Azure Security and its Features
Free AWS Course for AWS Certified Cloud Practitioner (CLF-C01) Start Now!!
FREE Online Courses: Your Passport to Excellence - Start Now
In Cloud Technology, security and governance ate the two main foundational layers. Microsoft Azure offers the most powerful services that support developers in deploying, integrating, operating, governing and securing cloud space for fulfilling the requirements of every user and organization. Whether the user is using PaaS or IaaS, Azure Security services play a very crucial role.
Microsoft’s Azure Security Center
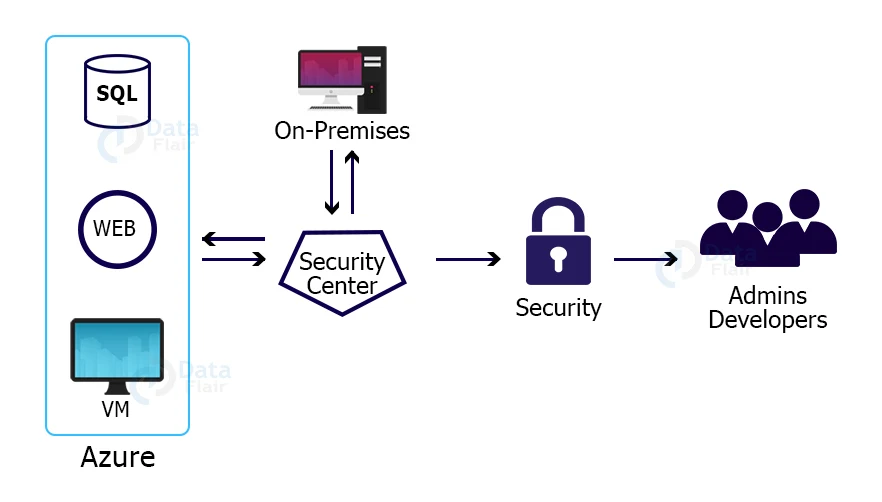
Microsoft’s Azure Security Center is a centralized and unified security management service available for the user’s and organization’s cloud environment. The security center be responsible and will continuously scan the user’s resources.
The security center will provide suggestions to the administrators of the organizations and the developers to immediately respond and secure their environment.
The functionality of the Security Center is not limited to this it expands to the hybrid environment with the help of installation of agents on the user’s virtual machines located on-premises otherwise at the resources located in other clouds.
Azure’s Security Center is locally connected with all the Azure services, and it will integrate with the Azure Advisor, which provides a unified best experience for the administrators and developers to secure their Azure environment completely.
Azure Platform
As we know Microsoft Azure is a public cloud platform that supports a wide range of operating systems, programming languages, frameworks, tools, databases and devices.
It has the capability to run in Linux containers with the help of Docker Integration to build applications by using JavaScript, Python, .NET, PHP, Java, and Node.js; build back-ends for iOS, Android, and Windows devices.
Azure Public Cloud services support similar technologies that millions of IT professionals trust.
When the user can build or migrate their IT assets on a public cloud provider then they are depending upon the provider to safeguard their organization’s applications.
Microsoft Azure’s infrastructure is specially designed from the facility to applications for hosting millions of customers and it offers a trustworthy foundation on which the organizations can meet the security requirements.
Along with that Azure offers their users with various configurable security options and the ability to control them so that the users can customize the security to meet their unique requirements depending upon the organization’s deployments.
Azure Security Capabilities
Depending upon the cloud service mod there is variable responsibility for who is responsible for managing the security-related tasks of the application or service.
In the Azure platform, there are multiple capabilities available for the users to assist them in meeting their requirements with the help of built-in features and by partner solutions that can be deployed in the Azure subscription.
The built-in capabilities are managed and organized into six functional sections. They are as follows:
- Operations
- Applications
- Storage
- Networking
- Compute
- Identity
Azure Security Operations
In the following section of the article, we will discuss some of the additional information regarding the crucial features in the Azure security operations along with a summary of these capabilities.
1. Microsoft Sentinel
Security information and event management (SIEM) and security orchestration, automation, and response (SOAR) solution Microsoft Sentinel is a scalable, cloud-native SIEM and SOAR solution.
Microsoft Sentinel is a single solution for attack detection, threat visibility, proactive hunting, and threat response that delivers intelligent security analytics and threat information throughout the company.
2. Microsoft Defender for Cloud
With enhanced visibility and control over the security of your Azure resources, Microsoft Defender for Cloud lets you prevent, detect, and respond to threats. It will take the responsibility to integrate the security monitoring and will take care of policy administration across your Azure subscriptions, assist in the detection of threats that might otherwise go unreported, and integrate with a wide range of security solutions.
Defender for Cloud also assists with security operations by providing a single dashboard that displays alarms and recommendations that can be acted on right away.
