Computer Network Models – Layered Architecture
FREE Online Courses: Your Passport to Excellence - Start Now
A systematic strategy is necessary for data transmission to occur for two or more users to send data from one to the other. This method allows people to converse and send data in an efficient and orderly manner. It is implemented in computer networks using models, which are referred to as computer network models.
Computer network models are in charge of creating a link between the sender and receiver as well as delivering data in a seamless manner.
Importance of Computer Network Layered Architecture:
- The layered architecture’s major goal is to split the design into tiny parts.
- Each lower layer contributes its services to the top layer, resulting in a complete collection of services for managing communications and running applications.
- It provides modularity and explicit interfaces, allowing subsystems to interact with one another.
- It ensures layer independence by offering services from the lowest to the highest layer without specifying how the services are implemented. As a result, any changes made to one layer have no effect on the other levels.
- The number of levels, functions, and contents of each layer will differ from one network to the next. However, the objective of each layer is to offer the service from a lower to a higher layer while masking the specifics of how the services are performed from the layers.
Fundamental Components of Layered Architecture:
Services, protocols, and interfaces are the fundamental components of layered architecture.
1. Service:
A collection of activities provided by a layer to a higher layer.
2. Protocol:
It is a collection of rules that a layer employs to share data with a peer entity.
These rules primarily address the contents and order of the messages used.
3. Interface:
The interface is the means through which a message is transmitted from one layer to another.
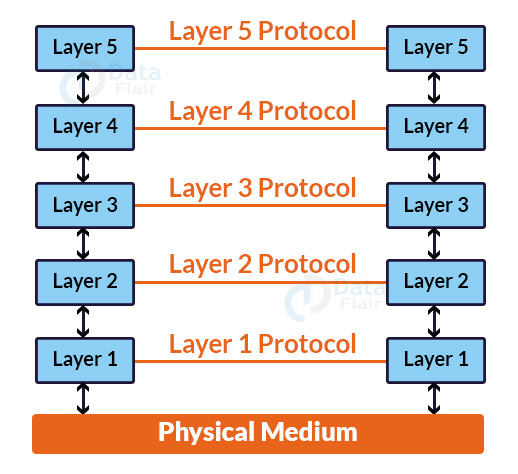
In a layer n architecture, layer n on one computer communicates with layer n on another machine, and the rules employed in the interaction are referred to as a layer-n protocol.
Features of Layered Architecture:
- In the case of layered architecture, no data is transmitted from one machine’s layer n to another machine’s layer n. Instead, until the lowest layer is reached, each layer transmits the data to the one directly below it.
- The physical channel via which real communication takes place is located underneath layer 1.
- Unmanageable activities are split into smaller, more manageable jobs in a layered architecture.
- Data is sent from the upper layer to the bottom layer via an interface. A layered design provides a clear interface so that only the most important information is communicated across levels. It also assures that one layer’s implementation may be readily changed by another.
Types of Computer Network Models:
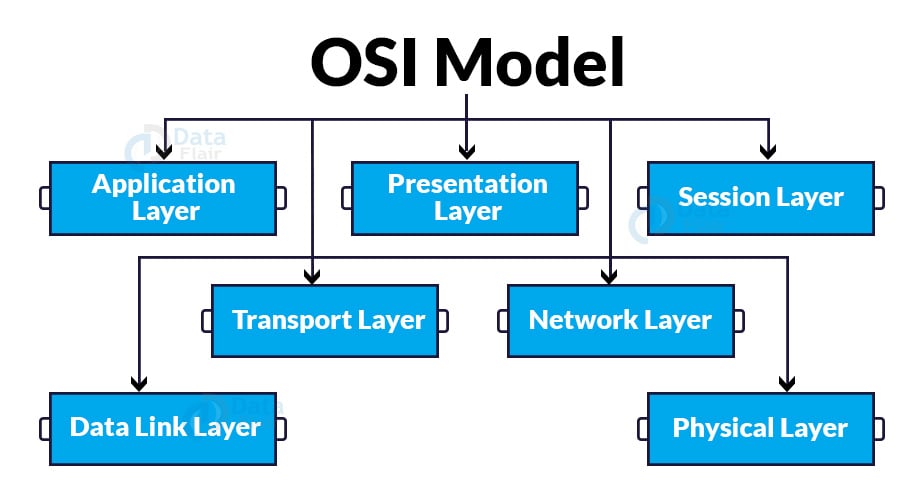
1. OSI Model:
Technology is evolving rapidly!
