Digital Signature in Computer Network
FREE Online Courses: Enroll Now, Thank us Later!
The Digital Signature is a mechanism used to authenticate the message’s validity and integrity. We know that security has four components: privacy, authentication, integrity, and non-repudiation. The first component of security has previously been covered, and the other three may be achieved by employing a digital signature.
The core concept of a Digital Signature is to sign a document. We can sign a document when we transmit it electronically. We can sign a document in two ways: as the entire document or as a digest.
How do Digital Signatures work?
Digital signature solution providers will produce two keys: a public key and a private key, using a mathematical procedure. When a signer digitally signs a document, a cryptographic hash of the document is created.
That cryptographic hash is then encrypted using the sender’s private key, which is kept safe in an HSM box. It is then added to the document and delivered together with the sender’s public key to the recipients.
With the sender’s public key certificate, the recipient may decode the encrypted hash. On the recipient’s end, a cryptographic hash is created once again.
To verify its legitimacy, the cryptographic hashes are compared. If they match, the document has not been tampered with and is genuine.
Why should you use a Digital Signature?
A digital signature’s security is dependent on how effectively the private key is safeguarded. It is difficult to prove someone’s identity or revoke a compromised key without PGP; this might allow people to impersonate someone without any way of validation.
Digital signatures may be used to identify and authenticate persons as well as assure the message’s integrity when used in conjunction with a trusted third party.
Important Terms Related to Digital Signature
1. Encryption – The process of turning electronic data into ciphertext, which is incomprehensible to everyone but the authorised parties. This ensures the security of data.
2. Decryption – Decryption is the process of converting code to data.
The communication is encrypted at the sender’s end using various encryption techniques and decoded at the receiver’s end using decryption methods.
When a communication, such as a login or password, has to be kept confidential, encryption and decryption procedures are employed to ensure data security.
Encryption Types
1. Symmetric Encryption – Data is encrypted with a key and decrypted using the same key.
2. Asymmetric Encryption – Public-key cryptography is another name for asymmetric encryption. It encrypts and decrypts data using public and private keys. The public key is the one key in the pair that may be shared with everyone. The private key is the other key in the pair that is kept secret and only known by the owner. Either key can be used to encrypt a message; the opposite key used to encrypt the message is used to decode it.
3. Public Key – A key that everyone has access to.
4. Private key – A key that is known exclusively to the person whose private key it is.
5. Authentication – Any procedure by which a system checks the identity of a person who desires to access it is referred to as authentication.
6. Non-repudiation – To verify that a transmitted message was sent and received by the parties claiming to have sent and received the message, non-repudiation is used. Non-repudiation is a method of ensuring that the sender of a communication cannot subsequently dispute sending the message and that the recipient cannot deny receiving the message.
7. Integrity – In this we ensure that the message was not tampered with during transmission.
8. Message digest – This is text in the form of a single string of numbers generated with the help of a one way hash function. The process of encrypting a message digest with a private key creates a digital signature.
What does signing a document mean?
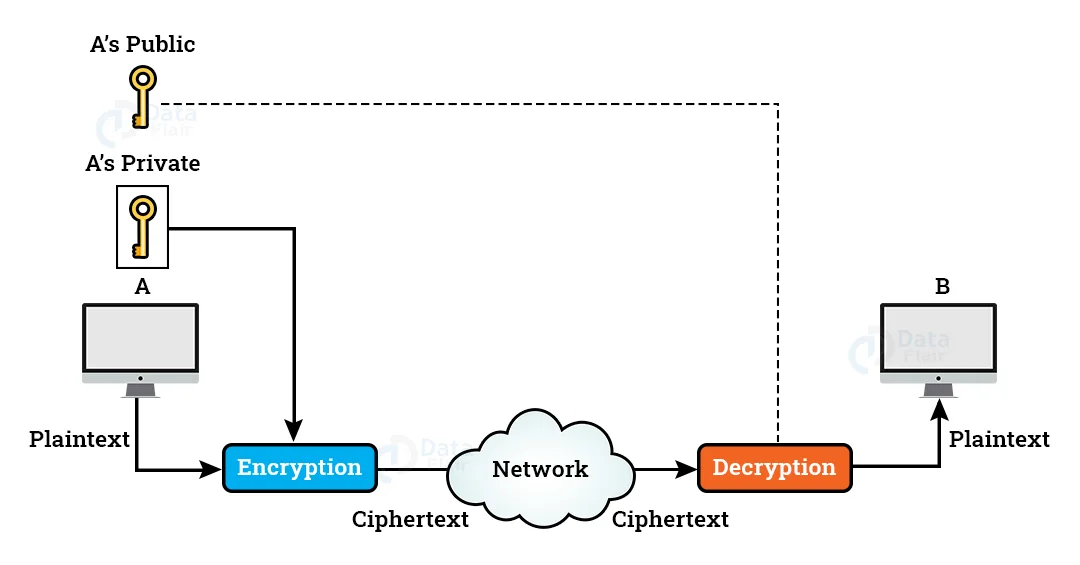
A public key encryption method is used to sign a document in Digital Signature. However, the functions of a public key and a private key are distinct in this context. The sender encrypts the communication by using a private key, and the recipient decrypts it with the sender’s public key.