Through many cases, you may resolve difficulties in the Defender for Cloud console with a single click.
3. Azure Resource Manager
You can use Azure Resource Manager to work with your solution’s resources as a group. All of the resources for your solution can be deployed, updated, or deleted in a single, coordinated action.
For deployment, you use an Azure Resource Manager template that can be used in a variety of contexts, including testing, staging, and production.
Security, auditing, and tagging capabilities in Resource Manager let you manage your resources after deployment.
Because standard security control settings may be integrated into standardized template-based deployments, Azure Resource Manager template-based deployments help to improve the security of solutions deployed in Azure.
This decreases the possibility of security configuration problems during manual deployments.
4. Application Insights
Application Insights is a web developer-friendly Application Performance Management (APM) tool. You may use Application Insights to monitor your live web applications and find performance abnormalities automatically.
It comes with advanced analytics capabilities to help you detect problems and analyze how users interact with your apps. It keeps an eye on your app while it’s operating, both during testing and after it’s been published or deployed.
Application Insights generates graphs and tables that show you things like when your app gets the most traffic, how responsive it is, and how well it is served by any external services it relies on. You can search through the telemetry data in detail to diagnose the source of crashes, malfunctions, or performance difficulties.
In addition, the service notifies you through email whenever your app’s availability or performance changes.
As a result, Application Insight becomes a vital security tool since it aids availability in the security triangle of confidentiality, integrity, and availability.
5. Azure Monitor
You may look over the telemetry data in great detail to figure out what’s causing crashes, malfunctions, or performance issues. Additionally, the service sends you an email whenever the availability or functionality of your app changes.
As a result, Application Insight becomes an important security tool because it helps with availability in the security triangle of confidentiality, integrity, and availability.
6. Azure Monitor logs
Azure Monitor logs – In addition to Azure resources, Azure Monitor provides an IT management solution for on-premises and third-party cloud-based infrastructure (such as AWS). Data from Azure Monitor may be seamlessly forwarded to Azure Monitor logs, allowing you to access metrics and logs for your whole environment in one location.
Azure Monitor logs can be valuable in forensic and other security investigations since they allow you to look through vast quantities of security-related items fast and easily using a flexible query strategy.
Additionally, logs from on-premises firewalls and proxy servers can be uploaded to Azure and analyzed using Azure Monitor logs.
7. Azure Advisor
Azure Advisor is a one-on-one cloud specialist who assists you in optimizing Azure deployments. It examines your resource settings as well as use data. It then suggests options to help you increase the performance, security, and dependability of your resources while also looking for ways to cut your Azure spending overall.
Azure Advisor makes security advice that might help you improve the overall security posture of your Azure products. These recommendations are based on Microsoft Defender for Cloud’s security analysis.
Applications of Azure Security
In the following section of the article, we will discuss some extra topics regarding the essential features in the application security section. Also, we have mentioned the summary of these capabilities.
1. Web Application Vulnerability Scanning
Using the connection with Tinfoil Security to perform one-click vulnerability scanning on your App Service app is one of the simplest methods to get started with testing for vulnerabilities on your App Service app. You can read the test results in an easy-to-understand report and follow the step-by-step instructions to remedy each vulnerability.
2. Penetration Testing
Azure does not perform application’s penetration testing for you, but we understand that you want and need to do it yourself. That’s a good thing because improving the security of your applications improves the security of the entire Azure ecosystem.
Customers must follow the Microsoft Cloud Penetration Testing Rules of Engagement, even though notifying Microsoft of pen testing operations is no longer necessary.
3. Web Application Firewall
The web application firewall (WAF) in Azure Application Gateway protects web applications against attacks such as SQL injection, cross-site scripting, and session hijacking. It is preconfigured with protection against the top 10 frequent vulnerabilities determined by the Open Web Application Security Project (OWASP).
4. Authentication and authorization in Azure App Service
App Service Authentication / Authorization is a feature that allows your app to sign in users without requiring changes to the app’s backend code. It gives you a simple approach to secure your app and interact with per-user data.
5. Layered Security Architecture
Developers can construct a layered security architecture with different levels of network access for each application tier using App Service Environments, which provide an isolated runtime environment deployed into an Azure Virtual Network. A typical objective is to keep API backends hidden from general Internet access and only allow upstream web apps to call APIs.
Network Security Groups (NSGs) can be used to restrict public access to API apps on Azure Virtual Network subnets hosting App Service Environments.
6. Web server Diagnostics and Application Diagnostics
Service for Apps Diagnostic capabilities for logging information from both the web server and the web application is provided by web apps. Web server diagnostics and application diagnostics are conceptually separated.
Two key advancements in diagnosing and debugging sites and applications are included in the Web server.
Real-time state information about application pools, worker processes, sites, application domains, and current requests is the first new feature.