Stay updated with DataFlair on WhatsApp!!
The OSI Model has seven layers, namely:
- Application Layer:
- The application layer is in charge of providing an interface to the application user. This layer contains protocols that communicate directly with the user.
- Presentation Layer:
- This layer deals with the appearance and format of the data on the end devices.
- Session Layer:
- This layer is responsible for maintaining connections between remote hosts.
- For example, after user/password authentication is complete, the remote host retains the session and does not request authentication again within that time period.
- Transport Layer:
- The Transport Layer is in charge of end-to-end delivery between hosts.
- Network Layer:
- This layer is in charge of assigning addresses and uniquely addressing hosts in a network.
- Data Link Layer:
- The Data Link Layer is in charge of reading and writing data from and onto the line. At this layer, link problems are identified.
- Physical Layer:
- This layer tells us about the hardware, cabling wiring, power output, pulse rate, and so on.
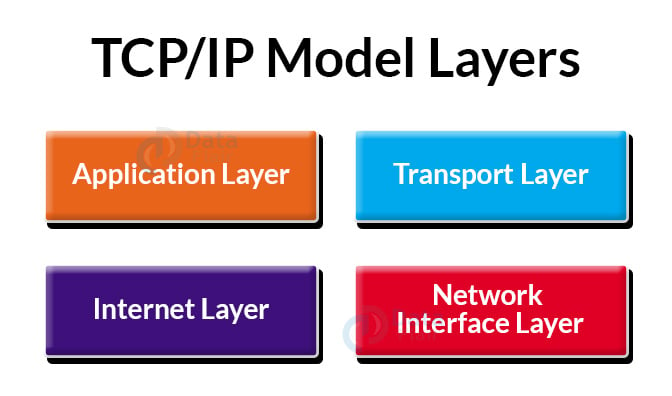
2. TCP/IP Model:
The TCP/IP Model has four layers, namely:
- Application Layer:
- The application layer specifies the protocol that allows users to communicate with the network. FTP, HTTP are some such protocols.
- Transport Layer:
- The Transport Layer describes how data should move between hosts.
- The Transmission Control Protocol is the most important protocol at this layer (TCP).
- This layer guarantees that data transferred between hosts is in the correct sequence and is in charge of end-to-end delivery.
- Internet Layer:
- The Internet Protocol (IP) operates on this layer.
- This layer makes host addressing and identification easier.
- This layer is responsible for routing.
- Network Interface Layer:
- This layer offers the means for delivering and receiving real data.
- This layer, unlike its OSI Model equivalent, is independent of the underlying network architecture and hardware.
What is the need for Layered Architecture?
- Divide-and-conquer method:
- The divide-and-conquer technique divides unmanageable tasks into tiny and manageable jobs during the design phase.
- In a nutshell, this technique minimises the complexity of the design.
- Modularity:
- Layered architecture has a higher level of modularity.
- Layer independence is provided through modularity, making it easier to comprehend and apply.
- Simple to modify:
- It provides layer independence, allowing changes to one layer’s implementation to have no effect on other levels.
- Simple to test:
- Each layer of the layered architecture may be separately studied and tested.
Summary:
In this article, we take a look at the importance and features of layered architectures, as well as a brief look at two of the most popular Computer Network Models in existence. We also discuss the need for layered architecture, and the different features that come with layered architecture.
Did you like this article? If Yes, please give DataFlair 5 Stars on Google