ICMP Protocol – Internet Control Message Protocol
FREE Online Courses: Elevate Skills, Zero Cost. Enroll Now!
The Internet Control Message Protocol (ICMP) stands for Internet Control Message Protocol. It’s a protocol for the network layer. It is primarily used on network devices such as routers for error handling in the network layer. Because various types of errors can occur at the network layer, ICMP can be used to report and debug these errors.
For example, a sender might want to send a message to a particular destination, but the router is unable to do so. In this case, the router informs the sender that the message could not be delivered to that destination.
Because the IP protocol lacks an error-reporting or error-correcting mechanism, it relies on messages to convey data. If someone sends a message to the destination, for example, the message is stolen in some way between the sender and the recipient. If no one reports the error, the sender may believe the message has arrived at its intended location. Also, if someone in the middle reports the error, the sender will quickly resend the message.
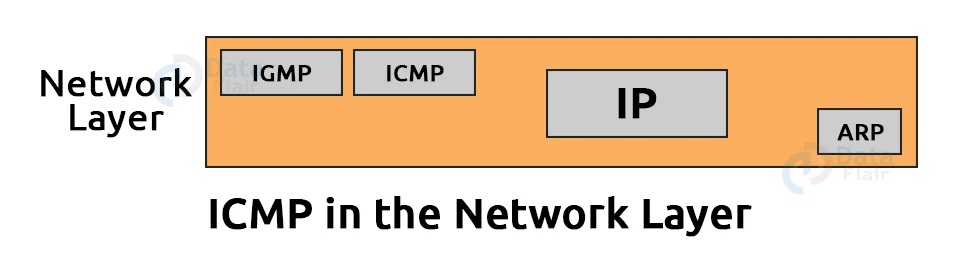
ICMP in the Network Layer:
ICMP is part of the IP Layer, as illustrated by the image:
Messages:
There are two types of ICMP Messages:
1. Error-reporting messages:
The error-reporting message indicates that when the router encounters a problem while processing an IP packet, it will send a message.
2. Query messages:
Query messages are those that assist the host in obtaining specific information from another host. Let’s say there’s a client and a server, and the client wants to know if the server is up and running. It sends an ICMP message to the server to find out.
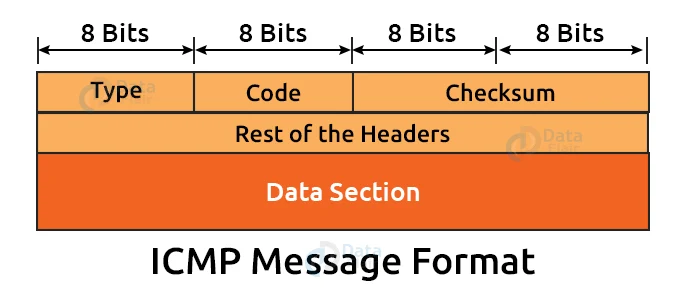
ICMP Message Format:
1. Type:
It’s a field with an 8-bit value. It specifies the type of ICMP message. ICMPv6 has values ranging from 0 to 127, and informational messages have values ranging from 128 to 255.
2. Code:
It’s an 8-bit field that specifies the ICMP message’s subtype.
3. Checksum:
It’s a 16-bit field that determines whether or not the message contains an error.
Types of error-reporting messages:
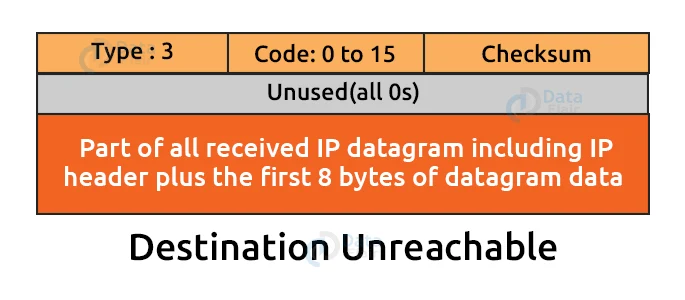
1. Destination Unreachable:
When a packet fails to reach its intended destination, the destination unreachable error occurs. If the sender sends a message but it does not reach its intended destination, the intermediate router will inform the sender that the destination is unavailable.
a. Type:
It specifies the message’s type. The number 3 indicates that the location is inaccessible.
b. Code (0 to 15):
It’s a four-bit number that indicates whether the message came from an intermediate router or directly from the destination.
