Create Virtual Network in Azure
Free AWS Course for AWS Certified Cloud Practitioner (CLF-C01) Start Now!!
FREE Online Courses: Click for Success, Learn for Free - Start Now!
In today’s article, we will learn about Azure virtual network which will help the developers to perform their tasks by keeping the security section in mind.
What is Azure Virtual Network?
The Azure Virtual Network is a logical representation of a cloud network. So, by creating an Azure Virtual Network, we can define our private IP address range on Azure as well as deploy various types of Azure resources.
For instance, an Azure virtual machine, an App service environment, an Integration service environment, and so on.
Creating Azure Virtual Network and Subnets
Below are the steps to create virtual network in Azure:
1: Firstly, the developer should search for Virtual Networks. For this, the developers can use their existing resource group or create a new one.
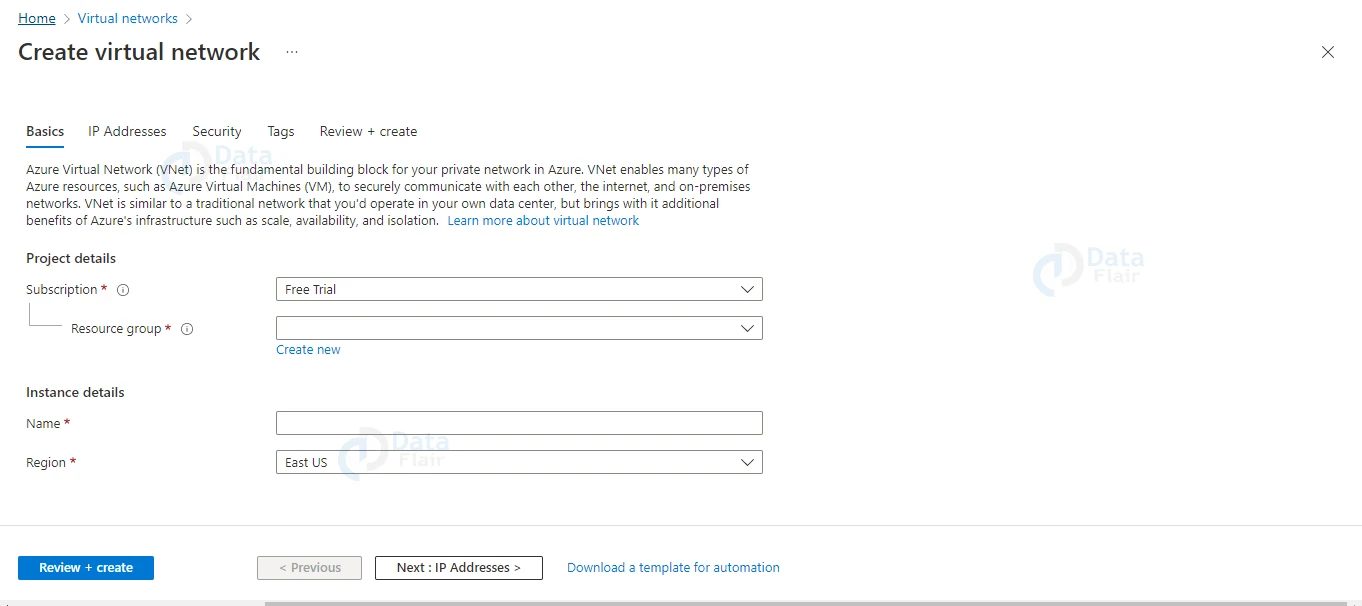
2: Once the developer opens they have to choose the resource group. If they don’t have any they can make a new one. Then provide a name and choose the region.
