SSH Protocol – Secure Shell
FREE Online Courses: Your Passport to Excellence - Start Now
SSH is a cryptographic network protocol that enables two computers to connect and share data over an unsecured network like the internet. It is used to log in to a remote server in order to execute instructions and transfer data from one system to another.
SSH communication security Ltd created the SSH protocol to provide safe communication with a distant system.
Secure communication encrypts communication with a public key across an unsecure channel and uses a strong password authentication. It replaces unprotected remote login protocols like TELNET, rlogin, rsh, and others, as well as insecure file transfer protocols like FTP.
Its security characteristics are commonly utilised by network administrators for remote management of systems and applications.
The SSH protocol protects a network against DNS spoofing, IP source routing, and IP spoofing attacks.
How SSH protects communications:
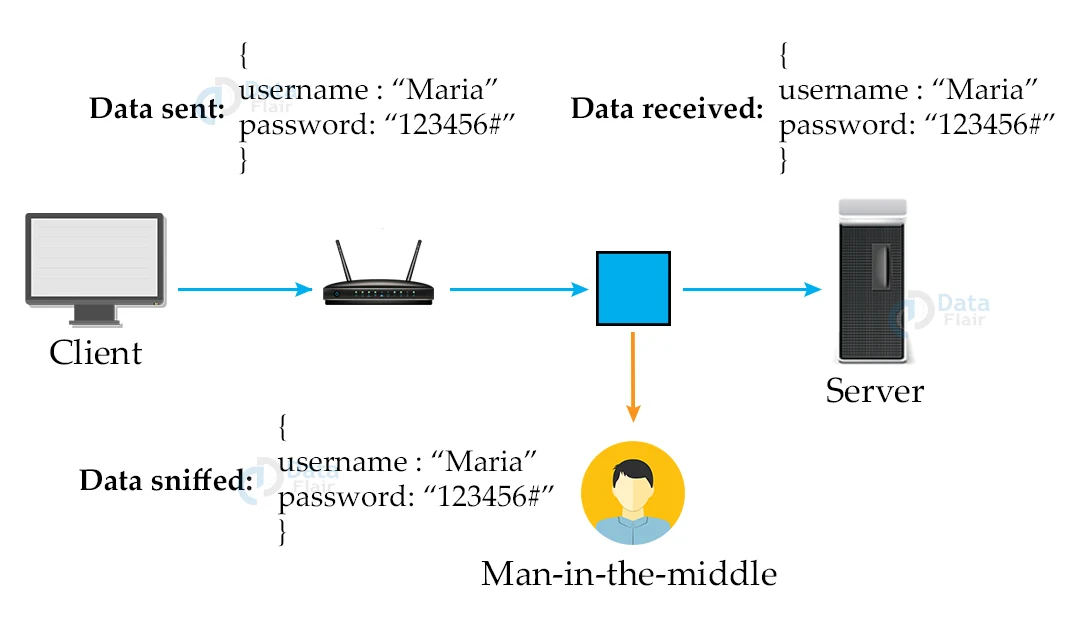
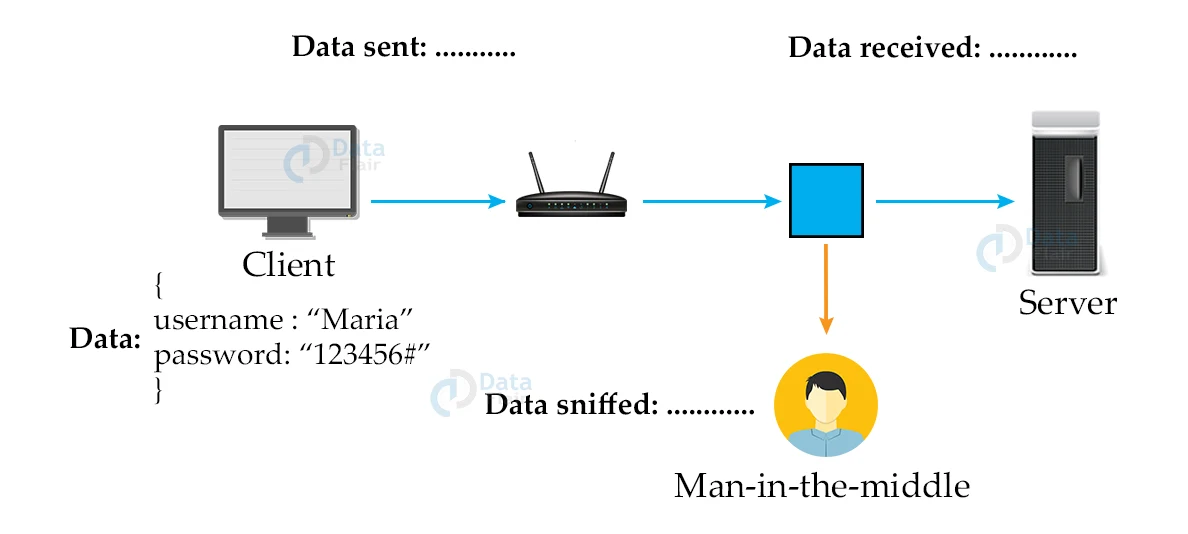
1. Before SSH:
2. After SSH:
Use of SSH Protocol:
1. It offers users safe access and automates procedures.
2. It is a simple and safe method of transferring files from one machine to another over an unsecured network.
3. It also gives users remote instructions.
4. It assists users in managing network infrastructure as well as other important system components.
5. It is used to log in to shell on a remote system (Host), replacing Telnet and rlogin, and to run a single command on the host, replacing rsh.
6. It works in tandem with the rsync software to backup, copy, and mirror files securely and efficiently.
7. It is capable of forwarding a port.
8. We can use SSH to automate the login to a remote server, such as OpenSSH.
9. We can safely access the web using the SSH client’s encrypted proxy connection, which supports the SOCKS protocol.
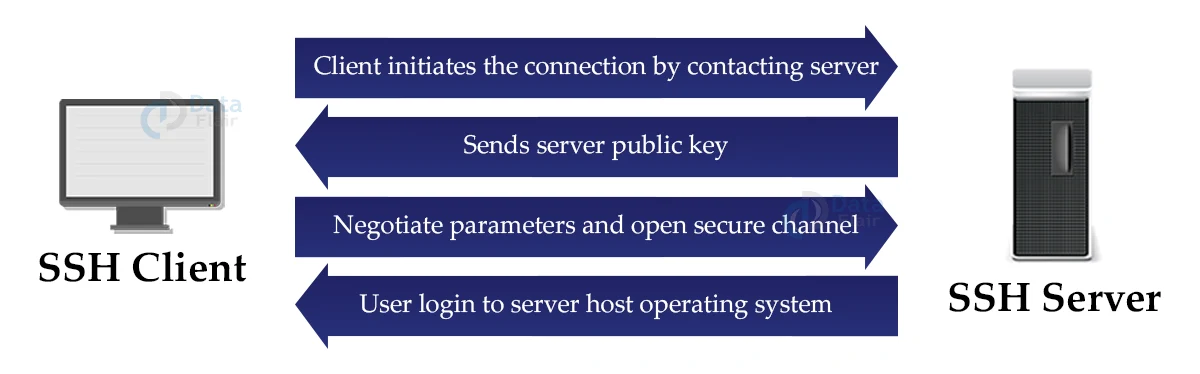
Working of SSH:
The SSH protocol operates on a client-server basis, which means it links a secure shell client programme (End where the session is shown) to the SSH server (End where session executes). It was designed to replace insecure login protocols such as Telnet and rlogin, and so fulfils the same job.
The command used to initiate an SSH connection is:
History of SSH Protocol:
There have been 3 versions of SSH –
1. Version 1.x:
The initial version of SSH was released in 1995 and was invented by Tatu Ylönen, a researcher at Finland’s Helsinki University of Technology. SSH-1 was the code name for it. There were various flaws with this version, therefore it was deprecated.
2. Version 2.x:
SSH-2, the current version of the SSH protocol, is the second version. The Internet Engineering Task Force selected it as a Standards Track standard in 2006. (IETF). This version does not support the SSH-1 protocol. It has more security features than SSH-1.
3. Version 1.99:
The prototype version of 2.1 is known as 1.99. It is not the actual version, but rather a method of determining backward compatibility.
Architecture of SSH Protocol:
Because the SSH protocol design is open, it gives enormous flexibility and allows SSH to be used for much more than just a secure shell. The transport layer is comparable to the transport layer security in the architecture (TLS). The user-authentication layer may be used with custom authentication techniques, and the connection layer allows for the multiplexing of several secondary sessions into a single SSH connection.
The SSH protocol is made up of 3 well-defined layers, which are –
1. Transport Layer:
The TCP/IP protocol suite’s top layer is the transport layer. This layer is in charge of managing initial key exchange, server authentication, encryption, compression, and integrity checking for SSH-2. It serves as an interface for transmitting and receiving plaintext packets of up to 32, 768 bytes in size.
2. User Authentication Layer:
The user authentication layer, as the name implies, is in charge of client authentication and offers a variety of authentication mechanisms. Because authentication is done on the client side, when a password prompt appears, it is normally for an SSH client rather than a server, and the server replies to these authentications.
