Azure Multi-Factor Authentication
Free AWS Course for AWS Certified Cloud Practitioner (CLF-C01) Start Now!!
FREE Online Courses: Transform Your Career – Enroll for Free!
As we all know, multifactor authentication techniques are the new trends and provide better security. And in today’s article, we will have a look at it. But we will see Multifactor authentication in Azure. Let us begin.
What is Multi-Factor Authentication in Azure?
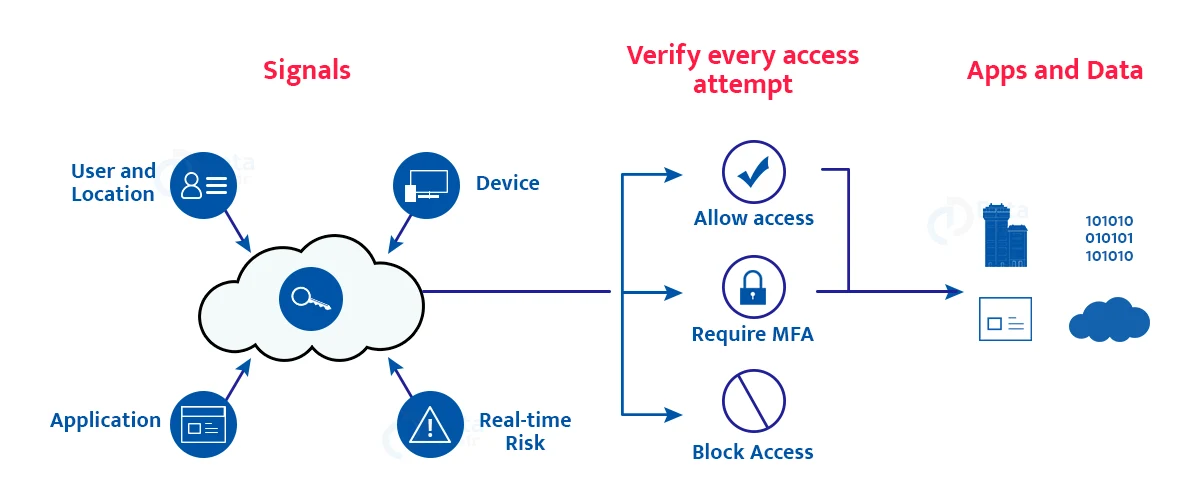
Multi-factor authentication is a method in which users are asked for an additional form of identity during the sign-in process, such as a code on their phone or a fingerprint scan.
When you merely utilize a password to authenticate a user, you’re leaving an attack vector open. An attacker could use the password to obtain access if it is weak or has been disclosed elsewhere.
When the second form of authentication is required, security is enhanced since the additional element is difficult for an attacker to get or reproduce.
Multiple authentication methods are required for Azure AD Multi-Factor Authentication to work:
- Something one already knows, like a password.
- Something you have, such as a trusted device that is difficult to duplicate, such as a phone or a hardware key.
- Biometrics, like a fingerprint or a facial scan, is a way to identify who you are.
- Password resets may be made even more secure using Azure AD Multi-Factor Authentication. Users can register for self-service password reset at the same time that they register for Azure AD Multi-Factor Authentication.
Administrators can choose from a variety of secondary authentication methods and design MFA challenges based on their configuration choices.
To use Azure AD Multi-Factor Authentication, you don’t have to update your apps or services.
The verification prompts are part of the Azure AD sign-in process, which requests and handles the MFA challenge automatically when it is required.
How does Multi-Factor Authentication Work in Azure?
MFA operates by requesting extra proof (factors). One-time passwords are one of the most popular MFA elements used by users (OTP). OTPs are four to eight-digit codes sent to you via email, SMS, or a mobile app.
Technology is evolving rapidly!
Stay updated with DataFlair on WhatsApp!!
When using OTPs, a fresh code is created on a regular basis or whenever a request for authentication is made.
The code is created using a seed value supplied to the user when they first register, as well as another component, such as an incrementing counter or a time value.
Available verification Techniques in Azure
Users can select one of their registered sources of additional verification when they check in to an application or service and receive an MFA prompt. Users can change or add verification methods in My Profile.
With Azure AD Multi-Factor Authentication, you can use the following additional types of verification:
- Microsoft Authenticator app
- Windows Hello for Business
- FIDO2 security key
- OATH hardware token (preview)
- OATH software token
- SMS
- Voice call
How to enable and use Azure AD Multi-Factor Authentication?
