Security Alerts in Azure
Free AWS Course for AWS Certified Cloud Practitioner (CLF-C01) Start Now!!
FREE Online Courses: Elevate Your Skills, Zero Cost Attached - Enroll Now!
In today’s article, we will be talking about Security Reports and Alerts in Azure. Let us begin.
What are Security Alerts and Incidents in Microsoft Defender for Cloud Environment
Defender for Cloud sends out alerts for resources on Azure, on-premises, and in a hybrid cloud environment.
Advanced detections trigger security alerts, which are only available if enhanced security features are activated. As mentioned in Quickstart:
Upgrade, you can upgrade via the Environment settings page.
Enable more advanced security features. There is a free 30-day trial available. See the pricing page for specifics in your preferred currency and according to your location.
What are security alerts and security incidents in Azure?
Defender for Cloud generates alerts when it identifies threats to your resources. Defender for Cloud prioritizes and lists the alerts, as well as the information you’ll need to examine the issue fast.
Defender for Cloud also includes extensive instructions for resolving assaults. Data from alerts are kept for 90 days.
Instead of listing each alert individually, a security incident is a group of related notifications.
Defender for Cloud correlates different alerts and low fidelity signals into security incidents using Cloud smart alert correlation (incidents). Defender for Cloud uses incidents to give you a single view of an attack campaign and all of the alarms associated with it.
This view allows you to see what actions the attacker made and what resources were impacted rapidly.
Responding to Today’s Threats
Over the previous two decades, the danger landscape has shifted dramatically. Previously, businesses only had to worry about individual attackers who were only interested in seeing “what they could do” with their websites.
The attackers of today are far cleverer and more well-organized. They frequently have specific financial and strategic objectives in mind.
They may also have higher resources since they are funded by nation-states or organised crime.
As a result of these shifting realities, the attacker ranks have reached a new level of professionalism. They are no longer interested in defacing websites.
They’re now interested in stealing information, financial accounts, and personal data, which they can exploit to make money on the open market or leverage a specific business, political, or military position.
The attackers that enter networks do harm to infrastructure and people are even more worried than those with a financial goal.
As a result, businesses frequently implement a variety of point solutions aimed at securing the corporate perimeter or endpoints by checking for known attack signatures.
These systems produce a large number of low-fidelity alarms, which must be triaged and investigated by a security analyst.
Because most businesses lack the time and knowledge to respond to these notifications, many go unanswered.
Furthermore, attackers have perfected their techniques to get through many signature-based defenses and adapt to cloud environments.
To more quickly identify emerging risks and accelerate detection and response, new methodologies are required.
Continuous Monitoring and Assessments
Microsoft Defender for Cloud benefits from Microsoft’s security research and data science teams, which are constantly monitoring the threat landscape for changes. The following initiatives are part of this:
Threat intelligence monitoring encompasses methods, indicators, consequences, and actionable advice regarding current and emerging risks.
This information is shared among security professionals, and Microsoft monitors threat intelligence streams from both internal and external sources regularly.
Signal sharing: Insights from Microsoft’s security teams are shared and evaluated across the company’s broad range of cloud and on-premises services, servers, and client endpoint devices.
Microsoft’s security experts will keep an eye on an ongoing collaboration with Microsoft teams working on specific security topics such as forensics and web attack detection.
Algorithms are tested against real consumer data sets, and security researchers collaborate with customers to verify the results. Machine learning algorithms are refined using true and false positives.
These combined efforts result in new and enhanced detections that you may use right now – no action is required on your part.
How does Defender for Cloud detect threats in Azure?
Security researchers at Microsoft are always on the lookout for new threats. We have access to a large amount of telemetry because of our global cloud and on-premises presence.
We can identify new attack patterns and trends across our on-premises consumer and enterprise products, as well as our web services, thanks to our extensive and diverse dataset collection.
As a result, as attackers reveal new and more complex exploits, Defender for Cloud can quickly upgrade its detection algorithms. This method allows you to stay up with a rapidly changing threat environment.
