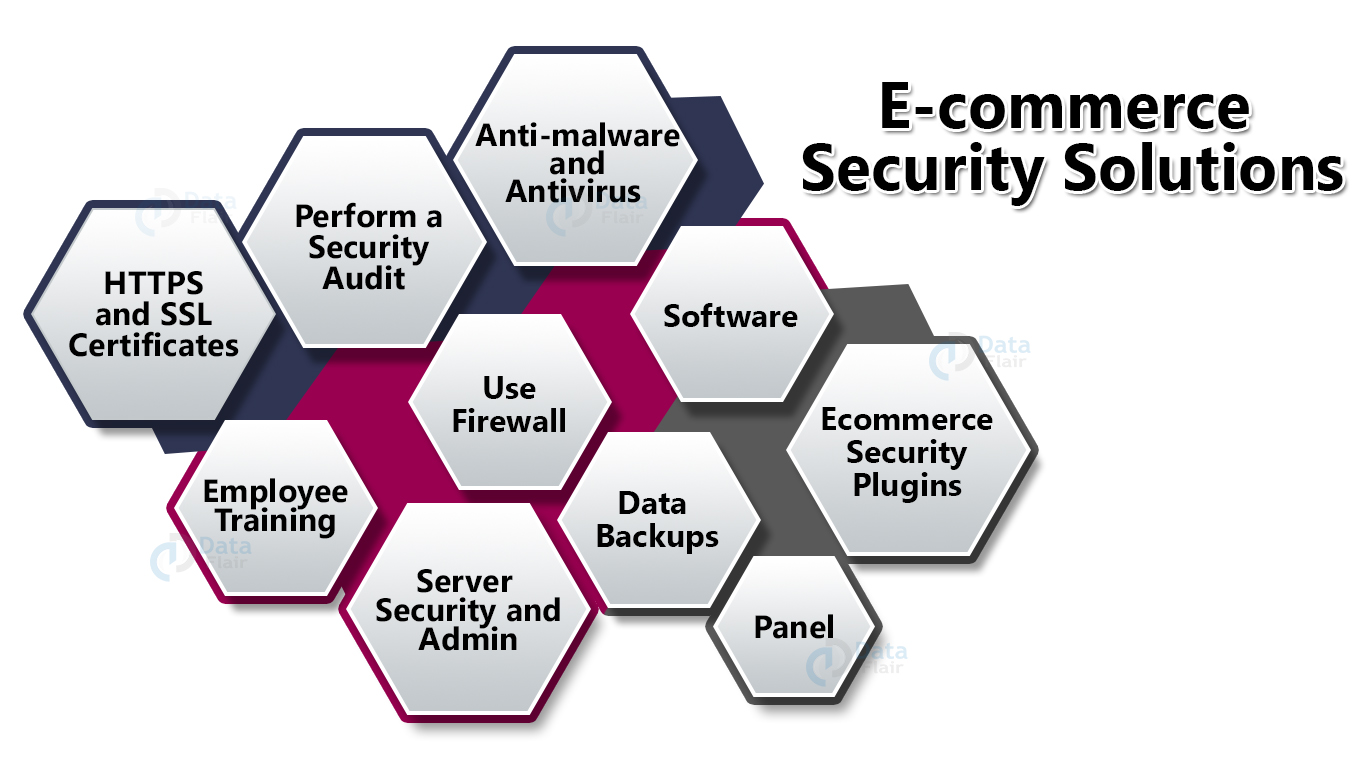
2. Use firewall
A very common technique to block security threats and control network traffic by following defined rules. It is a type of network security software that functions according to security measures put forward by the users. This includes protection from most of the cyber threats like XSS, SQL injection, trojan, etc.
3. HTTPS and SSL certificates
SSL and HTTPS certificates follow a standard protocol that encrypts personal data before transferring it to e-commerce websites. The consumers stay protecting if the website has both certificates. The hackers even with access to information cannot do much with encrypted data.
4. Encryption
A method of converting normal language into a coded one so that hackers can’t crack it. It is essential for websites to follow encryption to avoid data breach at all costs. Only a handful of trained individuals should be able to decrypt this cipher text ensuring safety at all times.
5. Server Security and Admin Panel
The users should carefully follow the password instructions mentioned on different websites. Using a set of charters, symbols and numbers can help users make stronger passwords. They should be careful about restricting access to multiple websites on the internet. Follow the admin panel instructions to avoid security breaches
6. Anti-malware and Antivirus Software
Installing anti-malware/virus software to detect and delete viruses can prevent file or software modification. This ensures the safety of data and personal information from threats like worms, viruses, and Trojan horses.
7. Payment Card Industry Data Security Standard
It is a set of rigid guidelines that defines how a website can remain in a safe space all the time. It gives a direct order of how the host can secure his website at payment level, confidentiality level, etc. Similarly, DSS instructs these websites about how they should save and deal with debit and credit card information.
8. Content delivery networks
It acts as a layer of hosting for websites by improving server content processes in data centers. These centers have their own safety protocols ensuring a double layer of security for the websites.
9. Opt for Multi-Layer Security
The new features of many software allow multi-layer security ensuring data protection from DDoS attacks and malevolent traffic. They use features like machine filters, two-factor authentication, etc. to tighten security.
10. Data Backups
It is always a good idea to keep backup files for important data in different devices to avoid loss. The chances of hardware malfunction and cyber-attacks are quite common in large companies. And thus having duplicate copies can be beneficial for the company.
11. Ecommerce Security Plugins
Security plugins ensure website protection from bad bots, SQLi, XSS, etc. by preventing malicious requests from reaching the website. They are easy to implement and highly secure to protect websites automatically.
12. Employee Training
The more educated the employees, the fewer chances of a security breach. Giving proper staff training can lead to better monitoring of the activities. They will know which policy or law is relevant according to the situation and will overcome the problem accordingly.
13. Track Malicious Activity
Ignorance often leads to smaller problems growing into huge ones. The same goes for malicious activities, if the company remains cautious and pays attention to every change, they can avoid security issues. A very tiny malicious activity when monitored from the start can save companies’ goodwill, revenues, and information.
14. Prioritize Updates
It is important to use the latest technology when dealing in e-commerce. The outdated software lacks better features to secure websites and portals which becomes an issue for the company. It is advisable to use updated security tools and plugins to avoid a serious liability.
15. Solid Ecommerce Platform
Having a secure e-commerce platform is very important as they have regular updates and security to safeguard the website. There are multiple options which are offering tools to prioritize website safety on the internet.
15. Perform a security audit
Just like a routine check-up, a regular examination of the website is very important. Companies should prioritize going through their security protocols on a weekly or monthly basis. This will allow them to identify any fault in the hosting before it’s too late.
16. Client Education
There are chances that many glitches or issues are coming from the client’s side. In this case, it is important for users to have proper knowledge about security and safety while using the internet. Because of them using weak passwords or unsecured networks, they end up facing consequences. This is the company’s responsibility to educate their customers about password creation, payment journey, network security, and many other things.
Conclusion
The internet and technology accessibility did open many ways for easier lifestyle but with a cost. These security threats are very serious and can cost a fortune to large companies if taken lightly. But this doesn’t mean that as a consumer you can ignore them.
You are equal shareholders of this cycle and thus responsible for your own safety. Following this set of instructions can help companies and consumers use the internet more securely and enjoy their privacy at the same time.
If you are Happy with DataFlair, do not forget to make us happy with your positive feedback on Google