You can rapidly enable Microsoft Authenticator for all users in Azure AD tenants by using security defaults.
You can use Azure AD Multi-Factor Authentication to require additional verification from users and groups during sign-in.
Conditional Access policies can be used to specify events or applications that need MFA for more granular controls.
When a user is on the corporate network or using a registered device, these policies may allow routine sign-in, but when the user is remote or using a personal device, additional verification factors may be required.
What authentication and verification methods are available in Azure Active Directory?
Because they provide the most secure sign-in experience, Microsoft recommends passwordless authentication techniques like Windows Hello, FIDO2 security keys, and the Microsoft Authenticator app.
Passwords should be replaced or updated with more secure authentication mechanisms, despite the fact that a user can sign in using other standard methods such as a username and password.
When a user registers in Azure AD, Multi-Factor Authentication (MFA) adds an extra layer of security over just using a password.
Additional means of authentication can be requested, such as responding to a push message, entering a code from a software or hardware token, or responding to an SMS or phone call.
We recommend enabling integrated security information registration to facilitate user onboarding and register for both MFA and self-service password reset (SSPR).
We advocate requiring users to register multiple authentication methods for robustness. When a user’s preferred mode of authentication isn’t accessible during sign-in or SSPR, they can choose another method.
Authentication Technique strength and security
Examine the possible authentication techniques before deploying Azure AD Multi-Factor Authentication in your organization.
Choose the approaches that meet or exceed your security, usability, and availability criteria. When feasible, employ the most secure authentication mechanisms available.
The security implications for the various authentication techniques are listed in the table below. In Azure AD, availability refers to the user’s ability to utilize the authentication mechanism, not to the service’s availability:
| Authentication method | Security | Usability | Availability |
| Windows Hello for Business | High Level | High Level | High Level |
| Microsoft Authenticator app | High Level | High Level | High Level |
| FIDO2 security key | High Level | High Level | High Level |
| OATH hardware tokens (preview) | Medium Level | Medium Level | High Level |
| OATH software tokens | Medium Level | Medium Level | High Level |
| SMS | Medium Level | High Level | Medium Level |
| Voice | Medium Level | Medium Level | Medium Level |
| Password | Low Level | High Level | High Level |
How does Every authentication method work in Azure?
Examine the possible authentication techniques before deploying Azure AD Multi-Factor Authentication in your organization.
Choose the approaches that meet or exceed your security, usability, and availability criteria. When feasible, employ the most secure authentication mechanisms available.
The security implications for the various authentication techniques are listed in the table below. In Azure AD, availability refers to the user’s ability to utilize the authentication mechanism, not to the service’s availability:
| Method | Primary authentication | Secondary authentication |
| Windows Hello for Business | Yes | MFA |
| Microsoft Authenticator app | Yes | MFA and SSPR |
| FIDO2 security key | Yes | MFA |
| OATH hardware tokens (preview) | No | MFA and SSPR |
| OATH software tokens | No | MFA and SSPR |
| SMS | Yes | MFA and SSPR |
| Voice call | No | MFA and SSPR |
| Password | Yes |
Benefits of Multi-Factor Authentication
One of the most effective ways to prevent unwanted access to sensitive data is to implement multi-factor authentication throughout an organization’s Internet-facing assets.
When properly configured, multi-factor authentication can be utilized to protect frequently overlooked points of authentication, such as email and business applications.
An attacker can use an exposed email account or a poorly-protected programme to obtain access to additional user information—or, even worse, use the compromise as a “foothold” to escalate privileges and gain superuser access to the entire environment—without this added layer of protection.
When threat actors attempt to authenticate to an account with multi-factor authentication enabled, the targeted employee receives the second authentication factor, which is an often-overlooked benefit of multi-factor authentication.
If the individual has been adequately trained, he or she should be able to spot the breach and report it to his or her security or IT department for resolution and prevention.
Why use multifactor authentication (MFA)?
- It’s safer than using passwords.
- Some multifactor authentication (MFA) methods are more secure than others.
- You are susceptible because of passwords.
Conclusion
Thus, we have reached the final section of the article. And, in this article, we learnt about the Multi-Factor technique along with its information. We hope you liked this article and will continue in further series. Happy Learning.
Did you like this article? If Yes, please give DataFlair 5 Stars on Google