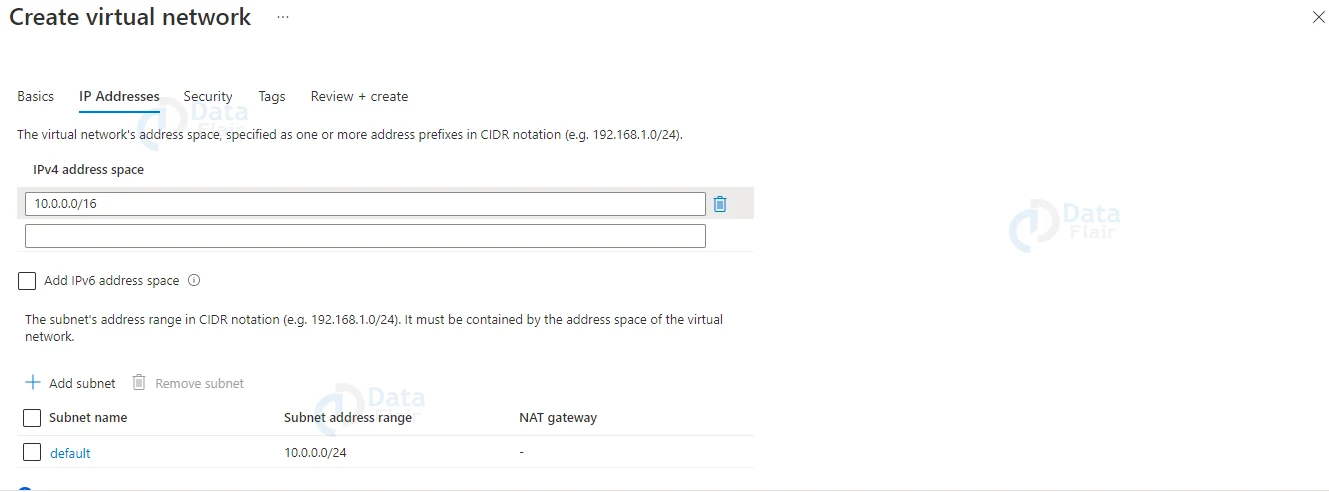
3: Now, a new window will appear where they should fill in the details such as IP address space, subnet name etc.
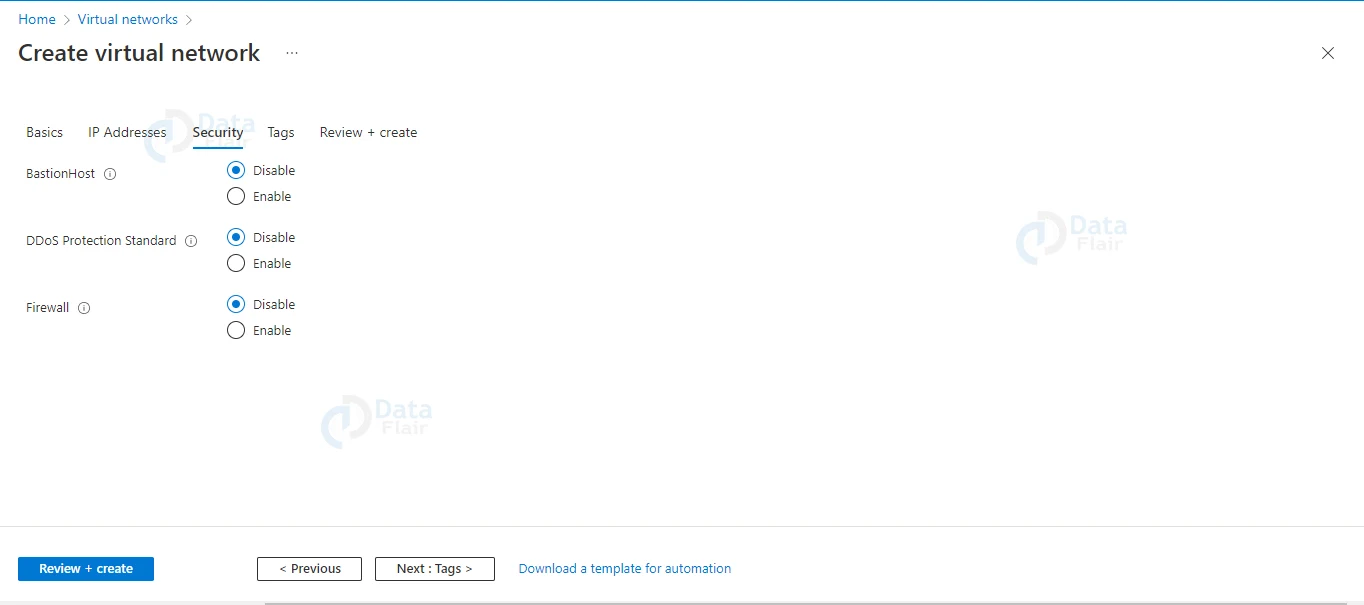
4: The developers can choose the security configurations as per their requirements.
