Computer Network Architecture
FREE Online Courses: Your Passport to Excellence - Start Now
The design and setup of a computer network is called Computer Network Architecture. It is the organization and arrangement of different network devices (i.e., the clients such as PCs, desktops, laptops, mobiles etc.) at both physical and logical levels in order to fulfil the needs of the end user/customer.
The two most well-known Computer Network Architectures are:
- Peer-to-peer Architecture
- Client-Server Architecture
Here is a brief, detailed look at each of the above-mentioned prominent architectures:
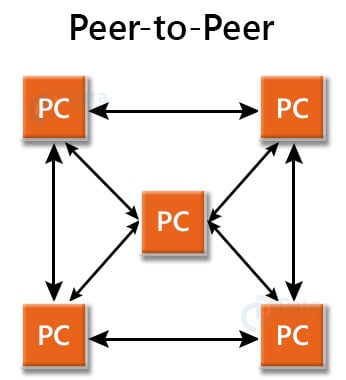
1. Peer-to-Peer:
- The peers referred to here are the individual devices linked together directly, having equal responsibilities and equal powers without the presence of any central authority.
- Due to the absence of a central device in charge of tasks, this architecture is also known as decentralized architecture.
- Each computer has special rights for resource sharing, however this might cause issues if the computer with the resource is unavailable.
- Useful in smaller environments with less number of computers.
Advantages of Peer to Peer Network:
- No particular device is a client or a server, the tasks and responsibilities of servers are distributed among all the devices, which also act as clients.
- Very inexpensive to set up, as there is no requirement of a centralized server, and this also ensures that in case of any failure in the network, all unaffected devices continue to operate normally.
- It’s simple to set up and maintain because each computer runs independently.
Disadvantages of Peer to Peer Network:
- No centralized system, thus difficult to keep a backup of the data in case of any fault.
- It has a security flaw because the computers are self-managed.
- With a growth in the number of machines on this network, performance, security, and access may all become big issues.
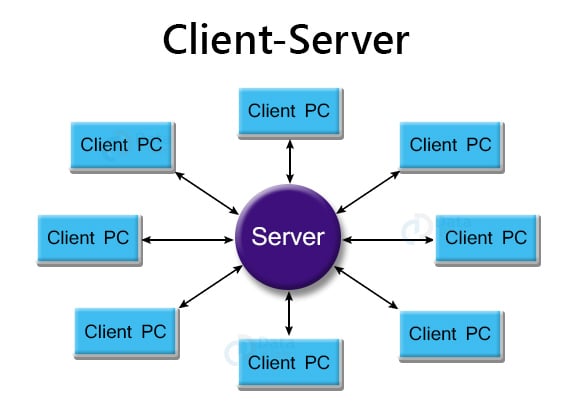
2. Client-Server Architecture:
- This is also known as centralized architecture, as one powerful central computer is in charge of serving all the requests from the client computers. This central computer is a server.
- The client computers connect to the server as and when they require the use of shared resources or shared data. All of the shared data is stored solely in the server, and not on any other computer.
- A server handles all of the key tasks, such as security and network administration.
- All of the clients interact with one another via a server.
Advantages of Client-Server Architecture:
- This type of architecture is much easier to scale since it is much more convenient to add more server computers than configure the network on each and every computer (as is the case in peer-to-peer architecture).
- Much faster network speeds.
- Because a single server manages the shared resources in a Client/Server network, there is improvement in security.
- Backing up data is easy because of the centralized system.
- The server provides a customised Network Operating System (NOS) to offer resources to a large number of users that want them.
Disadvantages of Client-Server Architecture:
- More prone to downtime because if the server fails, none of the client machines are able to get their requests served.
- Requirement of a dedicated network administrator to handle all of the resources.
- It is far more expensive than P2P. This is due to the requirement for a server with more RAM, as well as the necessity for several networking devices such as hubs, routers, switches, and so on.