The detailed trace events that track a request throughout the whole request-and-response process are the second new benefit.
IIS 7 can be configured to automatically capture entire trace logs in XML format for any given request depending on elapsed time or incorrect response codes to enable the gathering of these trace events.
Storage Features in Azure Application Security
In the following section of the article, we will discuss some extra topics regarding the storage features in the application security section. Also, we have mentioned the summary of these capabilities.
1. Azure role-based access control (Azure RBAC)
Azure role-based access control can help you protect your storage account (Azure RBAC). Organizations that want to enforce security policies for data access must restrict access based on the need to know and least privilege security principles.
The proper Azure role is assigned to groups and applications at a specific scope to grant these access permissions.
You can provide privileges to users using Azure built-in roles like Storage Account Contributor.
Azure RBAC can be used to control access to storage keys for a storage account using the Azure Resource Manager paradigm.
2. Shared Access Signature
A shared access signature (SAS) grants delegated access to your storage account’s resources. You can provide a client with limited permissions to objects in your storage account for a defined amount of time and with a set of permissions using the SAS. You don’t have to disclose your account access keys to grant these limited capabilities.
3. Encryption in Transit
Encryption in transit is a method of safeguarding data as it travels across networks. You can secure data with Azure Storage by using the following methods:
- When transferring data into or out of Azure Storage, use transport-level encryption, such as HTTPS.
- SMB 3.0 encryption for Azure File sharing is an example of wire encryption.
- Client-side encryption encrypts data before it is put into storage and decrypts it after it has been transferred out.
4. Encryption at rest
Data encryption at rest is a need for many enterprises in terms of data privacy, compliance, and data sovereignty. There are three security capabilities in Azure storage that encrypt data while it is “at rest”:
- You can use Storage Service Encryption to have the storage service automatically encrypt data when it’s written to Azure Storage.
- Client-side Encryption also has the ability to encrypt data at rest.
- You can encrypt the OS and data disks used by an IaaS virtual machine with Azure Disk Encryption.
5. Storage Analytics
For a storage account, Azure Storage Analytics does logging and gives metrics data. This information can be used to track down requests, analyze usage patterns, and detect problems with your storage account.
Storage Analytics keeps track of successful and unsuccessful queries to a storage service. This information can be used to track individual requests and troubleshoot storage service problems. On a best-effort basis, requests are logged. Authenticated requests of the following sorts are logged:
- Requests that were successful.
- Timeout, throttling, network, authorization, and other problems are examples of failed requests.
- Requests with a Shared Access Signature (SAS), both successful and unsuccessful.
- Requests for data from analytics.
6. Enabling Browser-Based Clients Using CORS
CORS (Cross-Origin Resource Sharing) is a system that allows domains to grant permission to each other to access each other’s resources.
Extra headers are sent by the User-Agent to ensure that JavaScript code loaded from one domain can access resources from another domain.
The latter domain then responds with additional headers granting or prohibiting access to its resources to the original domain.
Azure storage services now support CORS, which means that after you specify the CORS rules for the service, a fully authenticated request from a different domain is assessed to see if it is authorized according to the criteria you set.
Networking Features in Azure Application
In the following section of the article, we will discuss some extra topics regarding the networking features in Azure application security section. Also, we have mentioned the summary of these capabilities.
1. Network Layer Controls
Network access control is the act of restricting connectivity to and from specific devices or subnets, and it is at the heart of network security. The goal of network access control is to limit access to your virtual machines and services to only the people and devices you specify.
2. Network Security Groups
A Network Security Group (NSG) is a stateful packet filtering firewall that allows you to regulate access using a five-tuple.
Application layer inspection and authenticated access controls are not provided by NSGs.
They can be used to manage traffic across Azure Virtual Network subnets as well as the traffic between Azure Virtual Networks and the Internet.
3. Azure Firewall
Azure Firewall is a cloud-native, intelligent network firewall security service that protects your Azure cloud workloads from threats. It’s a stateful firewall as a service with high availability and unconstrained cloud scalability built-in. It can inspect both east-west and north-south traffic.
Standard and Premium versions of Azure Firewall are available. Microsoft Cyber Security provides L3-L7 filtering and threat intelligence feeds directly through Azure Firewall Standard.
Advanced features of Azure Firewall Premium include signature-based IDPS, which allows for rapid detection of threats by scanning for specific patterns.
4. Route Control and Forced Tunneling
Controlling routing behavior on your Azure Virtual Networks is an important network security and access control feature.
For example, you’ll need to be able to regulate and configure routing behavior if you want to ensure that all traffic to and from your Azure Virtual Network passes via your virtual security appliance. In Azure, you may achieve this by configuring User-Defined Routes.
User-Defined Routes allow you to configure the inbound and outbound paths for traffic traveling into and out of individual virtual machines or subnets to ensure the most secure path feasible.