Defender for Cloud collects, analyses, and integrates log data from your Azure resources and the network to detect actual threats and eliminate false positives.
It also integrates with third-party solutions such as firewalls and endpoint protection. To identify risks, Defender for Cloud analyses this data, typically correlating data from several sources.
Advanced security analytics are used in Defender for Cloud, which goes well beyond signature-based techniques.
Big data and machine learning breakthroughs are being used to analyse events across the entire cloud fabric, discovering risks that would be impossible to detect using manual methods and forecasting attack progression.
The following are examples of security analytics:
1. Integrated threat intelligence
Microsoft has a massive amount of threat intelligence from throughout the world. Azure, Microsoft 365, Microsoft CRM Online, Microsoft Dynamics AX, outlook.com, MSN.com, the Microsoft Digital Crimes Unit (DCU), and the Microsoft Security Response Center all provide data (MSRC).
Researchers also get threat intelligence from third-party feeds and information shared by key cloud service providers. This information can be used by Microsoft Defender for Cloud to warn you about risks from known bad actors.
2. Behavioral Analytics
Behavioral analytics is a method of analyzing and comparing data to a set of predefined patterns. These patterns, however, are not simple signatures.
Complex machine learning methods are used to determine them, and they are applied to enormous datasets.
Expert analysts also use a rigorous examination of malevolent actions to determine them.
Based on a study of virtual machine logs, virtual network device logs, fabric logs, and other sources, Microsoft Defender for Cloud may employ behavioral analytics to identify compromised resources.
3. Anomaly Detection
Anomaly detection is also used by Microsoft Defender for Cloud to identify threats. Anomaly detection is more “personalized” than behavioral analytics, which relies on recognised patterns collected from vast data sets.
It focuses on baselines that are specific to your deployments. Machine learning is used to determine regular behavior for your deployments, after which rules are created to specify outlier conditions that could indicate a security issue.
How are Alerts Classified in Azure?
Defender for Cloud assigns a severity to alerts to help you prioritize the order in which you respond to each warning, so you can respond quickly if a resource is compromised.
The severity is determined by how confident Defender for Cloud is in the discovery of the analytics used to generate the alert, as well as the amount of confidence that the action that triggered the alert has malicious intent.
| Severity | Recommended response |
| High | There’s a good chance your resource has been compromised. You should look into it as soon as possible. Both the malicious intent and the results used to produce the alert have high confidence in Defender for Cloud. For instance, an alert that detects the running of a known malicious instrument like Mimikatz, a popular credential-stealing tool. |
| Medium | This is most likely suspicious behavior that indicates a resource has been hacked. Defender for Cloud has a medium level of confidence in the analysis or discovery, and a medium to a high level of confidence in harmful intent. Machine learning or anomaly-based detections are the most common examples. A sign-in attempt from an unusual place, for example. |
| Low | This could be a harmless positive or a thwarted attack. Defender for Cloud isn’t sure if the aim is malicious, and the action could be harmless. For example, a log clear may occur when an attacker tries to remove their tracks, but it is often a normal process performed by administrators. Unless it’s an unusual circumstance that we recommend you investigate, Defender for Cloud doesn’t normally tell you when attacks were blocked. |
| Informational | An event is often made up of several alerts, some of which may appear to be just informative on their own, but which, when seen in conjunction with the other alerts, may need further investigation. |
Exporting Alerts in Azure
Outside of Defender for Cloud, you can access your alerts in a variety of ways, including:
The alerts dashboard’s Download CSV report allows for a one-time CSV export.
You can configure streams of security alerts and recommendations to Log Analytics workspaces and Event Hubs using continuous export from Environment settings. Continue reading to learn more about continuous export.
Security alerts from Microsoft Defender for Cloud are streamed into Microsoft Sentinel via the Microsoft Sentinel connection.
Cloud Smart Alert Correlation in Azure
Microsoft Defender for Cloud uses advanced analytics and threat intelligence to continuously monitor hybrid cloud workloads and warn you of dangerous activities.