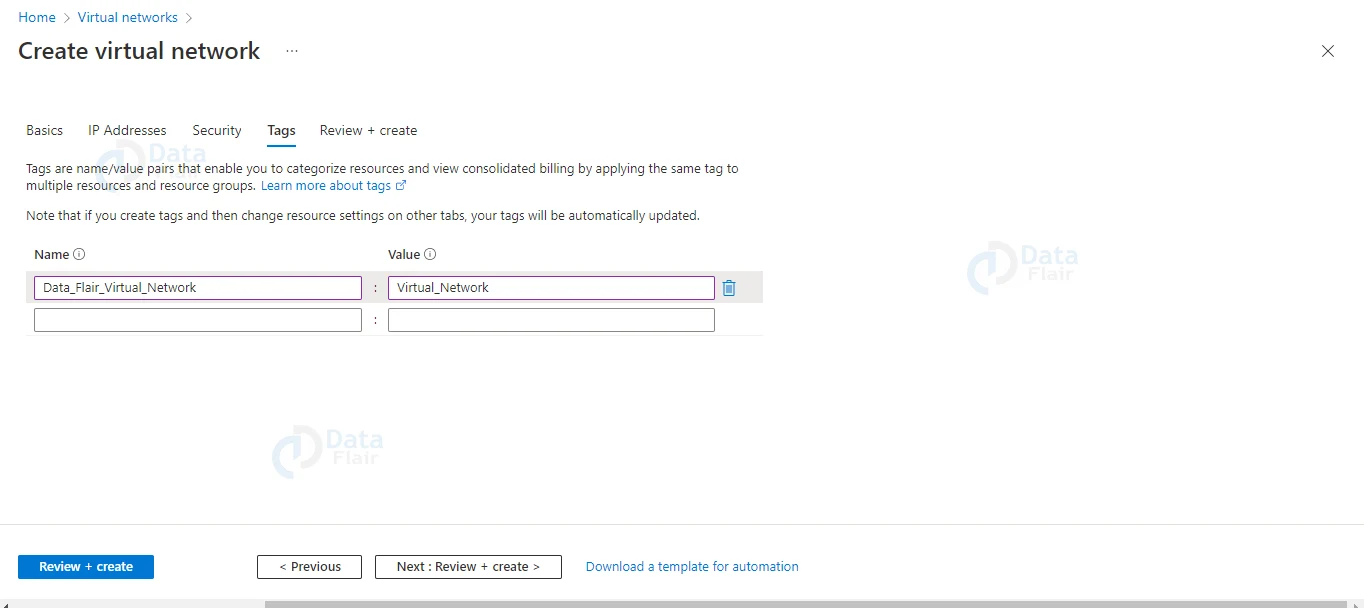
5: Mention the tags for the virtual network.