Forced tunneling is a method of ensuring that your services are not allowed to connect to other devices over the Internet.
This is distinct from the ability to accept and reply to incoming connections. Front-end web servers must reply to requests from Internet hosts, so incoming traffic from the Internet is allowed, and the web servers can answer.
Forcing outbound traffic to the Internet to transit via on-premises security proxies and firewalls is known as forced tunneling.
5. Virtual Network Security Appliances
While Network Security Groups, User-Defined Routes, and forced tunneling give security at the network and transport layers of the OSI model, there may be occasions when you want to enable security at the stack’s higher levels.
Using an Azure partner network security appliance solution, you can gain access to these advanced network security features.
By searching for “security” and “network security” in the Azure Marketplace, you may find the most up-to-date Azure partner network security solutions.
6. Azure Virtual Network
A virtual network (VNet) in Azure is a cloud version of your network. It’s a specialised logical separation of the Azure network fabric for your subscription. Within this network, you have complete control over IP address blocks, DNS settings, security policies, and route tables. You can divide your VNet into subnets and use Azure Virtual Networks to host Azure IaaS virtual machines (VMs) and/or Cloud services (PaaS role instances).
Additionally, you can use one of Azure’s connectivity options to connect the virtual network to your on-premises network. In essence, you can expand your network to Azure while maintaining total control over IP address blocks and taking advantage of Azure’s corporate scale.
7. Azure Private Link
Azure Private Link allows you to use a private endpoint to access Azure PaaS Services (such as Azure Storage and SQL Database), as well as Azure, hosted customer-owned/partner services in your virtual network. It’s setup and consumption are uniform across Azure PaaS, customer-owned, and shared partner services.
Your virtual network traffic to the Azure service is always routed through the Microsoft Azure backbone network.
You can use Private Endpoints to limit access to your Azure service resources to only your virtual networks.
Azure Private Endpoint connects you discreetly and securely to a service powered by Azure Private Link, essentially bringing the service into your VNet, using a private IP address from your VNet.
To use Azure services, you no longer need to expose your virtual network to the public internet.
In your virtual network, you can also set up your private link service. The Azure Private Link service is a pointer to your own Azure Private Link-powered service.
Your Azure Standard Load Balancer-based service can be configured for Private Link access, allowing customers to access it privately from their virtual networks.
Customers can map a private endpoint to this service from within their virtual network. To deliver Azure services, you no longer need to expose your service to the public internet.
8. VPN Gateway
You must construct a VPN gateway for your Azure Virtual Network to transport network traffic between it and your on-premises location. A virtual network gateway (VPN gateway) is a form of virtual network gateway that sends encrypted communication across a public connection.
VPN gateways can also be used to transport traffic via the Azure network fabric between Azure Virtual Networks.
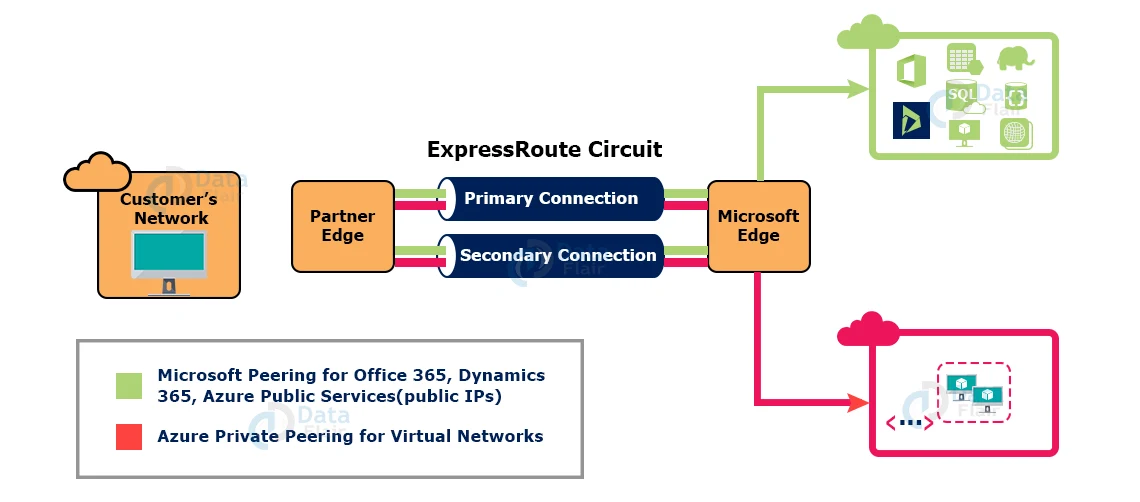
9. Express Route
Microsoft Azure ExpressRoute is a dedicated WAN link that allows you to extend your on-premises networks into the Microsoft cloud via a dedicated private connection provided by a connectivity provider. You can connect to Microsoft cloud services such as Microsoft Azure, Microsoft 365, and CRM Online using ExpressRoute.