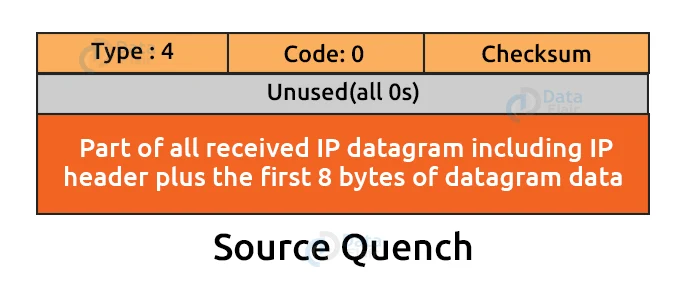
2. Source Quench:
The network layer and the IP protocol have no flow control or congestion control mechanisms. There is no flow control or congestion control mechanism because the sender is only concerned with sending packets. The sender is not concerned with whether the receiver is ready to receive those packets or whether there is any congestion in the network layer so that the sender can send a smaller number of packets.
In this case, ICMP provides source quench as feedback. Assume the sender resends the packet at a faster rate, and the router is unable to cope with the increased data rate. To deal with this, the router sends a source quench message to the sender, instructing them to send the packet at a slower rate.
Until the congestion is relieved, the sender must either stop or slow down datagram transmissions. For each datagram that is discarded due to network layer congestion, the router sends one source-quench message.
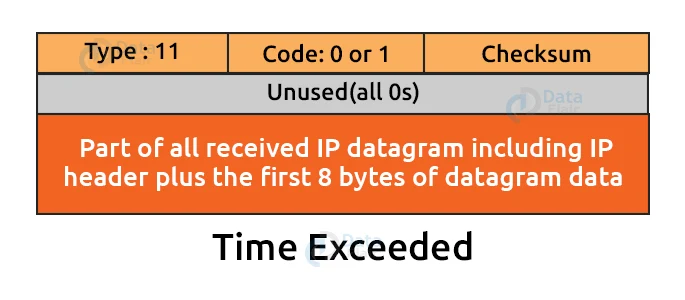
3. Time Exceeded:
When there are multiple routers between the sender and the receiver, the situation can become complicated. After the sender sends the packet, it is routed through a loop. The time-to-live value is used to determine how much time has passed.
When a packet passes through a router, the TTL value is reduced by one at each router. When a router reduces the time-to-live value of a datagram to zero, the datagram is discarded and the time exceeded message is sent to the original source.
Each MAC layer has its own set of data units. Some layers, for example, can handle up to 1500 data units, while others can only handle 300.
When a packet is sent from a layer with 1500 units to a layer with 300 units, the packet is fragmented; this process is known as fragmentation. These 1500 units are divided into five fragments, f1, f2, f3, f4, and f5, which arrive at the destination in order. They discard all received fragments and send a time-exceeded message to the original source if all fragments do not arrive at the destination within a certain amount of time.
The code will be different from TTL in the case of fragmentation.
Example:
The type of time-exceeded is 11 in the above message format, and the code can be 0 or 1. TTL is represented by code 0, and fragmentation is represented by code 1. The code 0 is used by routers in a time-exceeded message to indicate that the time-to-live value has been reduced to zero.
The destination uses code 1 to indicate that all of the fragments did not arrive within a certain amount of time.
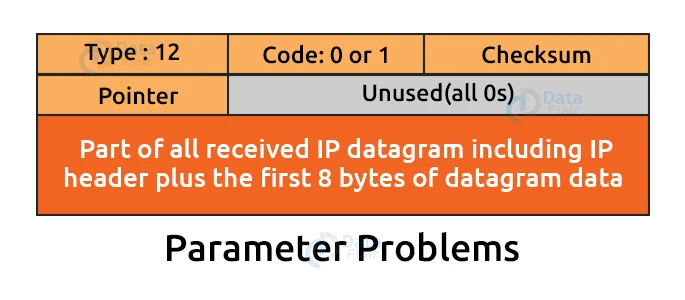
4. Parameter Problems:
A parameter problem message can be sent by both the router and the destination host. This message indicates that some parameters have been misconfigured.
The type of message is 12, and the code can vary between 0 and 1.
5. Redirection:
The routing table is gradually augmented and updated as the packet is sent. The redirection message is the tool that is used to accomplish this. For example, suppose A wants to send a packet to B, and A and B are separated by two routers. A sends the data to router 1 first. The IP packet is sent to router 2 along with a redirection message to A, allowing A to update its routing table.
