Penetration Testing Stages, Methods and Types
FREE Online Courses: Elevate Your Skills, Zero Cost Attached - Enroll Now!
Penetration Testing has become an important tool in the department of cybersecurity. It is a simulated cyberattack that is effective in identifying exploitable vulnerabilities. This is applicable for testing devices, systems, applications, servers, networks, and much more.
The tester may opt for breaching multiple application systems, servers, and devices to uncover vulnerabilities. The tester works on “exploits” to identify such threats and see inputs that are susceptible to code injection attacks. Knowing such input comes with relevant experience and education.
The exploits act as an insight for the tester to follow the process further. Both hackers and testers work to get these exploits but having the first-mover advantage is better for security. And this method of testing also aligns with government regulation and standards, becoming more reliable for the companies.
This method of testing allows consistent and self-initiated improvements according to the assessment report. This is not a non-proactive approach that works when the threats are on the face. It is more like a precautionary tool to make security stronger inside the organization.
Benefits of Penetration Testing
- Sectors dealing with confidential information need to secure their data and having this test can help them do so.
- To identify persistent threats in case the company faces an attack. This can help them to remove such viruses and secure data.
- It allows security against hackers.
- It helps in identifying weaknesses in systems.
- This also helps to determine the robustness of controls.
- It aligns with security regulations like PCI DSS, HIPAA, GDPR, etc.
- It allows companies to set a budget for future cybersecurity.
Role and Responsibilities of Penetration Testers
- Research about the organization’s information necessary to carry out the test.
- Identify weaknesses that hackers will have in the system.
- Act like a real attacker and not ethically.
- Produce work that the company can refer to in the future as well.
- Design the duration of the test in advance.
- Take responsibility for any sort of loss during the testing.
- Keep all data and information confidential at all costs.
The pen testing should be done by someone outside the organization. Because they bring in a new perspective and skills to identify threats. There are many ethical hackers who engage in such testing, they are the right fit for it.
Areas of Pen Testing
1. Web Application
Testing for web applications includes testing the overall security and potential risks of the target system. This includes coding errors, broken authentication, and injection vulnerabilities.
2. Network Security
Network penetration testing works on identifying vulnerabilities on different types of networks, devices, and hosts. The tester exploits these areas to gain access to critical systems.
3. Cloud Security Tests
The testers work with cloud providers to test cloud-based systems and applications. They work on cloud deployment, overall risk, and different vulnerabilities. Testers also recommended certain measures to improve the cloud environment.
4. IoT Security Tests
Testers look into different IoT devices and their components before running the test. They follow a layered methodology, analyzing each layer to identify weaknesses.
5. Social Engineering
Testers use deception to get information access. This is mainly done by using phishing tools to test the company’s defense mechanisms, detection, and reaction.
Five Stages of Penetration Testing
1. Planning and reconnaissance
The first stage of the process is to identify the goals and define the scope of work. This includes the method of testing and system address as well. Then the task is to gather intelligence (data) to see potential vulnerabilities.
2. Scanning
This step works on identifying the impact intrusion will have on the target application. There are two ways to do this step – static analysis and dynamic analysis. Static analysis inspects the application’s code in a single pass to see its behavior while stationary. Dynamic analysis sees the application’s code in a running state to get a real-time perspective.
3. Gaining Access
This step involves using web application attacks to exploit the vulnerabilities like in real critical situations. This may be by cross-site scripting, SQL injection, etc. and see what kind of damage they can do. Sometimes, testers also steal and corrupt data to get a better understanding.
4. Maintaining access
Testers are aware of persistent threats and how they can affect the data. To get a sense of it, they try to maintain access for a long time to see how hackers can exploit it. Persistent threats stay in the system for months and this step works to overcome such situations.
5. Analysis
The above steps are then compiled into one report which goes to the security team for future reference. It includes specific vulnerabilities, sensitive data access, access duration, and a few recommendations.
Three Steps to Consider After a Pen Test
1. Reviewing and discussing the analysis. It is very important after step to ensure that the results of the pen test don’t go to waste. The upper-level management and the security team should work together and review what the results are and what led to these situations. This can help them identify qualitative and quantitative risks.
2. Develop a recovery plan and implement it before a retest. It is important to draw a conclusion from testing the security. Companies must make up plan to overcome this weak point and validate their planning with a retest. Taking a retest will ensure that their plan is strong enough to control the entire situation.
3. The most important step, include this plan in your long-term regulation. These results show the situation of the company at some point and definitely impact its future. Including them in their long-term approach can ensure that employees know how to take care of it in the best possible way.
How Often Should You Pen Test?
Penetration testing should be performed on a regular basis to ensure more consistent IT and network security management. A pen-tester will reveal how newly discovered threats or emerging vulnerabilities may potentially be assailed by attackers. In addition to regularly scheduled analysis and assessments required by regulatory mandates, tests should also be run whenever there is –
- Addition of new application
- Change in network infrastructure
- Application of security patches
- Upgradation of application or infrastructure
- Modification of end-user policy
- Change in the office location
Penetration Testing Methods
1. External testing
This method is useful for testing assets of the company accessible on the internet. Web applications and websites are typical examples of this. Testers try to break in from outside to gain access and extract valuable data.