An any-to-any (IP VPN) network, a point-to-point Ethernet network, or a virtual cross-connection through a connectivity provider at a co-location facility can all be used for connectivity.
ExpressRoute connections are more secure than VPN-based alternatives since they do not go over the public Internet. This enables ExpressRoute connections to provide greater reliability, quicker speeds, lower latency, and greater security than traditional Internet connections.
10. Application Gateway
By outsourcing CPU-intensive TLS termination to the Application Gateway (also known as “TLS offload” or “TLS bridging”), you can improve web farm productivity.
Round-robin distribution of incoming traffic, cookie-based session affinity, URL path-based routing, and the ability to host numerous websites behind a single Application Gateway are just a few of the Layer 7 routing features it offers. A layer-7 load balancer is Azure Application Gateway.
It allows failover and performance-routing HTTP requests between different servers, whether on-premises or in the cloud.
HTTP load balancing, cookie-based session affinity, TLS offload, custom health probes, multi-site support, and many more capabilities are available through this application’s Application Delivery Controller (ADC).
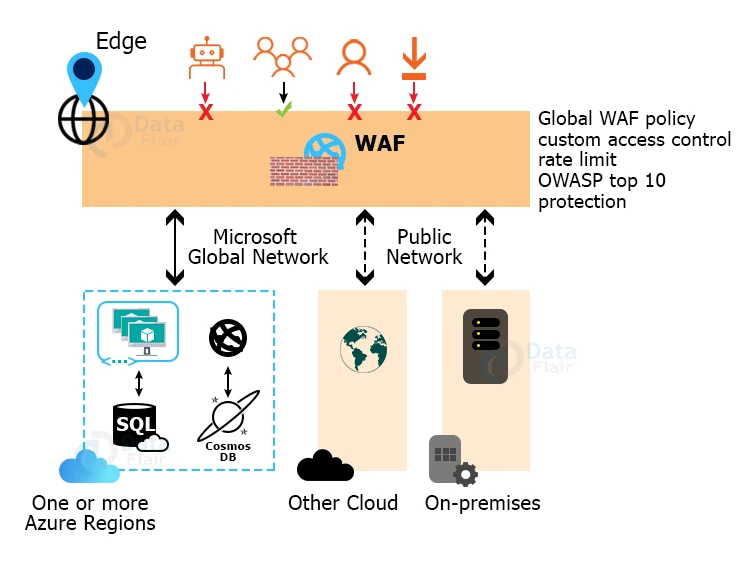
11. Web Application Firewall
The Azure Application Gateway Web Application Firewall protects web applications that use the application gateway for conventional Application Delivery Control (ADC) functionality.
The majority of the OWASP top 10 frequent web vulnerabilities are protected by a web application firewall.
A centralized web application firewall that protects against web attacks simplifies security management and ensures that the application is protected from intrusion threats.
By patching a known vulnerability at a central location rather than safeguarding each web application, a WAF solution can respond to a security threat faster. Existing application gateways can easily be changed to web application firewall application gateways.
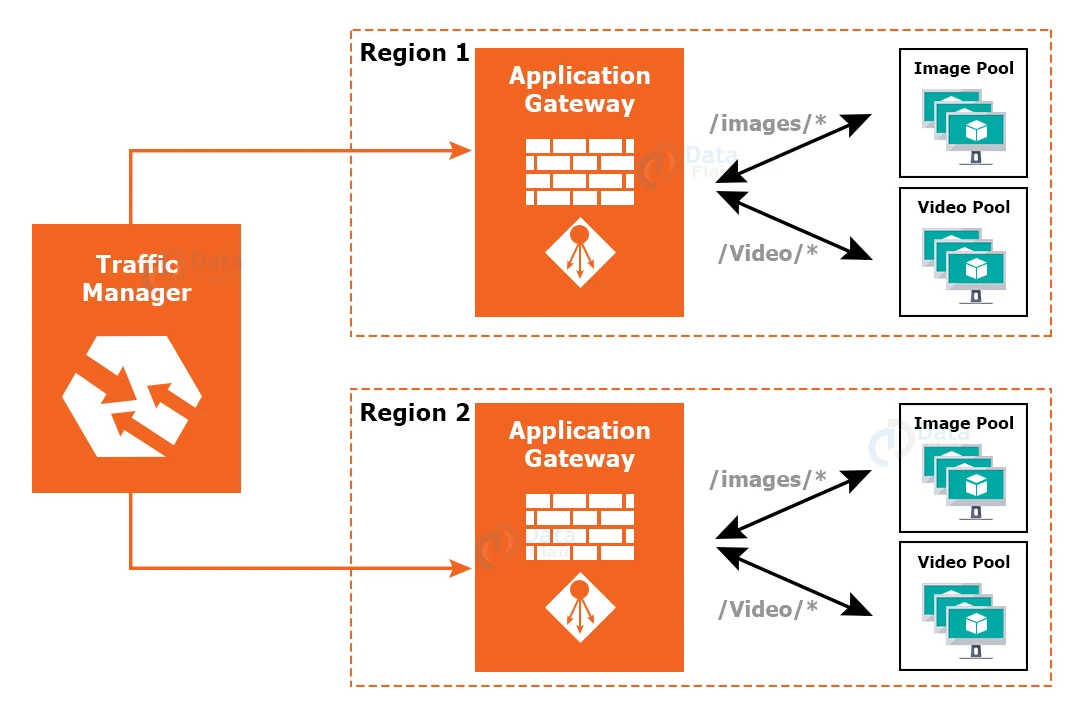
12. Traffic Manager
Microsoft Azure Traffic Manager helps you to manage user traffic distribution for service endpoints across many data centers.