There are some more lesser-known computer architectures:
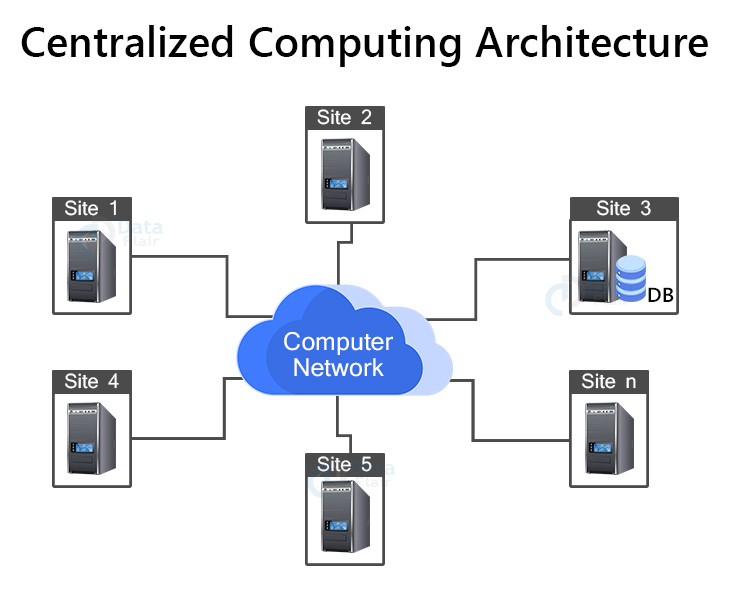
3. Centralized Computing Architecture:
One powerful computer is utilized to service one or more low-powered computers in centralized computing architecture. The nodes under the centralized architecture are not linked; they are only connected to the server.
The centralized computing architecture includes the following components:
- The primary, mainframe computer which handles all processing.
- Terminals are connected to a central computer and function as input/output devices.
- Linking of at least two mainframe computers together via networks. Terminals communicate solely with the mainframe and never with one another.
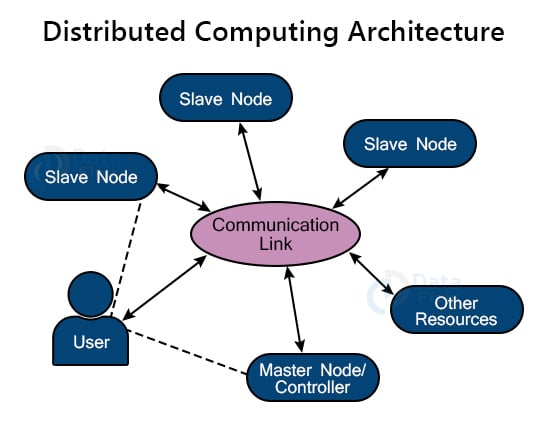
4. Distributed Computing Architecture:
A distributed architecture connects one or more nodes, which are personal computers. It supports a variety of functions, including file sharing, hardware sharing, and network sharing. The nodes in the distributed architecture can manage their own data and rely on the network for administration rather than data processing.
The following components are found in distributed computing architecture:
- Different computers are effective at performing independently.
- Completion of tasks on multiple computers locally.
- Networks enable computers to exchange data and services, but they do not offer processing help.
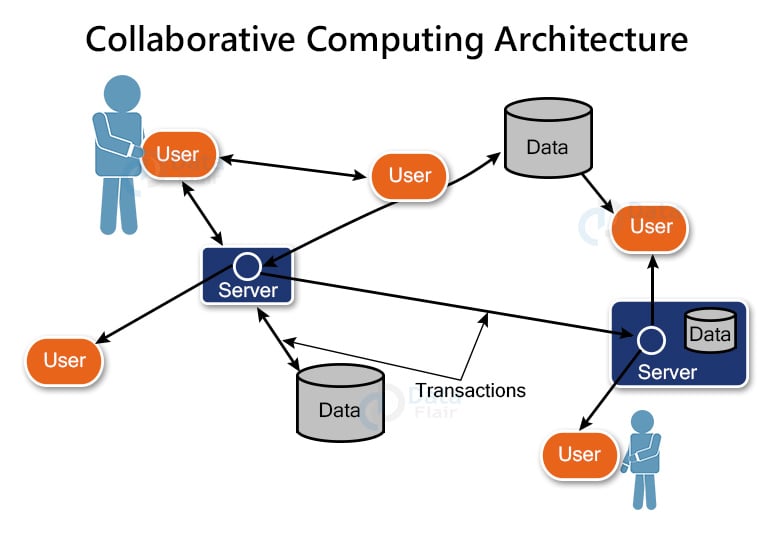
5. Collaborative Computing Architecture:
The collaborative computing architecture is a hybrid of centralised and decentralised computing. Individual members of a network can process their users’ fundamental needs under the collaborative model.
A database server, such as an MSSQL server or an ORACLE server, for example, observes or manages all database-related operations on all network nodes. The model will, however, execute requests that are not from the database.
Summary
In this article, we have discussed the different types of architecture of computer network, such as peer to peer architecture and client-server architecture, along with the advantages and disadvantages of each. We have also discussed some architecture models such as: centralized computing, distributed computing, collaborative computing.
Did you like this article? If Yes, please give DataFlair 5 Stars on Google


Excellent explaination
Well explained! Thanks for the content!!!
Well explained!
Thanks for the content!!!