Post Office Protocol in Computer Network
FREE Online Courses: Transform Your Career – Enroll for Free!
What is POP?
The POP protocol is an abbreviation for Post Office Protocol. As we all know, SMTP is a message transport agent. When a message is transmitted, SMTP is used to transfer it from the client to the server, and then to the receiving server.
However, the message is transmitted from the receiving server to the real server via the Message Access Agent. The Message Access Agent supports two protocols: POP3 and IMAP.
History of Post Office Protocol:
The internet engineering task force published the initial version of the post office protocol as RFC 918 in 1984. The POP3 protocol, which is used to get emails from the server, was created by the engineers as a simple and effective email system. This allows you to access your emails rather than your mailbox while you’re not connected to the internet.
POP version 2 came out in 1985, however it was replaced by POP version 3 with the release of RFC 1081 in 1988. POP3 was then updated over the following ten years until it was released. It was published in 1996 after it had been thoroughly polished.
Although the POP3 protocol has been improved in many ways, the essential premise that it follows a three-stage procedure during mail retrieval between the client and the server has not changed. They attempted to make this protocol as simple as possible, and it is because of this simplicity that it is so prevalent today.
Features of POP:
1. POP uses port 110.
2. It employs a Persistent TCP connection.
3. This is a type of pull protocol
4. It is a connection-oriented protocol
5. The POP protocol is a stateful protocol while downloading mail, later it is a stateless protocol.
Mechanism of Email Transmission in POP:
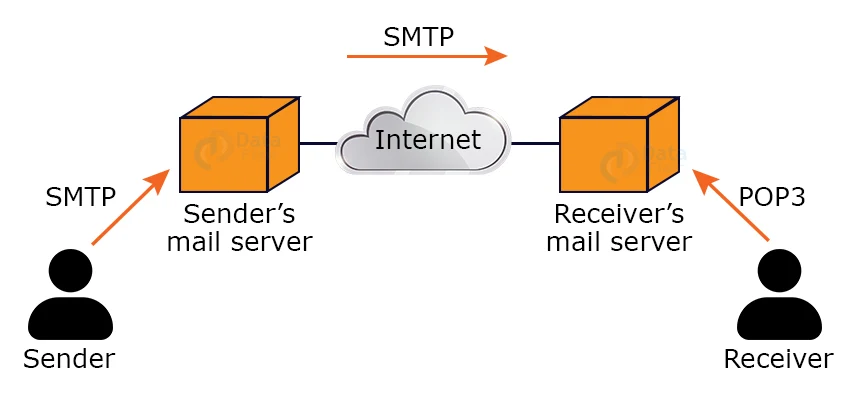
Assume the sender wishes to send the email to the recipient. The first email is sent to the sender’s mail server. The email is then sent across the internet from the sender’s mail server to the receiver’s mail server. When the mail arrives at the receiver’s mail server, it is forwarded to the user. The entire procedure is carried through using Email protocols.
The SMTP protocol is used to deliver email from the sender to the sender’s mail server and then to the receiver’s mail server. The POP or IMAP protocol at the receiver’s mail server receives the data and delivers it to the real user.
Because SMTP is a push protocol, it sends messages from the client to the server. SMTP sends the message from the client to the recipient’s mail server. The third step of email transmission necessitates the use of a pull protocol, and POP is one such protocol. When the message is sent from the recipient’s mail server to the client, it implies that the client is retrieving the mail from the server.
Working of POP:
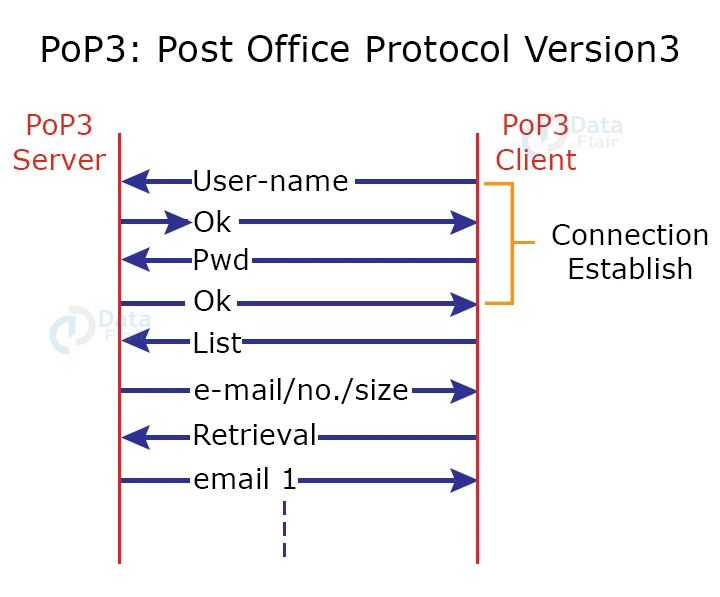
The POP3 server requests the user name from the POP3 client in order to establish a connection between the POP3 server and the POP3 client. If the username is discovered on the POP3 server, the ok message is sent. It then prompts the POP3 client for the password, which the POP3 client submits to the POP3 server. If the password is correct, the POP3 server delivers an OK message and the connection is created.
The client can view the list of mails on the POP3 mail server after establishing a connection. The server will return the email numbers and sizes to the user in the list of mails. The user can begin the mail retrieval process from this list.
Once the client has retrieved all of the emails from the server, the server’s emails are destroyed. As a result, we may argue that the emails are confined to a certain system, and accessing the same emails on another machine would be impossible. This problem may be solved by configuring the email settings to save a copy of the email on the mail server.
Advantages of POP:
1. It enables users to view their emails while they are not connected to the internet. It just requires an internet connection while downloading emails from the server. Once the emails are downloaded from the server, they are stored on our PC or hard drive, which may be read without using the internet. As a result, we may conclude that the POP3 protocol does not need continuous internet access.
2. It gives us quick and simple access to our emails because they are already on our computer.
3. There is no limit to the size of email that we may receive or send.
4. Because all emails are saved on the local computer, it takes less server storage space.
5. The mailbox has a maximum size, however it is restricted by the size of the hard disc.
6. Because it is a simple protocol, it is one of the most widely used protocols today.
7. It is simple to configure and use.
Disadvantages of POP:
1. When emails are downloaded from the server, they are automatically removed from the server. As a result, unless other workstations are set to leave a copy of the message on the server, mails cannot be accessed from other machines.
2. Transferring the mail folder from one machine to another might be challenging.
3. Because all of the attachments are saved on your local system, there is a significant danger of a malware attack if they are not scanned by a virus scanner.
4. The downloaded email folder from the mail server may potentially get damaged.
5. Because the emails are kept on the local system, anybody who uses your computer can view the email folder.
Commands used in POP:
- LOGIN – This command is used to establish a connection.
- STAT – This command displays all of the mails that are currently in the mailbox.
- DELE – This command is used to remove a message from the system.
- RSET – This command is mostly used to return the session to its default state.
- QUIT – This command is used to log the user out of the session.
- LIST – This command is mostly used to obtain the summary of each message, where the summary of each message is displayed.
- RETR – This command is mostly used to pick a mailbox from which to access messages.
Summary:
In this article, we explored the concept and working of the Post Office Protocol (POP). We looked at the various steps involved in the usage of POP, as well as some of the commands associated with it. We also looked at the advantages and disadvantages of POP.
Your opinion matters
Please write your valuable feedback about DataFlair on Google