The scope of threat coverage is expanding. The need to detect even the tiniest compromise is critical, and security analysts may find it difficult to sort through the various signals and identify a genuine attack.
Analysts can use Defender for Cloud to assist them to deal with alert fatigue. It assists in the early detection of assaults by connecting several alarms and low-fidelity signals to security problems.
Defenders for Cloud events are powered by fusion analytics, technology and an analytic back end that allows it to connect different warnings and contextual signals.
Fusion examines the various signals reported across all resources for a subscription.
Fusion identifies patterns that suggest assault progression or signals with shared contextual information, indicating that they should be dealt with in a united manner.
Fusion analytics blends security domain expertise with artificial intelligence to assess alarms and identify new threat patterns as they emerge.
The MITRE Attack Matrix is used by Defender for Cloud to correlate warnings with their perceived intent, which aids in the formalization of security domain knowledge.
Defenders for Cloud can also rule out the activity that appears to be steps of an attack but isn’t by using the information obtained for each step of the attack.
Defender for Cloud can integrate AI algorithms to assess attack sequences that are reported on each subscription, which is useful because attacks frequently occur across tenants.
Instead of being coincidentally related to each other, this method recognises the attack sequences as common alert patterns.
The MITRE Attack Matrix is used by Defender for Cloud to correlate warnings with their perceived intent, which aids in the formalization of security domain knowledge.
Defender for Cloud can also rule out an activity that appears to be steps of an attack but isn’t by using the information obtained for each step of the attack.
Analysts frequently require additional information during an event investigation to draw a conclusion about the nature of the danger and how to mitigate it.
It’s tough to know what to do next even when a network anomaly is noticed because you don’t know what else is going on in the network or concerning the targeted resource.
A security incident can contain artifacts, linked events, and information to aid in the investigation.
Depending on the type of threat detected and the setup of your environment, the additional information accessible for security events varies.
Managing Security Alerts in Azure
Below are the steps to manage security alerts in Azure:
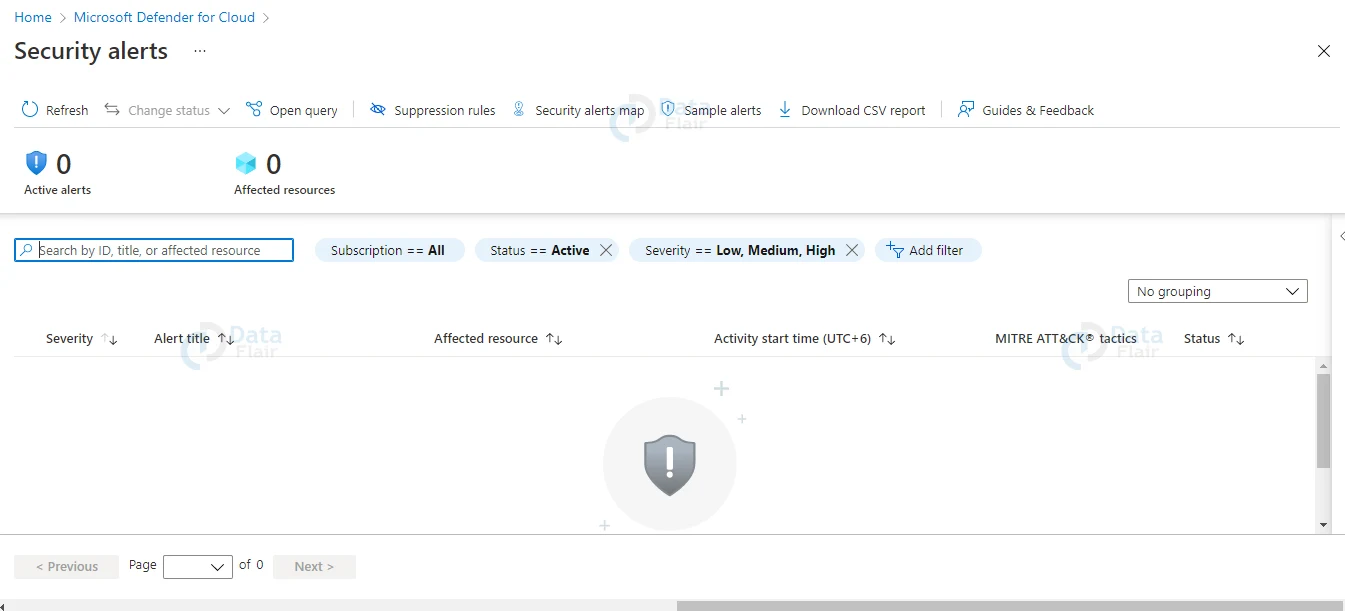
1: Select the Security warnings tile at the top of the page, or the link from the sidebar, from the Defender for Cloud overview page.