The various methods of authentication used in this layer are:
a. Password:
Password authentication is a simple method of authentication. It has the option to alter the password for simple access. However, it is not used by all apps.
b. Public Key:
The public-key authentication mechanism is based on public keys and supports DSA, ECDSA, or RSA keypairs.
c. Keyboard-interactive:
It is one of the many authentication mechanisms available. In this case, the server provides a prompt for the user to input information, and the client responds with the user’s keyed-in replies. It is used to authenticate users with a one-time password or OTP.
d. GSSAPI:
External techniques, such as Kerberos 5 or NTLM, are used to conduct authentication in this approach, allowing SSH sessions to be accessed with a single sign-on.
3. Connection Layer:
The connection layer specifies the channels via which SSH services are delivered. It defines the terms “channels,” “channel requests,” and “global requests.” One SSH connection may host several channels at the same time and transport data in both ways at the same time.
In the connection layer, channel requests are used to broadcast out-of-band channel-specific data, such as the changed size of a terminal window or the exit code of a server-side process. The following are the connection layer’s standard channel types:
a. shell:
It is used for terminal shells, SFTP, and command execution.
b. direct-tcpip:
It is used for forwarded client-to-server communications.
c. forwarded-tcpip:
It is used for forwarded server-to-client communications.
Types of Data that can be transferred using SSH:
- Text
- Commands
- Files (Files are transmitted using SFTP – Secure File Transfer Protocol, which is an encrypted version of FTP)
Difference between SSH and TELNET:
1. Telnet was the first protocol that was used to establish and maintain a terminal session on a remote computer, using the internet.
2. SSH and Telnet both do the same functions. The difference between them is that the SSH protocol is protected by public-key cryptography, which authenticates the endpoint while establishing a terminal session. Telnet, on the other hand, does not enable authentication for user authentication, making it less secure.
3. SSH sends encrypted data, whereas Telnet sends plain text data.
4. SSH is the ideal protocol for public networks because of its strong security, but Telnet is suited for private networks due to its lower security.
5. SSH utilises port 22 by default, however this may be altered, whereas Telnet uses port 23, which is especially built for local area networks.
SSH Encryption Techniques:
1. Symmetrical Encryption:
In symmetric encryption systems, just one key may be used to encrypt and decode communications transmitted and received from the destination. Because both devices utilise the same key to encrypt and decode the data they send and receive, this approach is also known as shared key encryption.
To prevent man-in-the-middle attacks, this approach encrypts the whole SSH connection. One difficulty emerges during the initial key exchange in this approach. According to this issue, if a third party is present during the key exchange, they may know the key and read the full communication.
To avoid this issue, the Key exchange algorithm is utilised. The secret keys may be safely exchanged without being intercepted using this approach.
To implement the key exchange technique, asymmetrical encryption is necessary.
2. Asymmetrical Encryption:
Asymmetrical encryption employs two distinct keys for encryption and decryption: private and public keys. The private key is exclusively available to the user and cannot be shared with anyone else, but the public key is available to everyone.
The public key is stored on the SSH server, while the private key is stored locally on the SSH client; these two keys are known as a key pair. Only the associated private key may decode a communication encrypted with the public key.
It is a more secure strategy because if a third party obtains the public key, they will be unable to decrypt the message since they do not know the private key.
The SSH session is not encrypted because of the asymmetrical encryption. Instead, it is mostly utilised for the symmetric encryption key exchange technique. Before connecting, both systems (client and server) produce temporary public-private key pairs and then share their private keys to generate the shared secret key.
After establishing a secure symmetric connection, the server uses the public key to authenticate the client. Because the client can only decode the data if it possesses the private key, the SSH session is established.
3. Hashing:
SSH employs one-way hashing as an encryption mechanism, which is a kind of cryptography. The hashing approach differs from the previous two methods in that it is not intended for decryption. It creates the signature or information summary. SSH employs HMAC (Hash-based Message Authentication) to verify that communications arrive on their whole and unaltered.
Each transmitted message must have a MAC in this technology, which consists of three components: symmetric key, packet sequence number, and message content. These three components combine to construct the hash function, which generates a string with no meaning and sends it to the host. Because the host has the same information, they build a hash function as well, and if the resulting hash matches the received hash, the message is not tempered.
Summary:
In this article, we looked at the concept and functioning of the SSH protocol. We also looked at the types of data that can be transmitted by the SSH protocol, and also the architecture and different versions of SSH. We also looked at the different kinds of encryption techniques used by SSH, and also the difference between TELNET and SSH.
Your 15 seconds will encourage us to work even harder
Please share your happy experience on Google