Traffic Manager supports Azure VMs, Web Apps, and Cloud services as service endpoints. Traffic Manager can also be used with non-Azure endpoints.
Based on a traffic-routing strategy and the health of the endpoints, Traffic Manager uses the Domain Name System (DNS) to direct client requests to the most appropriate endpoint.
Traffic Manager includes a variety of traffic-routing algorithms, endpoint health monitoring, and automatic failover to meet the needs of various applications.
Traffic Managers can withstand failures of any magnitude, including the failure of a whole Azure region.
13. Azure Load Balancer
Your applications benefit from Azure Load Balancer’s high availability and network performance. It’s a Layer 4 (TCP, UDP) load balancer that distributes incoming traffic among healthy instances of load-balanced services. The Azure Load Balancer can be set up to:
Distribute incoming Internet traffic to virtual machines in a load-balanced manner. Public load balancing is the term for this scenario.
Balance traffic between virtual machines in a virtual network, cloud services, or on-premises PCs and virtual machines in a cross-premises virtual network. Internal load balancing is the term for this system.
External traffic is forwarded to a certain virtual machine.
14. Internal DNS
The list of DNS servers used in a VNet can be managed either in the Management Portal or in the network configuration file. For each VNet, the customer can add up to 12 DNS servers.
It’s critical to double-check that you’ve listed the customer’s DNS servers in the correct order for the customer’s environment when supplying DNS servers.
Round-robin DNS server lists do not work. They’re used in the order in which they’re listed. If the client can reach the first DNS server on the list, regardless of whether the DNS server is operational or not, the client uses that DNS server.
To change the DNS server order for the customer’s virtual network, remove the DNS servers from the list and re-add them in the desired order. The availability aspect of the “CIA” security triad is supported by DNS.
15. Azure DNS
If the client can reach the first DNS server on the list, regardless of whether that DNS server is operational or not, that DNS server is used.
Remove the DNS servers from the list and re-add them in the desired order to change the DNS server order for the customer’s virtual network. DNS supports the availability aspect of the “CIA” security triad.
16. Azure Monitor logs NSGs
For NSGs, you can enable the following diagnostic log categories:
Event: Contains entries for which NSG rules based on MAC address are applied to VMs and instance roles. Every 60 seconds, the status of these rules is collected.
Rules counter: Counts the number of times each NSG rule is used to deny or allow traffic.
17. Microsoft Defender for Cloud
Microsoft Defender for Cloud continuously assesses the security of your Azure resources to identify network security best practices.
When Defender for Cloud detects potential security flaws, it generates recommendations that walk you through the process of configuring the necessary controls to harden and protect your resources.
Compute Features of Azure Application Security
In the following section of the article, we will discuss some extra topics regarding the Compute features in the application security section. Also, we have mentioned the summary of these capabilities.
1. Anti Malware & Antivirus
To protect your virtual machines from malicious files, adware, and other threats, you can use antimalware software from security vendors such as Microsoft, Symantec, Trend Micro, McAfee, and Kaspersky with Azure IaaS.
Microsoft Antimalware for Azure Cloud Services and Virtual Machines is a security feature that assists in the detection and removal of viruses, spyware, and other malicious software.
When known malicious or unwanted software attempts to install or run on your Azure systems, Microsoft
Antimalware provides configurable alerts.
Microsoft Defender for Cloud can also be used to deploy Microsoft Antimalware.
2. Hardware Security Module
Encryption and authentication are ineffective unless the keys themselves are safeguarded. By storing your critical secrets and keys in Azure Key Vault, you can simplify their management and security.
Key Vault gives you the option of storing your keys in hardware security modules (HSMs) that are FIPS 140-2 Level 2 certified.
