Multiple Access Protocols
FREE Online Courses: Click for Success, Learn for Free - Start Now!
What is Multiple Access Protocol?
The data link control is sufficient to handle the channel when a sender and receiver have a dedicated link for transmitting data packets. Assume there is no dedicated communication or data transfer path between two devices. In this case, multiple stations access the channel and transmit data over it at the same time. It could result in collisions and cross-talk. As a result, the multiple access protocol is required to reduce channel collisions and avoid crosstalk.
Types of Multiple Access Protocols:
1. Random Access Protocol:
In this protocol, all stations have the same priority when it comes to sending data over a channel. One or more stations cannot rely on another station, and no station can control another station in the random access protocol. Each station transmits the data frame based on the state of the channel (idle or busy). However, if more than one station sends data over the same channel, a collision or data conflict may occur. The data frame packets may be lost or changed as a result of the collision. As a result, the receiver end does not receive.
Types of Random Access Protocols:
a. Aloha:
It is intended for use in a wireless LAN (Local Area Network), but it can also be used to transmit data over a shared medium. When a data frameset is available for transmission, any station can transmit data across a network simultaneously using this method.
Aloha Rules:
- At any time, any station can transmit data to a channel.
- It does not necessitate the use of carrier sensing.
- During the transmission of data through multiple stations, collisions and data frames may occur.
- In Aloha, there is acknowledgement of the frames. As a result, no collision detection is possible.
- It necessitates data retransmission after a set period of time.
Types of Aloha:
1. Pure Aloha:
We use Pure Aloha whenever data is available for sending over a channel at stations. When each station transmits data to a channel without first checking whether the channel is idle or not, there is a risk of collision and the data frame being lost in pure Aloha.
The pure Aloha waits for the receiver’s acknowledgment when any station transmits a data frame to a channel. The station waits for a random amount of time, called the backoff time, if it does not acknowledge the receiver end within the specified time (Tb). It’s possible that the station will assume the frame has been misplaced or destroyed. As a result, the frame is retransmitted until all of the data is successfully transmitted to the receiver.
For accessing a shared channel and transmitting data frames, there are four stations. Because most stations send their frames at the same time, some frames collide. Only two frames, frame 1.1 and frame 2.2, reach the receiver end successfully. Other frames are lost or destroyed at the same time.
When two frames arrive on a shared channel at the same time, collisions can occur, causing damage to both. If the first bit of the new frame enters the channel before the last bit of the previous frame. Both frames are complete, and the data frame must be retransmitted by both stations.
Vulnerable Time = 2*(Frame Transmission Time)
Maximum Throughput (G=1/2) = 18.4%
Probability of successful transmission of data frame = G * e ^ – 2 G
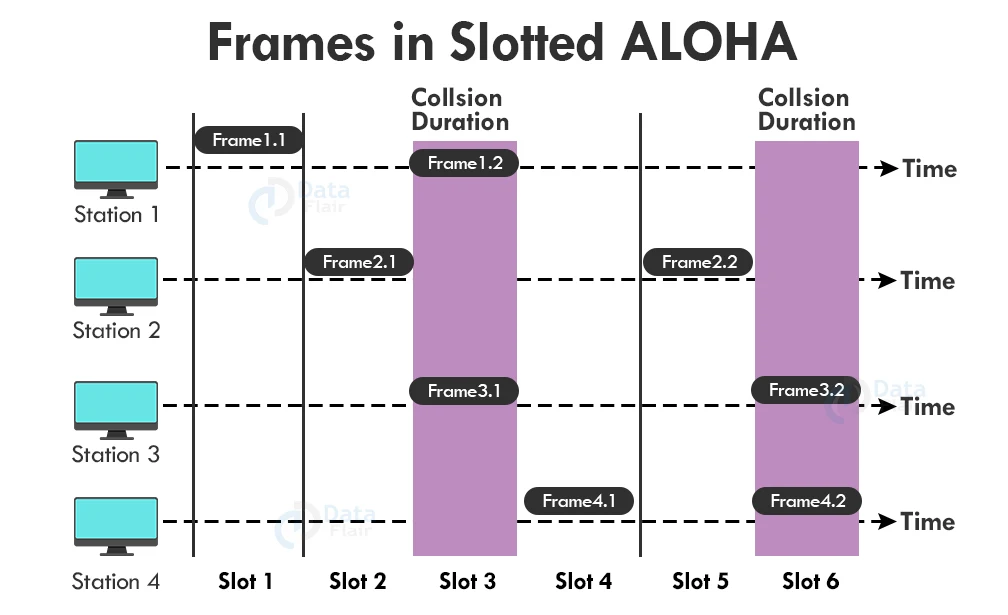
2. Slotted Aloha:
The slotted Aloha was created to counteract the pure Aloha’s efficiency, as pure Aloha has a high chance of hitting the frame. The shared channel in slotted Aloha is divided into fixed time intervals called slots. As a result, if a station wants to send a frame to a shared channel, it can only do so at the start of the slot, and only one frame per slot is allowed.