ICMP Query Messages:
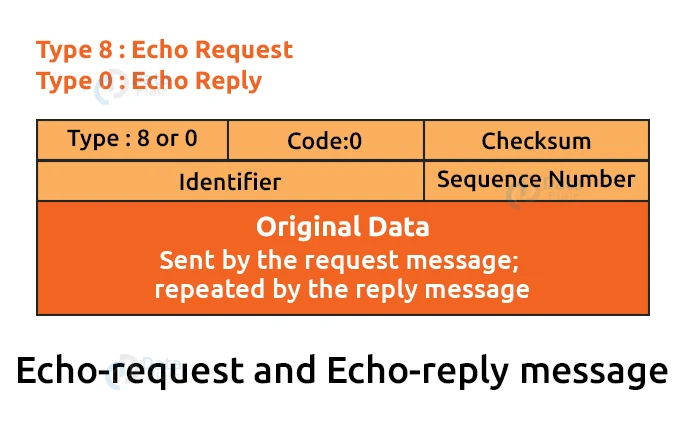
1. Echo-request and echo-reply message:
An echo-request message can be sent by a router or a host. It’s used to send a “Are you alive?” message to another host. If the other host is still alive, the echo-reply message is sent. The router or the host that receives an echo-request message sends an echo-reply message.
Network administrators can use the echo-request and echo-reply messages to test the IP protocol’s functionality. Assume there are two hosts, A and B, and A wishes to communicate with B. If the link between A and B is not broken and B is still alive, A can communicate with B.
The echo-request and echo-reply messages use the ping command to determine whether or not the host is reachable.
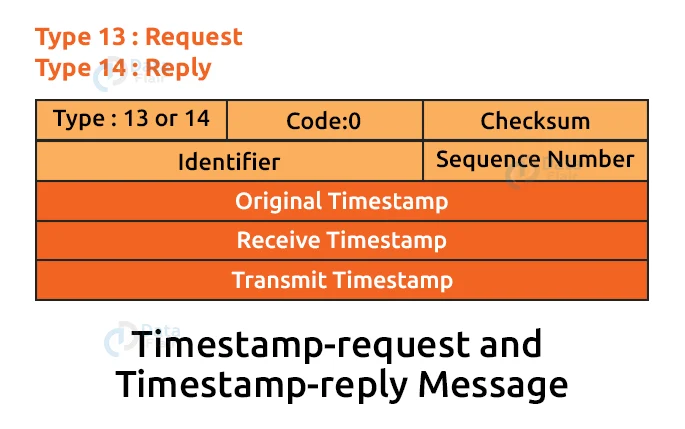
2. Timestamp-request and timestamp-reply message:
Query messages include the timestamp-request and timestamp-reply messages. If computer A wants to know what time it is on computer B, it sends a timestamp-request message to that computer. A timestamp-reply message is sent from computer B.
Even if the clocks are not synchronised, it can be used to calculate the round-trip time between the source and the destination.
If the exact transit time is known, it can also be used to synchronise the clocks in two different machines.
ICMP Debugging Tools:
1. Traceroute:
Traceroute is a tool that follows a packet’s path from source to destination on an IP network. It keeps track of how long the packet spends on each hop on its way from source to destination. ICMP messages and TTL values are used by Traceroute. The TTL value is determined, and if it reaches zero, the packet is discarded.
Traceroute uses short TTL values because they expire quickly. The message is produced by router 1 if the TTL value is 1; if the TTL value is 2 then the message is produced by router 2, and so on.
Example:
Assume A and B are two hosts, and A is looking to send a packet to B. There are 3 routers between A and B. The traceroute commands functions as follows:
a. TTL Value=1:
To begin, host A sends a packet to router 1 with a TTL value of 1, and when the packet arrives at router 1, the router reduces the TTL value by one, and the TTL values become 0. Router 1 generates the time-exceeded message in this case, and host A learns that router 1 is the first router in the path.
b. TTL Value=2:
When host A sends a packet to router 1 with TTL value 2, the TTL value is decremented by one when the packet reaches router 1, and the TTL value becomes 1. The packet is then sent to router 2, and the TTL value is set to 0, causing the router to generate a time-exceeded message. The host A discovers that router 2 is the path’s second router.
c. TTL Value=3:
When host A sends a packet to router 1 with a TTL value of 3, the router subtracts one from the value, making the TTL value 2. The packet is then sent to router 2, and the TTL value is set to 1. The packet is then sent to router 3 by router 2, and the TTL value is set to 0. Router 3 generates a time-exceeded message when the TTL value reaches 0. Host A is the third router on the path in this case.
Summary:
In this article, we explored the concept of the Internet Control Message Protocol (ICMP) in detail. We looked at the working of the ICMP protocol, as well as the various different types of messages that it is associated with. We also looked at the message format of ICMP messages.
We work very hard to provide you quality material
Could you take 15 seconds and share your happy experience on Google