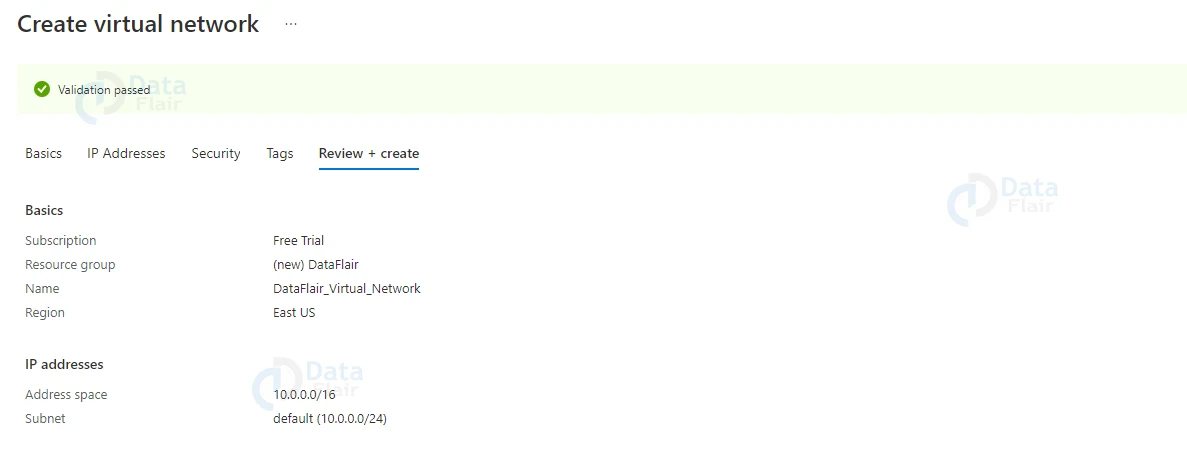
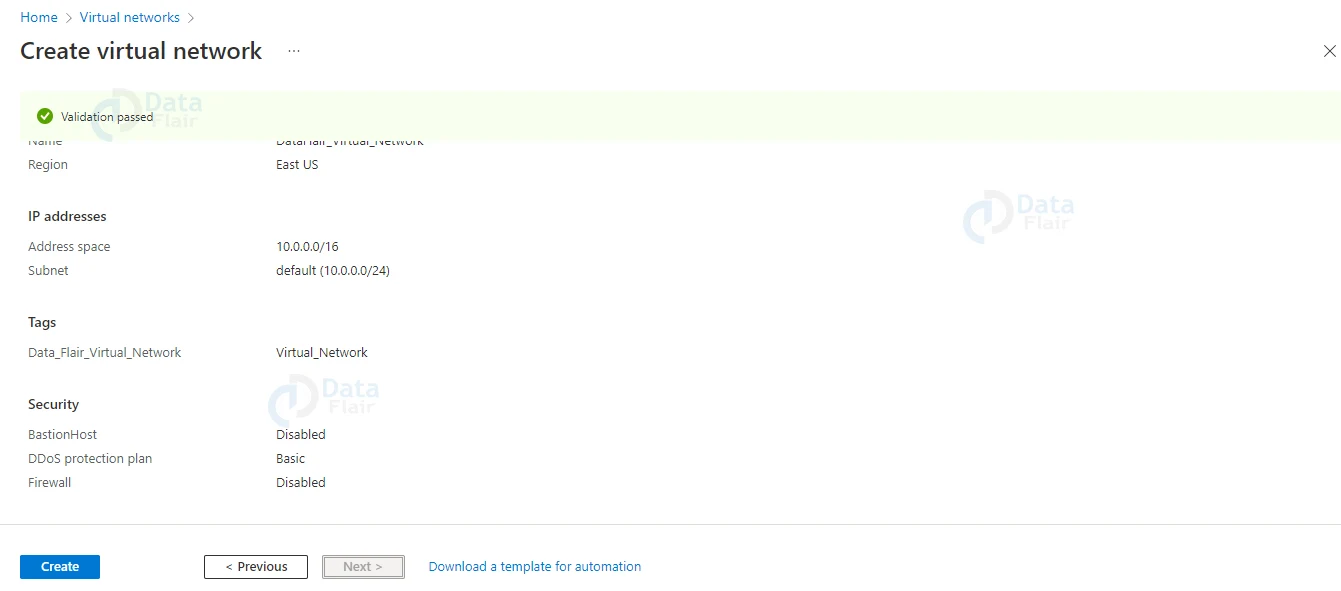
6: In the next step review all the details. Here you will see validation status as passed and then hit the create button.
7: After a few seconds the deployment will be successful.
Azure Virtual Network Capabilities
Communication Between Resources: Communication between the resources of a virtual network or with other resources via service endpoints.