If the stations are unable to send data to the start of the slot, they will have to wait until the start of the slot the next time. When sending a frame at the start of two or more station time slots, however, the possibility of a collision remains.
Vulnerable Time = Frame Transmission Time
Maximum Throughput (G=1) = 37%
Probability of successful transmission of data frame = G * e ^ – 2 G
b. CSMA:
Before transmitting data, carrier sense multiple access uses the media access protocol to detect traffic on a channel (idle or busy). It means that the station can send data to the channel even if it is idle. Otherwise, it will have to wait until the channel is free. As a result, the chances of a collision on a transmission medium are reduced.
CSMA Access Modes:
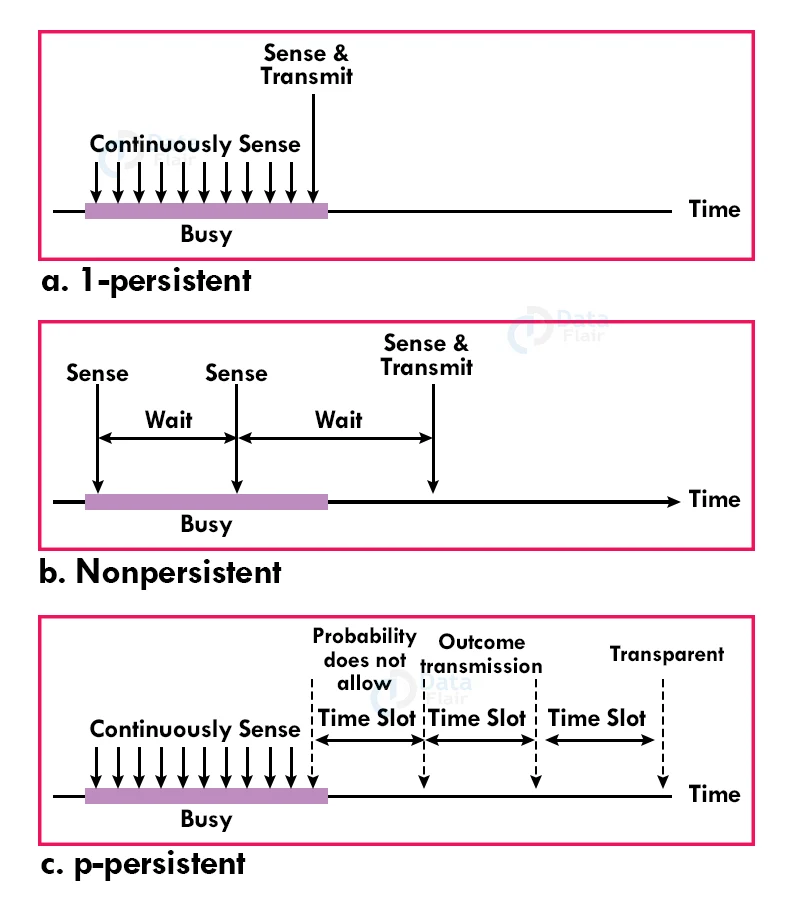
1. 1-Persistent:
Each node in the 1-Persistent mode of CSMA first senses the shared channel, and if the channel is idle, it sends the data immediately. Otherwise, it must wait for the channel to become idle and broadcast the frame unconditionally as soon as the channel becomes idle.
2. Non-Persistent:
It is the access mode of CSMA that defines before transmitting the data, each node must sense the channel, and if the channel is inactive, it immediately sends the data. Otherwise, the station must wait for a random time (not continuously), and when the channel is found to be idle, it transmits the frames.
3. P-Persistent:
It is the combination of 1-Persistent and Non-persistent modes. The P-Persistent mode defines that each node senses the channel, and if the channel is inactive, it sends a frame with a P probability. If the data is not transmitted, it waits for a (q = 1-p probability) random time and resumes the frame with the next time slot.
4. O-Persistent:
It is an O-persistent method that defines the superiority of the station before the transmission of the frame on the shared channel. If it is found that the channel is inactive, each station waits for its turn to retransmit the data.
c. CSMA/CD:
To transmit data frames, it is a carrier sense multiple access/ collision detection network protocol. A medium access control layer is used with the CSMA/CD protocol. As a result, it detects the shared channel first before broadcasting the frames, and if the channel is idle, it sends a frame to verify that the transmission was successful.