Your SQL Server encryption keys for backup or transparent data encryption, as well as any keys or secrets from your applications, can all be stored in Key Vault. Azure Active Directory manages permissions and access to these protected items.
3. Virtual Machine Backup
Azure Backup is a solution that protects your application data with no upfront costs and low operating expenses. Human errors can introduce bugs into your applications, which can lead to security issues, and application errors can corrupt your data. Azure Backup safeguards your virtual machines running Windows and Linux.
4. Azure Site Recovery
Figuring out how to keep corporate workloads and apps up and running during planned and unplanned outages is an important part of your organization’s business continuity/disaster recovery (BCDR) strategy.
Azure Site Recovery orchestrates workload and app replication, failover, and recovery so that they are available from a secondary location if your primary location fails.
5. SQL VM TDE
SQL Server encryption features include transparent data encryption (TDE) and column level encryption (CLE).
Customers must manage and store the cryptographic keys used for encryption in this type of encryption.
The Azure Key Vault (AKV) service is intended to improve the security and management of these keys by storing them in a safe and highly accessible location.
The SQL Server Connector allows SQL Server to use Azure Key Vault keys.
There are steps you can take if you are running SQL Server on-premises to access Azure Key Vault from your on-premises SQL Server instance.
However, you can save time by using the Azure Key Vault Integration feature for SQL Server in Azure VMs.
You can automate the configuration required for a SQL VM to access your key vault by using a few Azure PowerShell cmdlets to enable this feature.
6. VM Disk Encryption
Azure Disk Encryption is a new feature that allows you to encrypt the discs of your Windows and Linux IaaS virtual machines. It uses Windows’ industry-standard BitLocker feature and Linux’s DM-Crypt feature to provide volume encryption for the operating system and data discs.
The solution is integrated with Azure Key Vault to help you control and manage your Key Vault subscription’s disk-encryption keys and secrets.
In addition, the solution ensures that all data on virtual machine disks are encrypted at rest in your Azure storage.
7. Virtual Networking
Network connectivity is required for virtual machines. Azure requires virtual machines to be connected to an Azure Virtual Network in order to meet this requirement.
A virtual network in Azure is a logical construct built on top of the physical network fabric in Azure. Each logical Azure Virtual Network is isolated from the others.
This isolation ensures that network traffic in your deployments is not available to other Microsoft Azure customers.
8. Patch Updates
Patch updates serve as the foundation for identifying and correcting potential problems, as well as simplifying the software update management process by reducing the number of software updates that must be deployed in your enterprise and increasing your ability to monitor compliance.
9. Security policy management and reporting
Defender for Cloud assists you in preventing, detecting, and responding to threats, as well as providing you with increased visibility and control over the security of your Azure resources.
It offers integrated security monitoring and policy management across your Azure subscriptions, aids in the detection of threats that would otherwise go undetected, and collaborates with a diverse ecosystem of security solutions.
10. Security Policy Management and Reporting
Identity-based access controls are the first step in securing systems, applications, and data. Microsoft business products and services include identity and access management features that help protect your organization’s and personal information from unauthorized access while making it available to legitimate users whenever and wherever they need it.
Identity and Access Management
In the following section of the article, we will discuss some extra topics regarding the Security and Access Management features. Also, we have mentioned the summary of these capabilities.
1. Secure Identity
To manage identity and access, Microsoft employs a variety of security practices and technologies across its products and services.
- Multi-Factor Authentication necessitates the use of multiple methods of access, both on-premises and in the cloud. It offers strong authentication with a variety of simple verification options, as well as a simple sign-in process for users.
- Microsoft Authenticator offers a simple Multi-Factor Authentication experience that works with both Microsoft Azure Active Directory and Microsoft accounts, as well as support for wearables and fingerprint-based authentication.
- Password policy enforcement improves the security of traditional passwords by requiring length and complexity, forcing periodic rotation, and account lockout after failed authentication attempts.
- Token-based authentication allows for Azure Active Directory authentication.
- Azure role-based access control (Azure RBAC) allows you to grant access based on the user’s assigned role, making it simple to grant users only the access they require to perform their job duties. Azure RBAC can be tailored to your organization’s business model and risk tolerance.
- Integrated identity management (hybrid identity) allows you to keep control of your users’ access across internal data centers and cloud platforms by creating a single user identity for authentication and authorization to all resources.
2. Secure Apps and Data
Azure Active Directory, a comprehensive identity and access management cloud solution, secures data access in on-premises and cloud applications and simplifies user and group management. It combines core directory services, advanced identity governance, security, and application access management, making it simple for developers to incorporate policy-based identity management into their applications.
You can add paid capabilities to your Azure Active Directory by using the Azure Active Directory Basic, Premium P1, and Premium P2 editions.