Communication with On-premises Resources: By establishing a point-to-site VPN, a site-to-site VPN, or an Express route, your workloads in the Azure virtual network can seamlessly communicate with workloads in our on-premises data center.
The Azure virtual network includes a plethora of capabilities for traffic control.
1. Filter Network Traffic: To filter traffic coming to virtual network resources, we can use Network Security Groups, Application Security Groups, Azure firewalls, or third-party network virtual appliances.
2. Route Network Traffic: We can use routing tables to route network traffic, or we can configure user-defined routes to route all outbound traffic, for example, through a firewall.
3. Monitor Network Traffic: Using network security groups and a traffic analytics monitoring solution, you can perform extensive monitoring on both inbound and outbound communications.
Elements of Azure Virtual Network
1. Address Space
When creating a VNet, you must first specify a private IP address space within the RFC 1918 range.
This IP address space includes well-known IP addresses like 10.0.0.0, 192.168.0.0, and 172.16.0.0. A virtual network contains one or more of these address ranges, from which additional subnets can be created.
The address spaces of Azure Virtual Networks cannot overlap. If you attempt to create a virtual network using an existing address space, Azure will display a warning message.
If one does not intend to peer at the two virtual networks, then they can ignore this warning. Also if you intend to build a hybrid network, you should avoid using overlapping network spaces with your on-premises data center.
2. Subnet
A subnet is important because many configurations will be done at the subnet level. It is the VNet’s IP address range.
Vnet can be divided into multiple subnets based on various design considerations, such as deploying a virtual machine, App services environment, an integration service environment, and so on.
VMs and PaaS services are deployed to subnets within the same VNet and can communicate with one another without any additional configuration. Subnets are configured with route tables, NSG, service endpoints, and policies.
3. Network Security Groups
Network Security Groups (NSG) protect each subnet within a virtual network. NSGs are used to filter traffic entering and exiting a virtual network.
To identify the traffic, you define the source and destination, port, and protocol for each rule. An NSG contains default security rules that automatically secure resources by blocking Internet traffic while allowing traffic from other virtual networks to pass through.
4. Routing and Peering
Azure develops the routes within subnets, virtual networks, on-premises networks, and the Internet automatically.
One can make use of the route tables for controlling where Azure routes traffic for each subnet.
Users can also make use of their existing on-premises BGP routes for connecting their Azure virtual networks.
And, when they connect their on-premises data center to the Azure cloud they require an Azure VPN Gateway or ExpressRoute connection.
While Azure automatically connects subnets within the same virtual network, routing between virtual networks necessitates network peering.
Virtual network peering connects multiple VNets so that they appear as one for connectivity purposes. The traffic between the virtual networks is routed through the Microsoft backbone infrastructure rather than the Internet.
Virtual Network Pricing
Unlike virtual machines and other Azure resources, virtual networks are free to create. Creating a virtual network incurs no resource costs, and you can create up to 50 virtual networks per subscription.
However, if you establish a peering connection between two virtual networks, Azure will charge you for both inbound and outbound data transfers.
Securing Resources in Azure Virtual Network
Azure also offers several capabilities for safeguarding your network resources. One example is Azure Firewall, a cloud-based network security service.
By enforcing application and network connectivity policies, Azure Firewall safeguards resources. Azure Firewall includes built-in high availability and limitless cloud scalability.
The Azure Web Application Firewall (WAF), in addition to the Azure Firewall, is designed specifically to protect web applications. WAF protects against common web application exploits and vulnerabilities, including those on the OWASP Top Ten list.
Azure also includes free basic distributed denial-of-service (DDoS) attack protection. The basic service monitors traffic and automatically mitigates attacks.
One can also upgrade to standard protection, which includes rapid response assistance, mitigation policies, metrics, and alerts.
Conclusion
Finally, we are into the last section of our article. In this article, we learnt about virtual networks and how to create them. Now, once the developer has learnt about it they should start learning about the security.
Did you know we work 24x7 to provide you best tutorials
Please encourage us - write a review on Google