The private key is used for encryption in Digital Signature, whereas the public key is utilised for decoding.
Secret key encryption cannot be used to create a digital signature.
What does signing a digest mean?
If the message is brief, public key encryption is efficient. If the communication is lengthy, using public key encryption is wasteful. The answer to this issue is to allow the sender to sign a digest of the document rather than the entire document.
The sender generates a small version (digest) of the document and signs it; the recipient verifies the miniature version’s signature.
The message digest is generated with the help of a hash function. From the variable-length message, the hash function generates a fixed-size digest.
MD5 (Message Digest 5) and SHA-1 are the two most often used hash algorithms (Secure Hash Algorithm 1). The first generates a 120-bit digest, whereas the second generates a 160-bit digest.
To be successful, a hash function must have two properties:
- First, the digest must be one-way, that is, it can only be produced from the message and not the other way around.
- Second, hashing is a one-to-one function, which means that no two messages should produce the same digest.
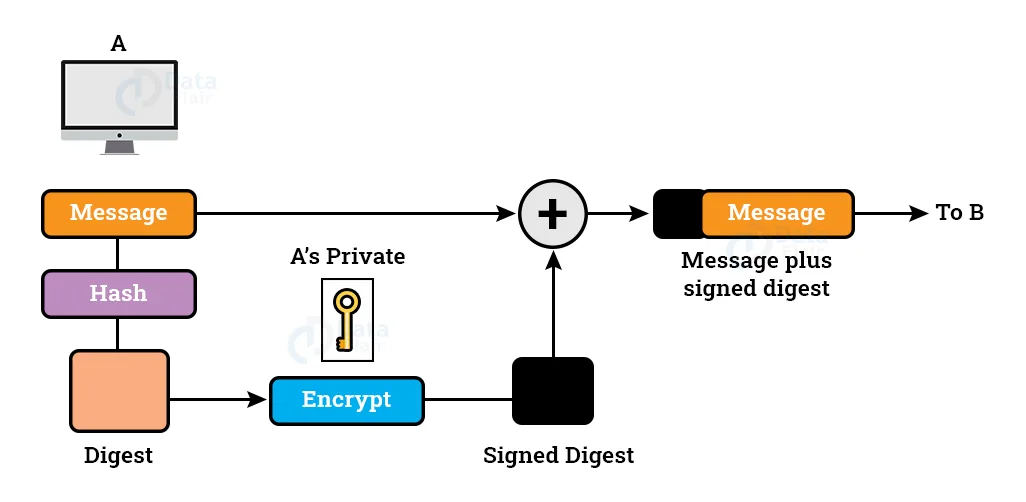
Steps Taken while Signing Digest:
A hash function is used to generate the message’s smaller version (digest).
The sender’s private key is used to encrypt the digest.
After the digest has been encrypted, it is linked to the original message and transmitted to the recipient.
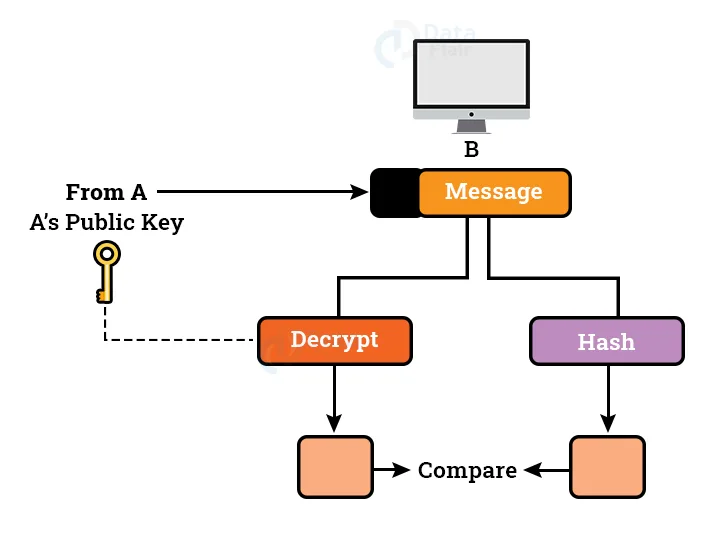
The recipient receives both the original message and the encrypted digest and decrypts them. The receiver applies the hash function to the original message to generate the second digest, and it also decrypts the received digest using the sender’s public key. If both digests are identical, then all features of security are retained.
Sender Side:
Receiver Side:
Summary:
In this article, we looked at the concept of Digital Signatures and how they are implemented in various forms, including signing whole documents and signing only digests. We also looked at various important terms associated with digital signatures.
You give me 15 seconds I promise you best tutorials
Please share your happy experience on Google