Microsoft Azure Advisor
Microsoft’s Azure Advisor will scan the cloud environments and will offer customized or personalized recommendations. This includes the optimization of resources and will also provide the security-based recommendations that are offered by the security center by itself.
Thus, the administrators can review the recommendations directly inside the Azure’s Security Center otherwise, they can check and take the appropriate actions inside the Azure Advisor.
How Azure Security Works?
Microsoft Azure Security architecture has a shared security responsibility paradigm, according to Azure Security literature. This means that security is a shared effort between Azure and customers, with the exception of on-premise environments, where customers are solely responsible.
Some Azure customer security duties are transferred as customers move to the cloud.
This next section of the article shows how the division of duties varies amongst cloud service models:
Azure provides physical security as part of IaaS (infrastructure as a service) (hosts, networks, and datacenter).
Azure takes over physical security and the operating system under PaaS (platform as a service). Customers get access to Azure’s identity and directory infrastructure, network controls, and apps.
Azure takes on more duties in SaaS (software as a service): physical security, operating system, and network.
Microsoft Azure’s Defender Panel
Microsoft’ Azure’s Defender panel comes under the paid subscription of Azure Security Center. It will provide more alerts, threat detection, vulnerability assessments, just-in-time(JIT) access, and much more.
The pricing option is flexible for the administrators, which permits them to choose appropriate resources, and then the organization has to only pay for the resources for which they want to secure.
The regulatory compliance will always provide recommendations depending upon the most common compliance standards according to the industry standards.
Microsoft Azure’s Security Alerts
In Azure’s cloud environment, the administrators can view the security alerts that are generated by the Security Center. Every alert will have a description along with the current level status and the severity level. This will help the administrators to check the impact and check how urgent it is to take action.
Next, in the “Take Action Tab” section, the administrators will notice a list of recommendations for mitigating the threats and preventing future attacks depending upon the most popular recommendations provided by Azure Security Center.
Microsoft Azure’s Security Inventory
This tab provides one more method of viewing the recommendations from the aim of particular Azure and on-premises resources.
Microsoft Azure Active Directory
In Azure, security is all about the management of user access to the organization’s resources, applications, platforms, and portals.
The administrators mainly use the Active Directory service to manage the database of the users in a secured manner.
Windows Azure provides a similar service to keep the users and their passwords secure. Azure’s Active Directory is a core feature that authorizes the administrators to create users, manage their roles, grant access and lastly, delete them.
Reports
Reports are one of the best features in Active Directory. It provides multiple reports like the number of times the user is signing in, whether they are signing in from an unknown device or not. This information is displayed in this section.
Pricing
Microsoft Azure provides two tiers of Security Center to the administrators of the organizations and users. And in this section of the article, we will discuss both tiers. Firstly, we will discuss the free version, which is included with all the Azure services, and it provides the following:
- Continuous Assessment
- Security Score
- Actionable Security Recommendation
Even in the trial version of Azure, the administrators enjoy the benefits from the environment protection along with access to the security center. Azure’s Security Center Free Tier version disables the Azure Defender by default.
Secondly, the paid version of the Security Center will provide its core feature such as Azure Defender. This provides administrators with some great capabilities such as:
- Hybrid security
- Protection Powers
- Vulnerability Scanning for virtual machines
- Just-In-Time (JIT) access for virtual machines and much more.
Azure Security Best Practices
Security tips and recommended practices are also available in the Azure Security documentation. Below are some key pointers to help the users get started:
- Upgrade to Azure Security Center Standard to get more features. This includes finding and patching security flaws, detecting threats using analytics and intelligence, and responding quickly to an attack.
- Azure Key Vault is a place where you may store your keys. Passwords, database credentials, and other secrets are all stored in this vault.
- Set up a firewall for web applications.
- Use Azure MFA (Multi-factor Authentication) for administrator accounts, specifically.
- Files on a virtual hard drive can be encrypted.
- Place Azure virtual networks on which you can connect Azure VMs (virtual computers) to other networked devices.
- DDoS (distributed denial of service) assaults can be avoided and mitigated with Azure’s DDoS services.
- Put in place security procedures to avoid abuse. Azure can automatically develop a security policy for each Azure subscription to assist you in getting started.
- Examine the Azure Security Center dashboard regularly. The dashboard gives you a centralized view of your Azure resources and suggests activities to take.
- Role-Based Access Control in Azure Security Center should be used (RBAC). There are five built-in roles (Subscription Owner, Resource Group Owner, Subscription Contributor, Resource Group Contributor, and Reader) as well as two unique security roles (Subscription Contributor, Resource Group Contributor, and Reader) (Security Administrator and Security Reader). Permissions for these roles vary.
Conclusion
Finally, we learned about the security service offered by Microsoft Azure. We hope you enjoyed this article too as our previous articles.
You give me 15 seconds I promise you best tutorials
Please share your happy experience on Google