2. Internal testing
This method is to test the application from the back end i.e. behind its firewall. Testers act as malicious insiders and then attack the applications. It may not be an employee necessarily but any other stakeholder who lost her credentials.
3. Blind testing
In this case, testers just know the name of the company they have to test. They do their research on the company and attack them as a real hacker. This allows the security team to understand how a real-time attack would look like.
4. Double-blind testing
This is a good method to test a company’s preparation for a cyber attack. The tester gets the name of the company without the knowledge of the security team. And when the tester attacks, the security team thinks it to be a real attack.
5. Targeted testing
This method requires the tester and the security team to coordinate and test the security. It is more like a training session where they anticipate how an attack would unfold. They get a perspective of both parties as part of the attack.
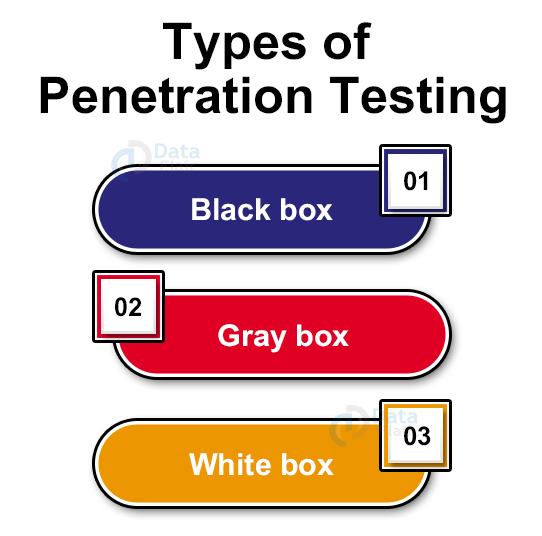
Types of Penetration Testing
1. Black box
The testers are not aware of the internal system of the company. They attack from the outside and go for externally exploitable weaknesses.
2. Gray box
The testers may have information about some credentials and data structure. They conduct the test with all this information like an insider.
3. White box
The testers have full information about the company’s security system. This allows them to conduct the test is very little time and provides the highest level of assurance.
Penetration testing and web application firewalls
Penetration testing and WAFs are very important security measures that go hand in hand. Testers usually go for WAD data and its weak point to perform the test. This allows WAF administrators to benefit from it as they can make the weak points stronger.
Difference between Pen testing and Vulnerability assessment
Pen tests and vulnerability assessments are two different methods to identify potential threats. The tester may perform them together due to more accurate results. But pen testing is very specific to an objective like –
1.Identify hackable systems
2.Attempt to hack a specific system
3.Carry out a data breach
Most of the objectives fall under these categories only. And testers keep them in mind before initiating an attack.
Manual Penetration vs. Automated Penetration Testing
| Manual Penetration Testing | Automated Penetration Testing |
| Expert engineers are the ones conducting the test. | The test is conducted by automated software. |
| Needs different testing tools | Have integrated tools |
| Results vary from test to test | Has fixed result. |
| Needs to remember cleaning up memory | Not necessary |
| Exhaustive and time taking | Efficient and fast |
| Better analysis due to professional involvement | Doesn’t analyze at all |
| Experts can undertake multiple testing. | Can conduct one test at a time |
| More reliable | Less reliable |
Top pen-testing tools
There are several cybersecurity tools available online. All of them have their advantages and features. Some of the top pen-testing tools are –
- Kali Linux
- nmap
- Metasploit
- Wireshark
- John the Ripper
- Hashcat
- Hydra
- Burp
- Zed Attack Proxy
- sqlmap
- Aircrack-ng
- Suite
Compliances and Pen Testing
Pen testing aligns with many cybersecurity standards allowing companies to stay under regulations. Some of them are –
- HIPAA
- PCI DSS
- SOX
- NERC
- HEOA
- GDPR
- CMMC
Testers undergo this extensive process to see how the company will face such attacks. While the major objective is to see the real-time attack process, testers also check if companies are following the regulations or not. Many of the above standards make it mandatory for companies to do pen testing as part of regular security audits.
What Is Teaming?
Teaming is a way of dividing testers into groups of people to simulate real-life attack scenarios. There are three types of team in this process –
1. Red Teams
The red team is made of the offenders who identify the limitations and attack the organization. They assess vulnerabilities, test assumptions, and then reveal the information.
2. Blue Teams
The blue team is made of the defenders who come up with protective measures to tackle the situation.
3. Purple Teams
This is where lines between the blue and red teams become a blur. They both work together with a common objective to improve security. This team solely functions on the basis of communication and coordination.
Disadvantages of Penetration Testing
- Cannot identify all vulnerabilities
- Limitations of time
- Lack of Testing skills
- Data Loss and Corruption
- Down Time
- Increase Costs
Conclusion
Being an IT professional is a tough job as you deal with sensitive data all the time. This makes it important for you to have proper knowledge of security measures and security tools. Knowing what works the best for the company can help you save resources and goodwill. Pen testing is one such tool that is highly beneficial for cybersecurity. This information will allow you to make a more well-informed decision in the field of cybersecurity.
Your 15 seconds will encourage us to work even harder
Please share your happy experience on Google