The page for security alerts appears.
2: Select any of the relevant filters to filter the notifications list. With the Add filter option, you may choose to add more filters. The list is updated based on the filtering choices you’ve chosen. Filtering can be beneficial.
For example, if you’re investigating a possible system breach, you might want to handle security warnings that have occurred in the recent 24 hours.
Responding to Security Alerts in Azure
Below are the steps to respond security alerts in Azure:
1: Select an alert from the Security alerts list. A side window appears, displaying a description of the warning as well as all of the resources that are affected.
2: Select View complete details for more information.
The security alert page’s left pane displays high-level information about the security alert, such as the title, severity, status, activity time, suspicious activity description, and affected resource.
The Azure tags that are relevant to the resource are displayed beside the impacted resource. When investigating the alert, use these to infer the resource’s organizational context.
The Warning details tab in the right pane contains further information about the alert to help you research the problem, such as IP addresses, files, processes, and more.
The Take action tab is included on the right pane. Use this page to take additional steps in response to the security alert. Taking actions like:
1. Mitigate the Threat
This security alert has manual remedial steps.
2. Prevent Future Attacks
It gives security advice that will help to decrease the attack surface, improve security posture, and ultimately avoid future attacks.
3. Trigger Automated Response
As a response to this security alert, you have the option of triggering a logic app.
4. Suppress Similar Alerts
If the alert isn’t relevant to your organization, you can choose to suppress future notifications with comparable characteristics.
Note: Currently we have no security threats so we are providing the steps.
How to change the status of multiple security alerts at once in Azure?
Checkboxes are included in the alerts list, allowing you to address numerous notifications at once. For example, you might decide to ignore all informational alerts for a given resource for triaging purposes. Below are the steps to change the status of multiple security alerts in Azure:
1: Filter by the alerts you want to deal with in bulk.
2: Pick the alerts to be processed using the checkboxes, or use the checkbox at the top of the list to select them all.
3: Set the required state using the Change status options.
Features of Azure Security
1. Secured Networks
From the user’s perspective, Azure Virtual Network Gateway allows you to create an encrypted IPSec tunnel. Private IPs and IP subnets, which operate as a virtual firewall, can also be used to segment instances within various deployments in a single customer subscription.
2. Key Logs
Microsoft Azure keys are protected by 256-bit AES encryption. You also gain access to the Microsoft Security Vault, which uses FIPS 140-2 Level 2 approved HSMs and allows you to simplify and automate SSL/TLS certificate management processes.
3. Malware Protection
MS Azure security features include several integrated alternatives for malware protection. In the Azure management site, you can enable the antimalware option.
4. Access Management
The Azure Multi-Factor Authentication service from Microsoft can also be used as a standalone server for on-premise connections. Plus, there’s more. To assess Microsoft’s security safeguards, you can conduct your own penetration testing.
Conclusion
Microsoft’s security policies, such as its Security Development Lifecycle, Microsoft Security Response Center, and Microsoft Malware Protection Center, have all been noted to be fairly open.
They’re also willing to go into great detail on reports like the SSAE 16 SOC 2. We’ve compiled a list of MS Azure security features to ensure that migrating to the cloud doesn’t jeopardize your security.
We work very hard to provide you quality material
Could you take 15 seconds and share your happy experience on Google