The station sends another frame if the first one is successfully received. If a CSMA/CD collision is detected, the station sends a jam/stop signal to the shared channel, effectively stopping data transmission. It then waits for an unknown amount of time before sending a frame to a channel.
d. CSMA/CA:
For carrier transmission of data frames, it is a carrier sense multiple access/collision avoidance network protocol. It’s a protocol that uses a medium access control layer to operate. When a data frame is sent to a channel, it is acknowledged in order to determine whether the channel is clear. The data frame has been successfully transmitted to the receiver if the station receives only one (own) acknowledgment.
However, if it receives two signals (it’s own achnowledgement and another in which frames collide), a frame collision occurs in the shared channel. When a sender receives an acknowledgment signal, it detects the frame colliding.
Methods to avoid collisions used in CSMA/CA:
1. Interframe Space:
In this method, the station waits for the channel to become idle, and if it gets the channel is idle, it does not immediately send the data. Instead of this, it waits for some time, and this time period is called the Interframe space or IFS. However, the IFS time is often used to define the priority of the station.
2. Contention Window:
In the Contention window, the total time is divided into different slots. When the station/ sender is ready to transmit the data frame, it chooses a random slot number of slots as wait time. If the channel is still busy, it does not restart the entire process, except that it restarts the timer only to send data packets when the channel is inactive.
3. Acknowledgement:
In the acknowledgment method, the sender station sends the data frame to the shared channel if the acknowledgment is not received ahead of time.
2. Controlled Access Protocols:
It’s a technique for preventing data frames from colliding on a shared channel. In the controlled access method, each station communicates with one another and decides whether or not to send a data frame that has been approved by all other stations. It means that a single station cannot send data frames unless all other stations have refused to send them.
Reservation, Polling, and Token Passing are the three types of controlled access available.
3. Channelization Protocols:
Methods to implement channelization protocols:
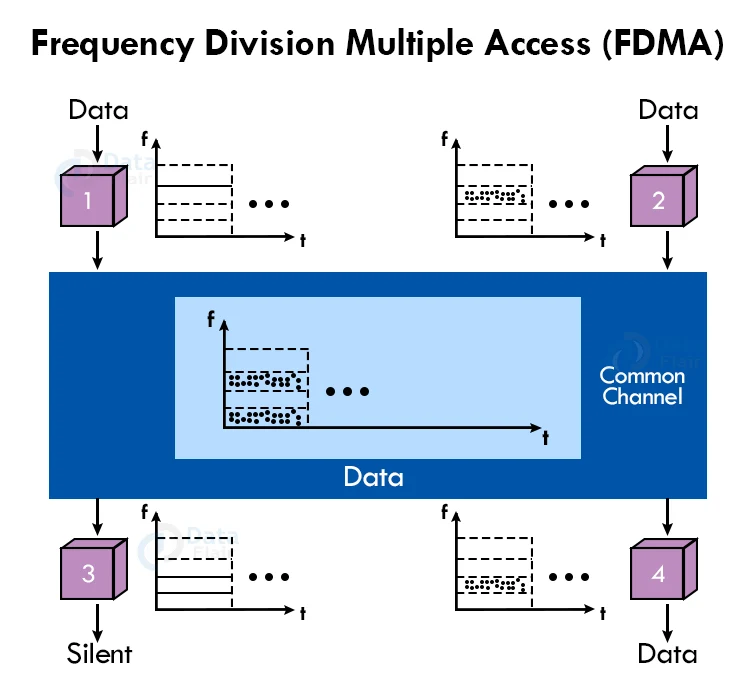
a. Frequency Division Multiple Access (FDMA):
It is a method that divides the available bandwidth into equal bands so that multiple users can send data to the subchannel using different frequencies. To prevent crosstalk between channels and station interference, each station is assigned to a specific band.
b. Time Division Multiple Access (TDMA):
TDMA allows multiple stations to share the same frequency bandwidth. It also divides the shared channel into different frequency slots that assign stations to transmit data frames to avoid collisions. By dividing the signal into various time slots to transmit it, the same frequency bandwidth can be shared over a shared channel.
However, TDMA has a synchronisation overhead that adds synchronisation bits to each slot to specify each station’s time slot.
c. Code Division Multiple Access (TDMA):
A channel access method is code division multiple access (CDMA). In CDMA, all stations can send data over the same channel at the same time. It means that each station can transmit data frames on the shared channel at full frequency at all times. It does not necessitate the use of time slots to divide bandwidth on a shared channel.
A unique code sequence separates the data frames of multiple stations sending data to the same channel at the same time. For data transmission over a shared channel, each station has its own unique code.
In a room, for example, there are multiple users who are constantly speaking. When only two people interact with each other using the same language, data is received by the users. Similarly, if different stations in the network communicate with each other at the same time using different code languages, the network will be disrupted.
Summary:
In this article, we explored the concept of Multiple Access Protocols. We looked at the various types of multiple access protocols, as well as the various subtypes within them.
You give me 15 seconds I promise you best tutorials
Please share your happy experience on Google